ZHO Ransomware is a type of malware that encrypts files on a victim’s computer and demands a ransom in order to decrypt them. It typically infects computers through malicious email attachments, fake software updates, or exploit kits.
Once a computer is infected, ZHO Ransomware adds a unique file extension to the encrypted files, making them inaccessible to the user. The specific file extension used by ZHO Ransomware may vary.
ZHO Ransomware uses strong encryption algorithms such as AES or RSA to encrypt the victim’s files, making it difficult to decrypt them without the decryption key.
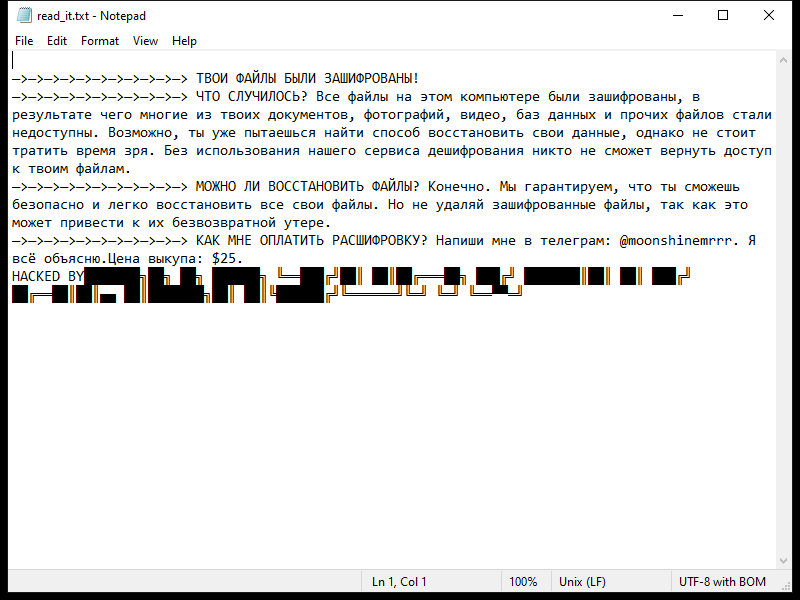
After encrypting the files, ZHO Ransomware typically creates a ransom note on the victim’s desktop or in each folder containing encrypted files. The ransom note usually contains instructions on how to pay the ransom in exchange for the decryption key.
As of now, there are no decryption tools available for ZHO Ransomware. However, it is important not to pay the ransom as there is no guarantee that the cybercriminals will provide the decryption key or that it will work properly.
If you have been affected by ZHO Ransomware, it is recommended to regularly back up your files, remove the malware from your computer using reputable antivirus software, and seek assistance from a professional cybersecurity expert to try and decrypt your files.