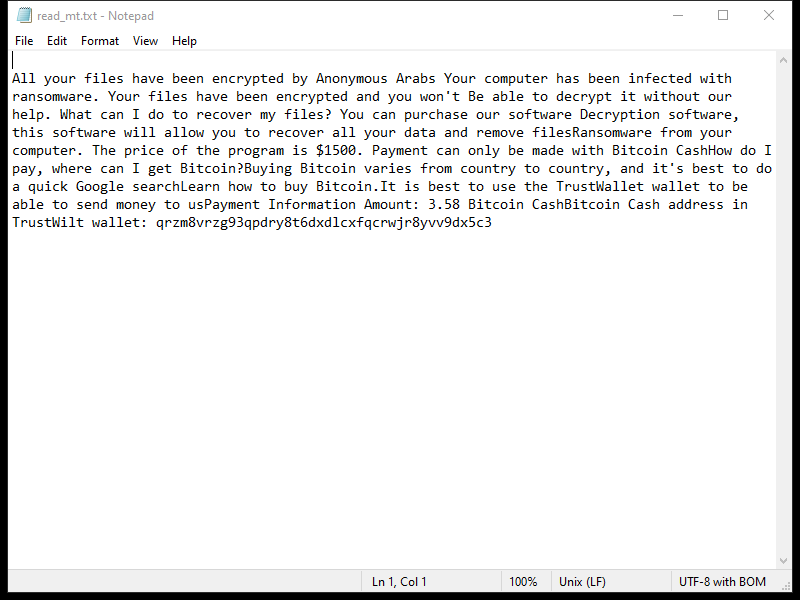
Rafel RAT is a remote access tool (RAT) that is commonly used by cybercriminals to gain unauthorized access to Android devices. This malicious software allows attackers to remotely control the infected device, steal sensitive information, and perform various malicious activities without the user’s knowledge. Rafel RAT can be installed on Android devices through various means, such as malicious email attachments, fake app downloads, or exploiting vulnerabilities in the device’s operating system.
Once installed on an Android device, Rafel RAT can remain hidden from the user and silently carry out its malicious activities. The RAT can access the device’s microphone and camera to eavesdrop on conversations and capture images, as well as track the user’s location using GPS data. Additionally, Rafel RAT can intercept SMS messages, steal login credentials, and remotely control the device to perform actions like sending text messages or making calls without the user’s consent. It is essential for Android users to be cautious when downloading apps or clicking on links to prevent their devices from becoming infected with Rafel RAT and other types of malware.