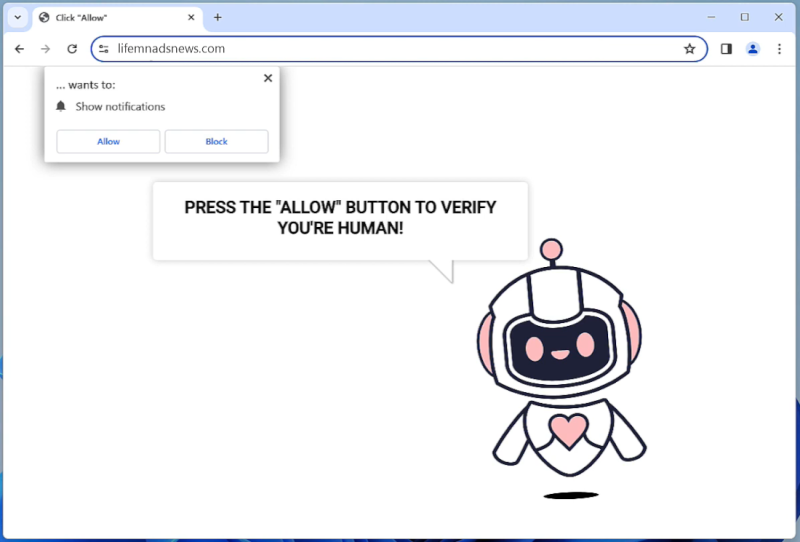
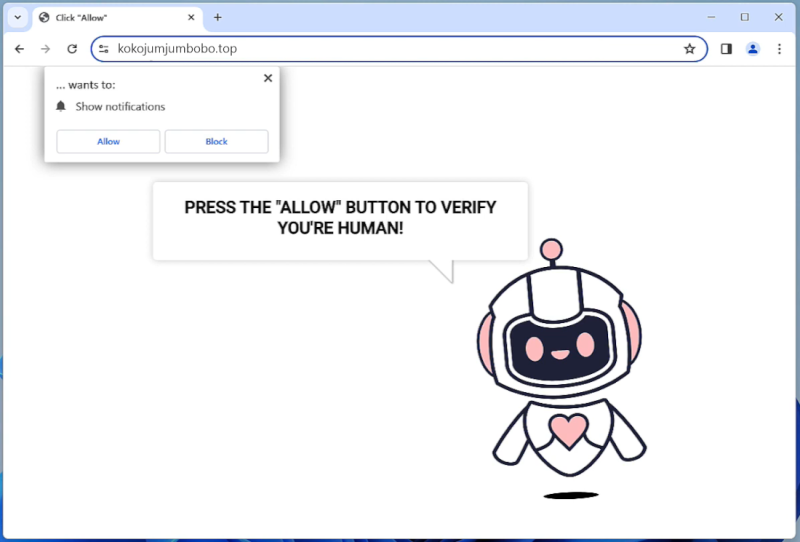
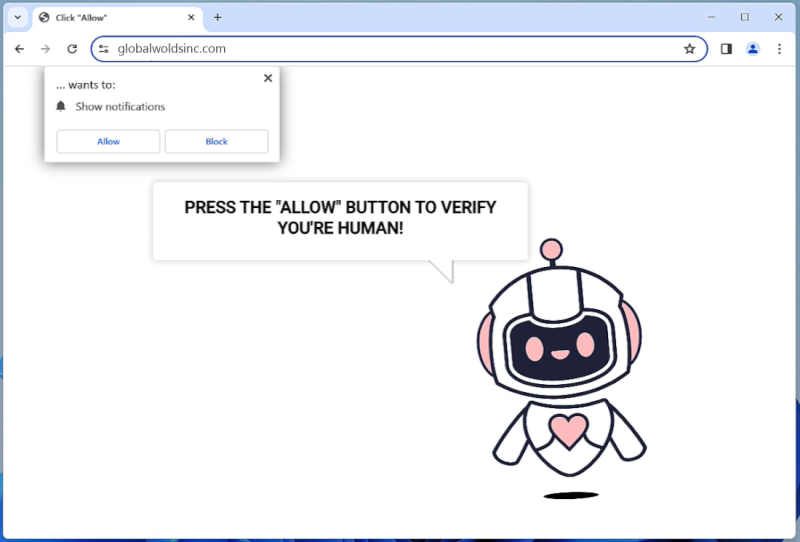
Lifemnadsnews.com is a malicious website that infects computers by tricking users into allowing browser notifications. When users visit the website, they are prompted to click on a button that claims to be necessary to access the content. However, by clicking on this button, users unknowingly give permission for Lifemnadsnews.com to send them unwanted notifications.
Once granted permission, Lifemnadsnews.com exploits browser notifications by sending pop-up messages that contain advertisements, fake alerts, or links to malicious websites. These notifications can be very intrusive and disruptive, making it difficult for users to browse the internet without being bombarded by unwanted content. Lifemnadsnews.com can infect all major web browsers, including Chrome, Firefox, and Safari, as well as various devices such as desktop computers, laptops, and mobile devices. It is important for users to be cautious when visiting unfamiliar websites and always be wary of granting permissions for browser notifications to prevent infections like Lifemnadsnews.com.