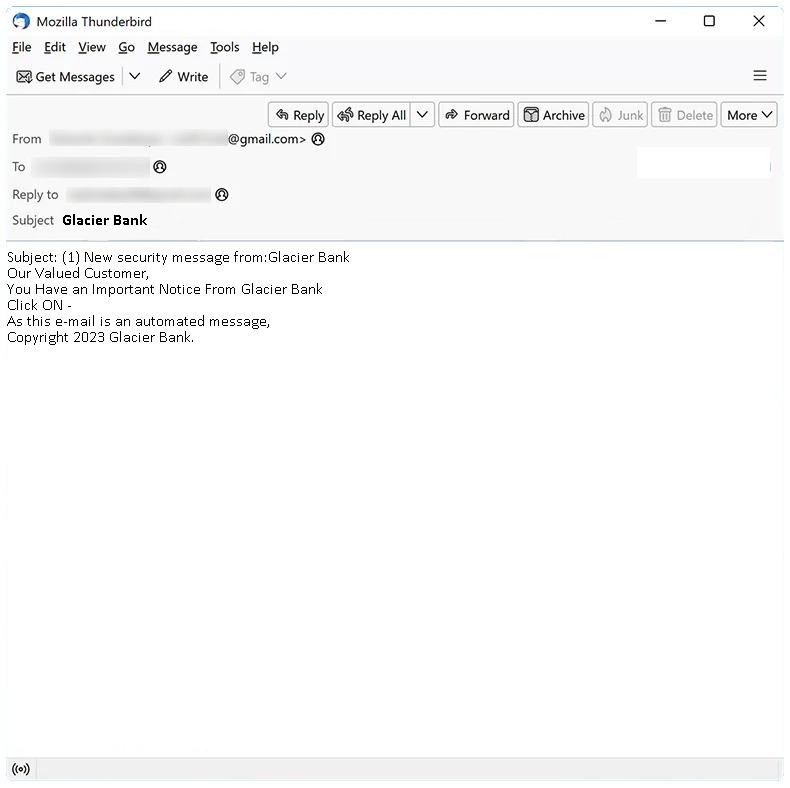
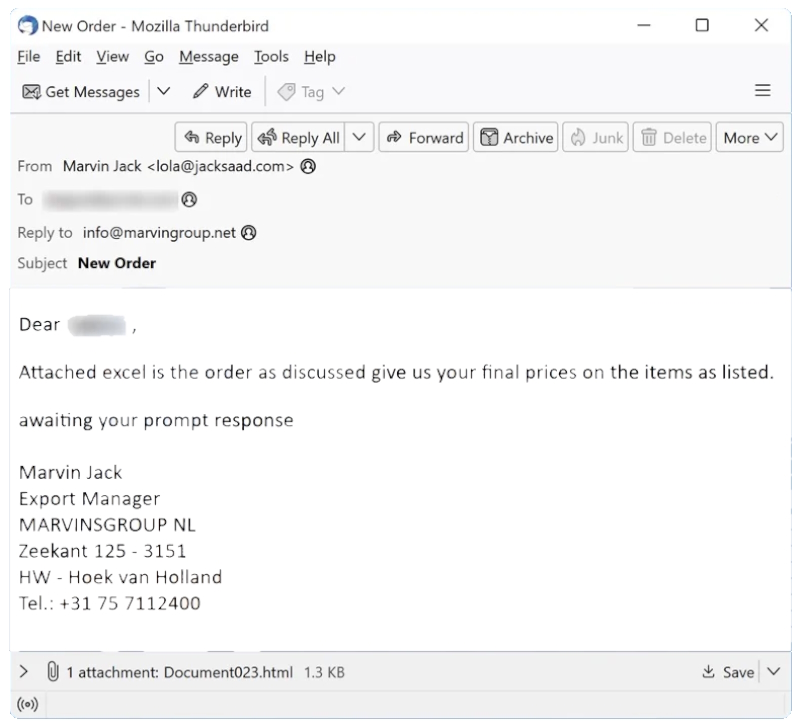
Glacier Bank email spam refers to unsolicited and fraudulent emails sent by cybercriminals, impersonating Glacier Bank, with the intention of deceiving and defrauding recipients. These spam campaigns typically involve phishing attacks, where scammers attempt to trick recipients into providing personal and sensitive information, such as bank account details, login credentials, or credit card information.
There are a few common methods used by Glacier Bank spam campaigns to infect computers:
1. Phishing emails: Cybercriminals send emails appearing to be from Glacier Bank, often with official logos and graphics, asking recipients to click on a link or download an attachment. These links or attachments may contain malware, such as keyloggers or ransomware, which can infect the computer when interacted with.
2. Malicious attachments: Scammers may attach files, such as Word documents or PDFs, to their emails. These attachments may contain malicious macros or scripts that, when opened, can execute code to infect the computer.
3. Fake websites: The email may include a link to a fake Glacier Bank website that closely resembles the legitimate site. Recipients may be tricked into entering their login credentials or personal information on these fraudulent sites, which the scammers can then capture for illegal purposes.
Interacting with Glacier Bank email scams poses several risks, including:
1. Identity theft: Providing personal information, such as social security numbers or bank account details, can lead to identity theft. Scammers can use this information to carry out fraudulent activities or sell it on the dark web.
2. Financial loss: If recipients are tricked into providing their banking information, scammers can gain unauthorized access to their accounts and carry out fraudulent transactions, causing financial loss.
3. Malware infections: Clicking on links or downloading attachments from fraudulent emails can lead to malware infections on the computer. This can result in data loss, system damage, or unauthorized access to personal information.
It is crucial to remain vigilant and skeptical of any unsolicited emails claiming to be from Glacier Bank. To protect yourself, avoid clicking on suspicious links or downloading attachments from unknown sources. Additionally, never provide personal or financial information unless you can verify the authenticity of the email and its sender through official channels, such as contacting Glacier Bank directly through their official website or phone number.
Read more