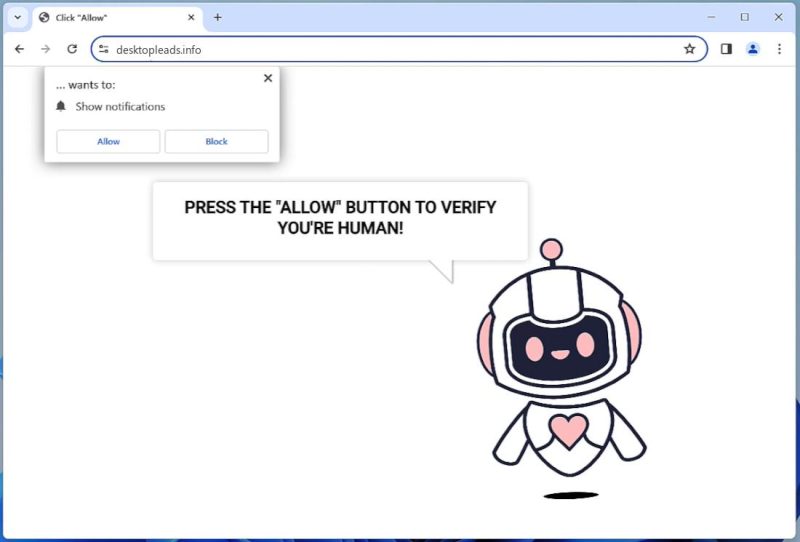
Desktopleads.info is a malicious website known for distributing unwanted software and ads, often referred to as adware. It infects computers primarily through deceptive pop-up ads or potentially unwanted programs (PUPs) that users might inadvertently download. Once in a system, it manipulates browser settings to display intrusive advertisements and redirects users to other suspicious websites. The core aim of such websites is to generate revenue through click fraud or the installation of other potentially harmful software. Desktopleads.info exploits browser notifications by tricking users into allowing push notifications. It often deceives users with misleading prompts like confirming that they are not robots or offering access to adult content. Once users click ‘allow,’ they start receiving unwanted ads even when their browser is closed. The adware can infect all mainstream browsers, including Google Chrome, Mozilla Firefox, and Safari, and is not limited to a specific device, meaning it can affect both Windows and Mac systems.
Author: admin
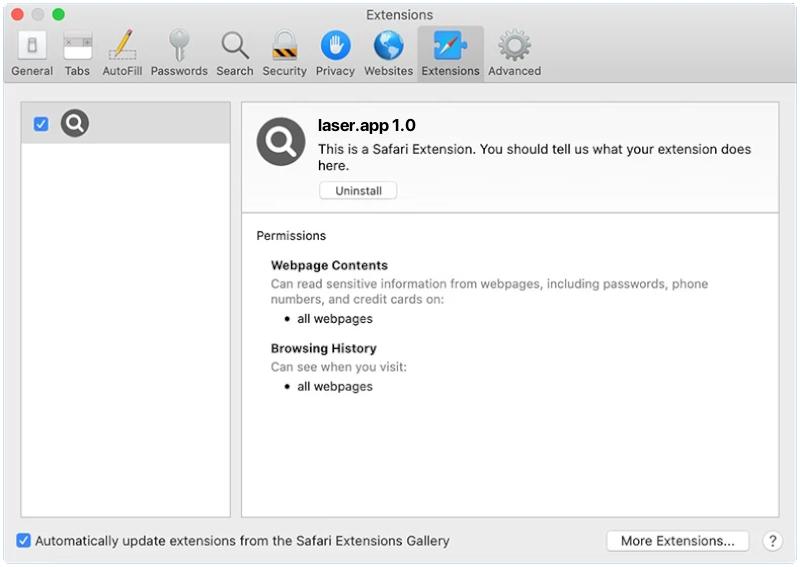
How to remove Laser.app (Mac)
Laser.app is a potentially unwanted program (PUP) that targets Mac users, categorized under the umbrella of adware. It is mainly designed to generate revenue by displaying numerous intrusive advertisements and redirecting users to affiliated or sponsored sites. While it may seem harmless, it can greatly affect your browsing experience due to the constant interruptions. Additionally, Laser.app can also collect personal data, such as browsing habits and history, potentially leading to privacy issues. Laser.app typically infiltrates a Mac system through bundling, a method frequently used by developers of unwanted programs. This method involves hiding the PUP within the ‘Custom’ or ‘Advanced’ settings of the installation processes of other regular applications. Users often rush through these processes, unaware of any additional apps being installed, resulting in the unintentional installation of Laser.app. Other potential methods of infection include clicking on misleading ads, visiting untrustworthy websites, or downloading software from unreliable sources. Therefore, always ensure to follow safe browsing practices and always keep your system updated with a reputable antivirus software.
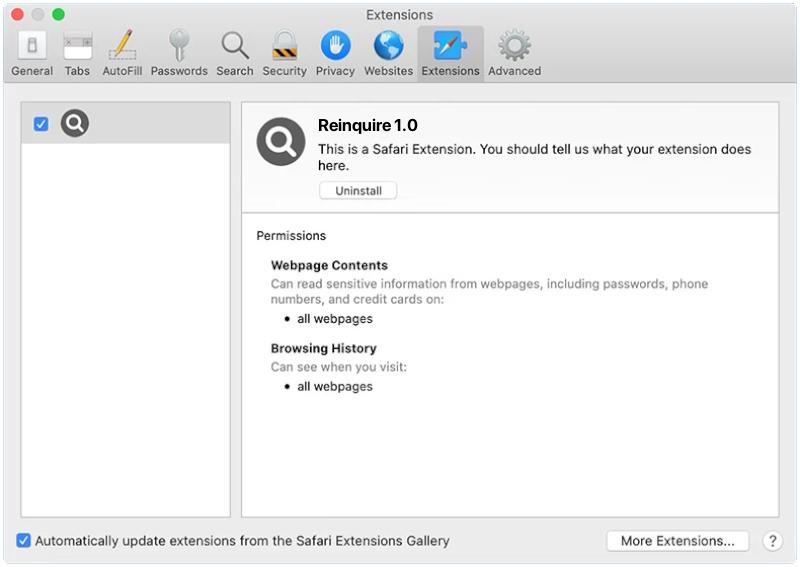
How to remove Reinquire (Mac)
Reinquire is a type of malicious software or malware that targets Mac operating systems. It is primarily classified as adware, which means it infiltrates your system to present you with unwanted advertisements, often in the form of pop-ups, banners, or random page redirects. Reinquire can significantly hamper user experience by slowing down the system, consuming valuable resources and interrupting browsing sessions with constant advertisements. Reinquire typically infects a Mac when users unintentionally download and install it, thinking it’s a useful software or an update. It often comes bundled with free software downloaded from the internet, or users might inadvertently install it when they click on deceptive advertisements or visit compromised websites. Once installed, Reinquire can modify browser settings, track user activities, and gather sensitive data, leading to privacy concerns. Regular system checks and cautious internet browsing habits are key to preventing a Reinquire infection.
How to remove Nano Search
Nano Search is a type of adware, a malicious software program, which is designed to infiltrate computer systems and browsers without the user’s consent. It typically displays unwanted and intrusive advertisements, redirects the user to unfamiliar web pages, and may collect personal data. The main goal of such adware is to generate revenue through pay-per-click activities. It often disguises itself as a legitimate search engine but instead of providing accurate search results, it typically bombards users with ads, sponsored links, and pop-ups. Nano Search adware often infiltrates computers and browsers through deceptive means. It can be bundled with free software or applications that users download from the internet, often without realizing that additional programs are also being installed. Once inside the system, it modifies browser settings, replacing the default homepage and search engine with its own. It may also install additional components or browser extensions to further control the user’s browsing activities. The adware is designed to be difficult to remove, often persisting even after attempts to uninstall it.
How to remove SugarGh0st
SugarGh0st is a type of malicious software, or malware, that can infect computers. It is typically spread through malicious emails, websites, or infected software downloads. Once inside a computer, SugarGh0st can perform a variety of malicious activities such as stealing personal information, tracking user behavior, or causing system damage.
The infection process usually goes as follows:
1. Delivery: The malware is delivered to the victim’s computer through a malicious email attachment, a compromised website, or a malicious software download. The malware may be disguised as a legitimate file or software to trick the user into downloading or opening it.
2. Execution: Once the file is opened or the software is installed, the malware is executed. It may install itself in the system files or registry to maintain persistence, meaning it will continue to operate even if the computer is restarted.
3. Infection: After execution, SugarGh0st starts its malicious activities. It may start collecting personal information, tracking user activity, or damaging system files. It may also try to spread to other computers on the same network.
4. Command and Control: SugarGh0st may also establish a connection with a remote server controlled by the attacker. This allows the attacker to control the infected computer, send commands to the malware, and receive stolen data.
In order to avoid infection by SugarGh0st and other similar malware, it is important to practice safe internet habits, such as not opening suspicious emails, not visiting untrusted websites, and only downloading software from trusted sources. It’s also crucial to keep all software and operating systems up-to-date and to use a reliable antivirus software.
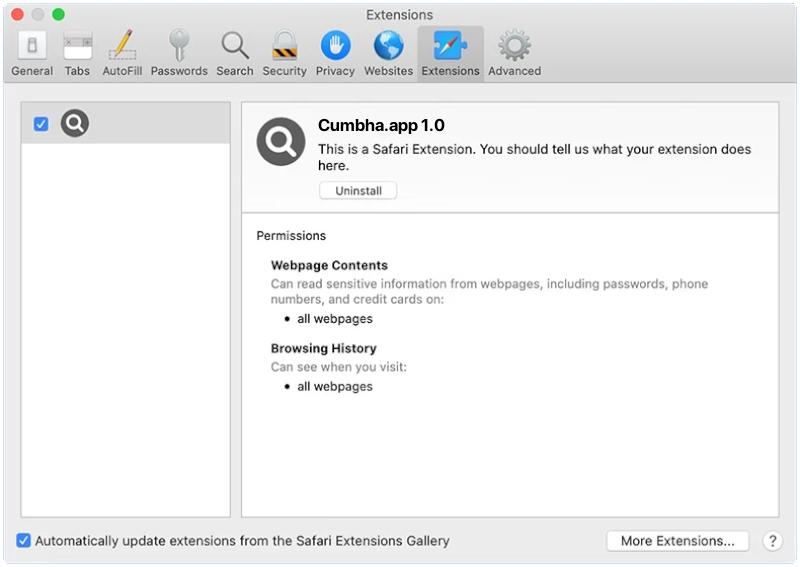
How to remove Cumbha.app (Mac)
Cumbha.app is considered as an unwanted application or potentially unwanted program (PUP) that primarily targets Mac operating systems. It is often classified as adware because of its intrusive advertising activities. It is designed to promote rogue applications, deliver intrusive advertisements, and collect various user data. It is typically spread through dubious software bundles, fake updates, or infected downloads and often gets installed on the system without the user’s explicit permission or knowledge. Once Cumbha.app is installed on a Mac, it can start to display an array of intrusive ads that may include pop-ups, banners, coupons, and other types of advertisements. These ads not only disrupt the user’s browsing experience but also pose a risk to the system’s security as they could potentially lead to malicious websites. In addition to the annoying ads, Cumbha.app also collects different information from the user’s device, including browsing history, search queries, and potentially even personal data. This information can be used for targeted advertising or could be sold to third parties.
How to remove Dragon Search
Dragon Search is a type of adware, a malicious program that is designed to display unwanted ads on a user’s computer, altering the user’s browsing experience. This adware can significantly slow down the computer, cause browser crashes, and even lead to privacy issues. Dragon Search may also redirect users to suspicious websites, which could potentially expose the user to additional malware or viruses. It is typically disguised as a useful tool, promising enhanced search results, but instead, it modifies browser settings without the user’s consent and starts exhibiting intrusive ad activity. Dragon Search adware can infect computers and browsers through various deceptive strategies. One of the most common ways is through bundling; it is packaged with other free software that the user may download from the internet. During the installation process of the downloaded software, the Dragon Search adware is also installed, often without the user’s knowledge. Another method of infection is through malicious email attachments or links. When the user opens the attachment or clicks on the link, the adware is downloaded and installed on the computer. It can also infect browsers by exploiting security loopholes or through malicious websites.
How to remove Pua:Win32/Solvusoft
Pua:Win32/Solvusoft is a potentially unwanted application (PUA) detected by Windows Defender, a built-in anti-malware component of Microsoft Windows. PUAs are not necessarily harmful, but they can engage in annoying or undesirable behaviors, such as displaying unwanted ads or tracking user habits. Pua:Win32/Solvusoft can infect computers through various ways. Here are some common infection methods:
1. Downloading Software: One of the most common ways a computer may end up with Pua:Win32/Solvusoft is through downloading and installing software. PUAs are often bundled with other software, especially freeware or shareware. During installation, the PUA may be installed alongside the desired program without the user’s knowledge.
2. Clicking on Infected Links: If a user clicks on an infected link, they might unknowingly download Pua:Win32/Solvusoft onto their computer.
3. Opening Email Attachments: Opening email attachments from unknown or suspicious sources can also lead to a PUA infection.
4. Browsing Unsafe Websites: Websites that are not secure or contain malicious content can also lead to a PUA infection.
To avoid Pua:Win32/Solvusoft and other PUAs, it can be helpful to only download software from trusted sources, avoid clicking on unknown links, be cautious of email attachments from unknown sources, and use a reliable security program.
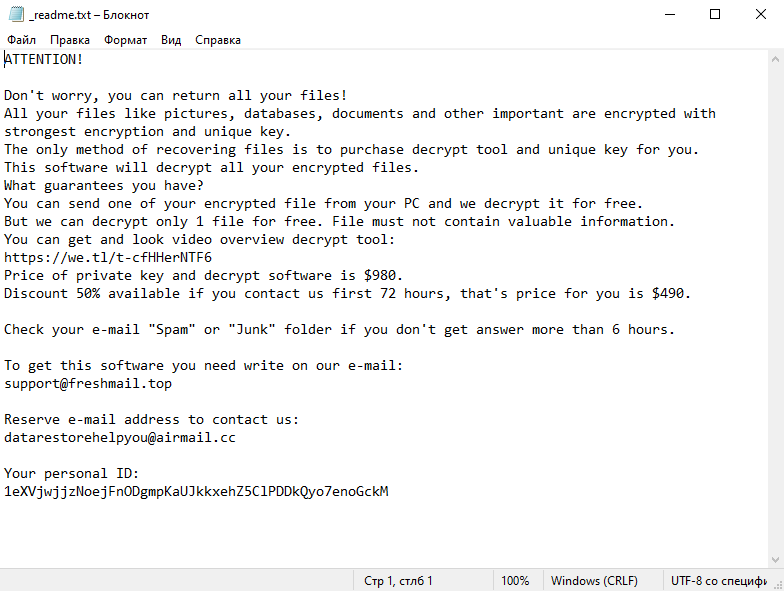
How to remove Ljuy Ransomware and decrypt .ljuy files
Ljuy Ransomware is a type of malicious software that encrypts files on a victim’s computer and demands a ransom for their decryption. Here is some information about the ransomware:
Infection: Ljuy Ransomware can infect computers through various methods, such as malicious email attachments, software vulnerabilities, fake software updates, or by being bundled with other software.
File Extensions: Ljuy Ransomware typically adds a unique extension to each encrypted file. The specific extension may vary, but it often consists of a combination of random characters.
File Encryption: Ljuy Ransomware uses a strong encryption algorithm to encrypt the victim’s files, making them inaccessible without a decryption key. The encryption algorithm may vary depending on the variant of the ransomware.
Ransom Note: Ljuy Ransomware creates a ransom note that usually appears as a text file or an image file. It is often placed in every folder containing encrypted files or displayed on the desktop. The note typically contains instructions on how to pay the ransom and obtain the decryption key.
Decryption Tools: Emsisoft, a cybersecurity company, has developed a tool called “STOP Djvu Decryptor” that can decrypt files encrypted by various variants of Djvu Ransomware, including some variants of Ljuy Ransomware. However, not all variants are decryptable, and it may not work for all cases.
Decrypting Files: If you have been affected by Ljuy Ransomware and your files have been encrypted, you can try using the Emsisoft STOP Djvu Decryptor tool to decrypt your files. However, it is essential to note that this tool may not work for all variants, and it is always recommended to have a backup of your important files to avoid data loss.
Please note that without specific details about the variant of Ljuy Ransomware and its encryption algorithm, it is challenging to provide precise information. It is always recommended to consult with a cybersecurity professional for assistance in dealing with ransomware attacks.
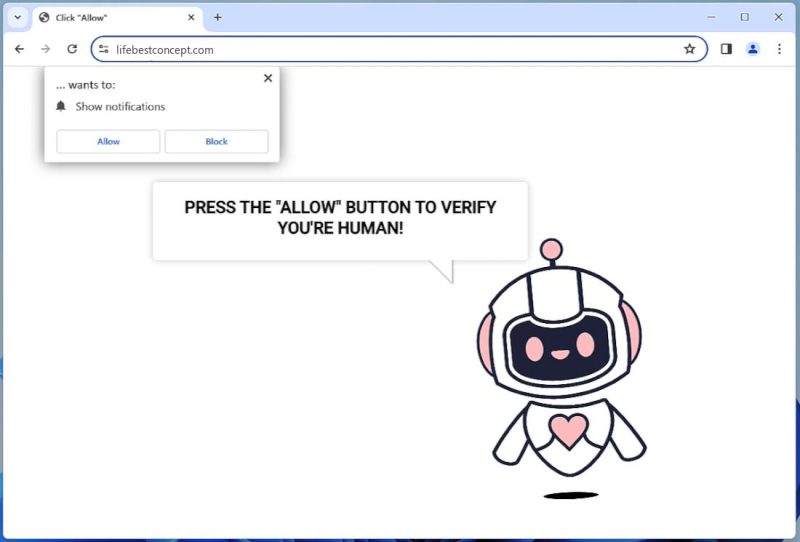
How to remove Lifebestconcept.com
Lifebestconcept.com is a potentially harmful website that employs deceptive tactics to trick users into subscribing to its browser notifications. It manipulates users into clicking the ‘Allow’ button on a prompt to enable push notifications. Once this is done, it sends unrequested ads, links to suspicious websites, prompts for software downloads, and other unwanted content directly to the user’s desktop or browser. This website can also redirect users to other malicious sites that may cause additional harm. It can infect a computer when users inadvertently visit the site, click on a deceptive pop-up ad, or download software from unsecured sources.
This malicious website can affect a wide range of browsers including Google Chrome, Mozilla Firefox, Internet Explorer, Safari, and even Microsoft Edge. It can also infect various devices such as Windows PCs, Mac computers, and mobile devices running on Android or iOS. This is achieved through the use of scripts and codes embedded in the website or through malicious software downloads. The best way to protect against such threats is by keeping software and antivirus protection up-to-date, avoiding suspicious websites, and being vigilant when clicking on ads or downloading software.