What is Gusau ransomware Gusau ransomware is a new encoding threat, that will infiltrate victim’s computer by means of spam email attachments, exploits, botnets, fake
Author: admin
How to remove Berosuce Ransomware and decrypt .berosuce files
What is Berosuce ransomware Berosuce is the newest crypto-virus, that is originated from STOP ransomware. Cyber criminals are blackmailing their victims, because Berosuce ransomware will
How to remove Madek Ransomware and decrypt .madek files
What is Madek ransomware Madek ransomware is a virus-encryptor, that uses AES encryption algorithms on user’s files. The list of endangered by Madek ransomware types
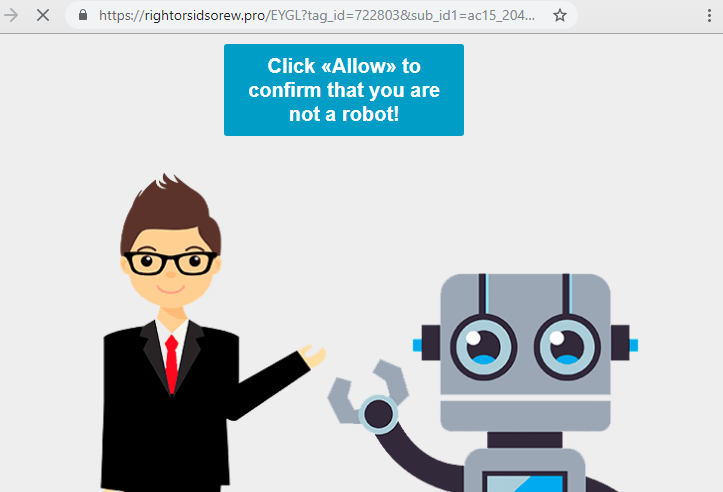
How to remove Rightorsidsorew.pro
What is Rightorsidsorew.pro Rightorsidsorew.pro web page may start to appear in a browser without user’s permission. Such redirections and pop-ups is the result of a
How to remove Heran Ransomware and decrypt .heran files
What is Heran ransomware Heran Ransomware is a dangerous encoding virus. It is able to use advanced encryption algorithms to encipher most types of personal
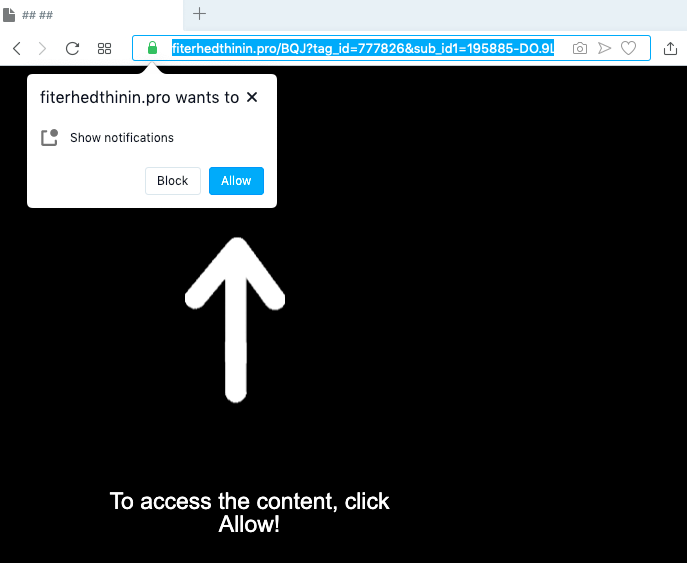
How to remove Fiterhedthinin.pro
What is Fiterhedthinin.pro Fiterhedthinin.pro is a non-trusted web page that may constantly appear in your browser because of an adware infection. The malware in your
How to remove Herad Ransomware and decrypt .herad files
What is Herad ransomware Herad ransomware is a virus, that is created with the purpose of blackmailing people. The main function of Herad ransomware is
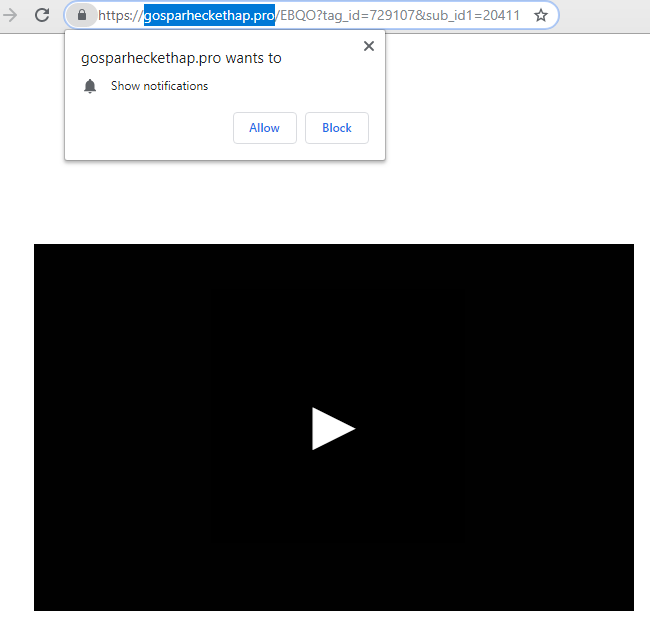
How to remove Gosparheckethap.pro
What is Gosparheckethap.pro If you are experiencing a lot of uncontrollable pop-ups of Gosparheckethap.pro web page, then your computer is infected with adware. This kind
How to remove BoooamCrypt Ransomware and decrypt .boooam@cock_li files
What is BoooamCrypt ransomware BoooamCrypt – is a virus, that is able to lock all the personal and important for any user files. It will
How to remove SkyStars Ransomware and decrypt .SKYSTARS files
What is SkyStars ransomware SkyStars – is a crypto-virus, that will run AES encryption algorithms on infected computer. After this process, a victim of this