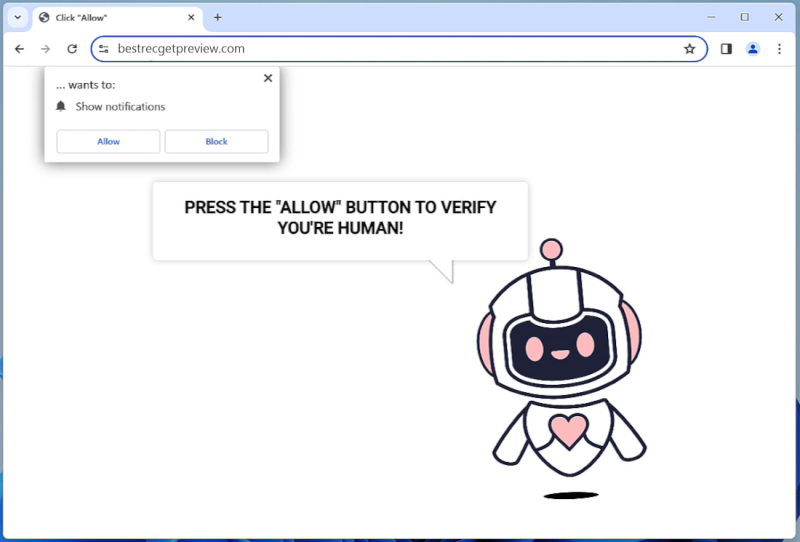
Bestrecgetpreview.com is a malicious website that is known for infecting computers with adware and potentially unwanted programs (PUPs). It usually infiltrates systems through software bundling, where it is included as an optional installation alongside legitimate software. Once installed, it bombards users with intrusive pop-up ads and redirects them to other malicious websites.
One of the tactics used by Bestrecgetpreview.com to exploit users is through browser notifications. It tricks users into allowing notifications by displaying fake alerts or prompts that claim to be necessary for accessing content or downloading files. Once granted permission, the website starts sending unwanted notifications, which can lead to further infections or privacy breaches. Bestrecgetpreview.com mainly targets popular web browsers such as Google Chrome, Mozilla Firefox, and Microsoft Edge, and can infect devices running various operating systems, including Windows, macOS, and Android. Users are advised to be cautious while browsing the internet and to avoid interacting with suspicious websites to prevent infections by Bestrecgetpreview.com and other similar threats.