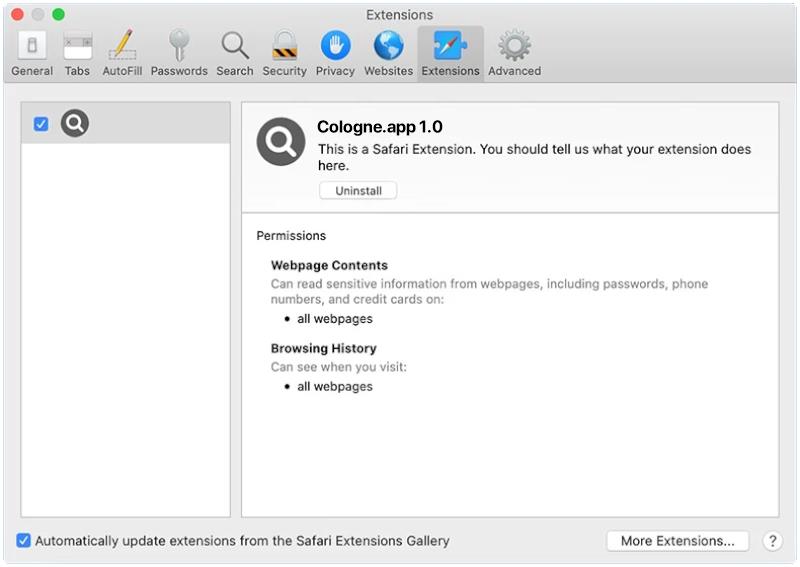
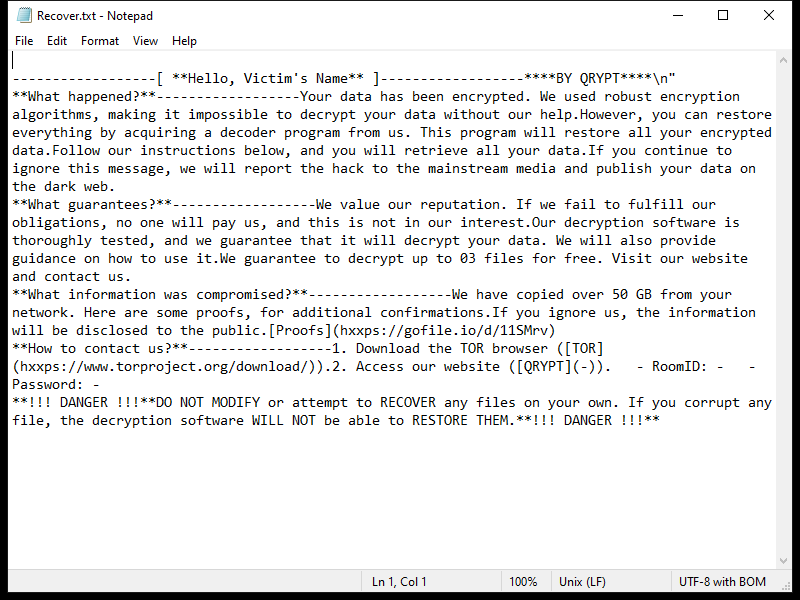
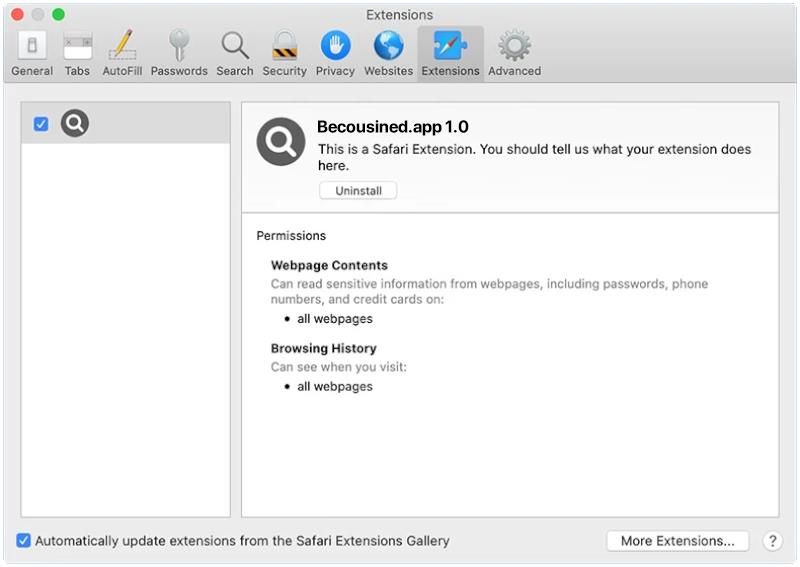
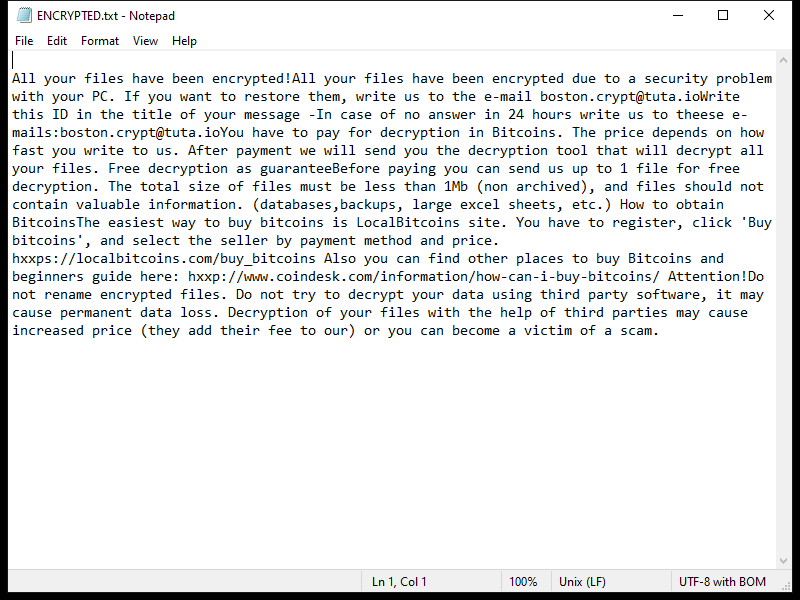
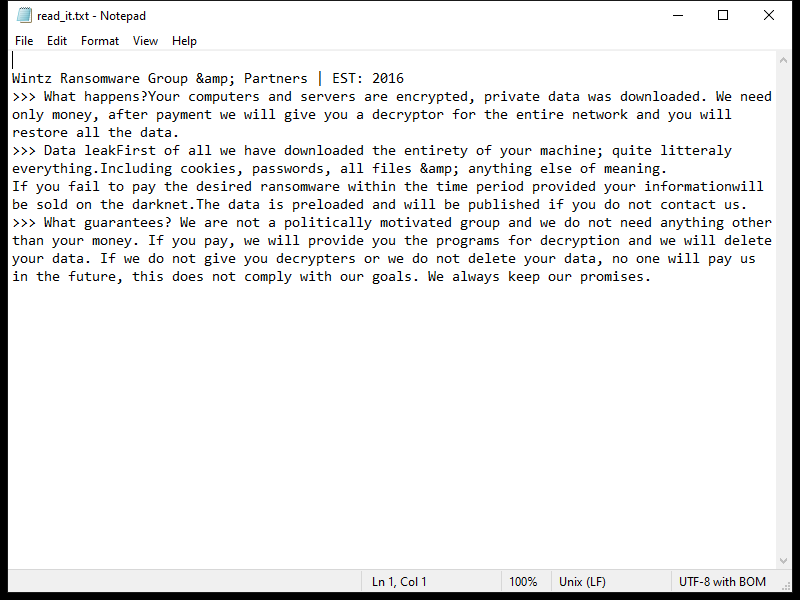
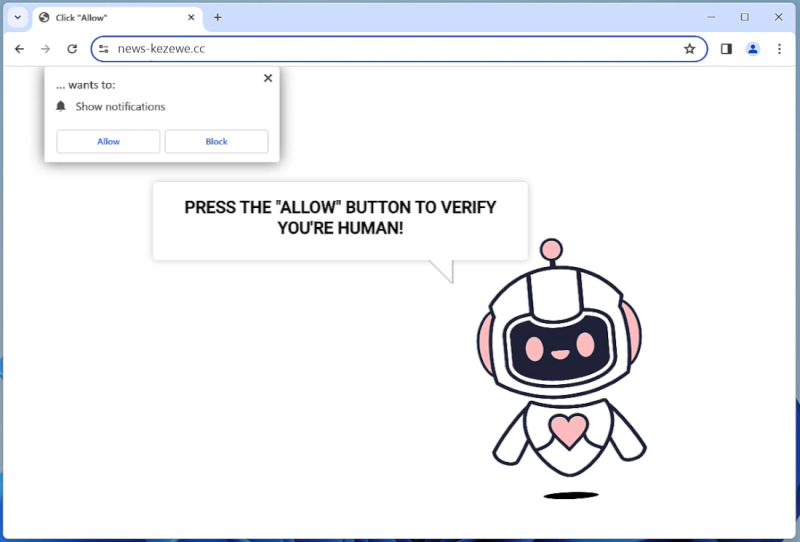
Cologne.app is a type of malicious software that is designed to infect Mac computers. It typically enters a system through deceptive means, such as being bundled with other software downloads or disguised as a legitimate application. Once installed on a Mac, Cologne.app can cause a variety of issues, including slowing down the system, displaying unwanted pop-up ads, and collecting personal information without the user’s consent.
Cologne.app infects Mac computers by exploiting vulnerabilities in the operating system or by tricking users into downloading and installing it themselves. It may also spread through malicious websites or email attachments. Once installed, Cologne.app can be difficult to remove and may require the use of specialized anti-malware software to fully eliminate it from the system. It is important for Mac users to be cautious when downloading software from the internet and to regularly update their system to protect against potential malware threats like Cologne.app.