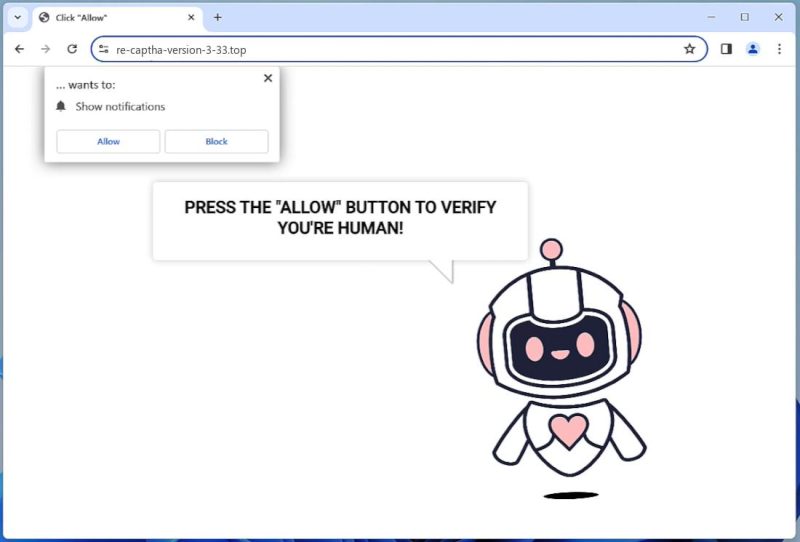
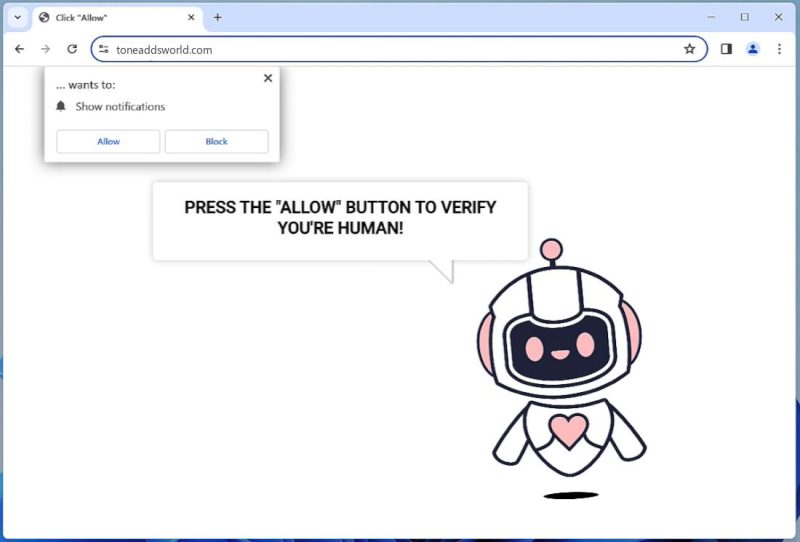
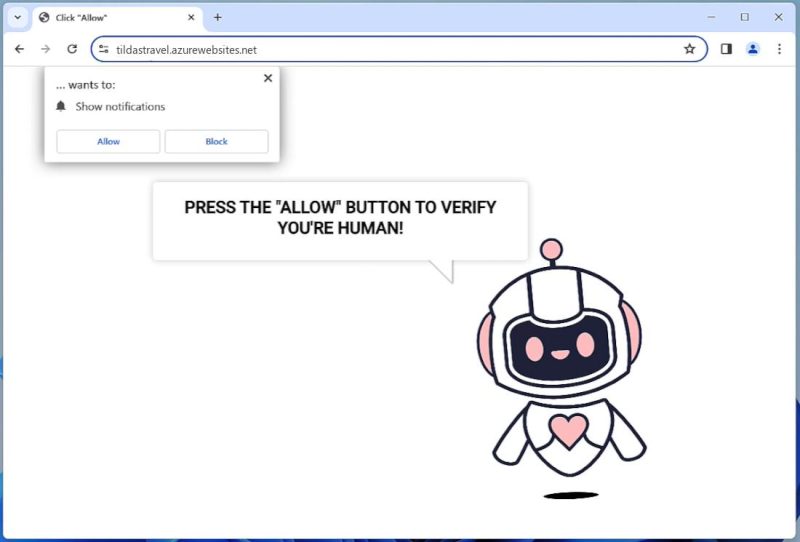
Re-captha-version-3-33.top is an intrusive program often classified as a browser hijacker or adware. It operates by tricking users into allowing push notifications via their internet browsers. The program typically infiltrates computers through bundled software or infected websites that users unknowingly download or visit. Once installed, it begins to display a series of pop-ups, ads, and redirects, essentially hijacking the browser’s functionality. The user is often asked to complete a captcha verification to access content, and once they agree, the site gains permission to send them intrusive notifications.
This deceptive software can affect various browsers, including popular ones like Google Chrome, Mozilla Firefox, and Safari. It can also infect various devices, including PCs, laptops, and even smartphones. The key to its operation is the exploitation of browser notifications, a feature meant to provide convenience to the user. Once the user unintentionally grants permission, the software starts spamming with unwanted ads and notifications, which can lead to potentially harmful websites or download further malware. Therefore, it’s crucial to be vigilant when online and refrain from granting permission to suspicious sites.