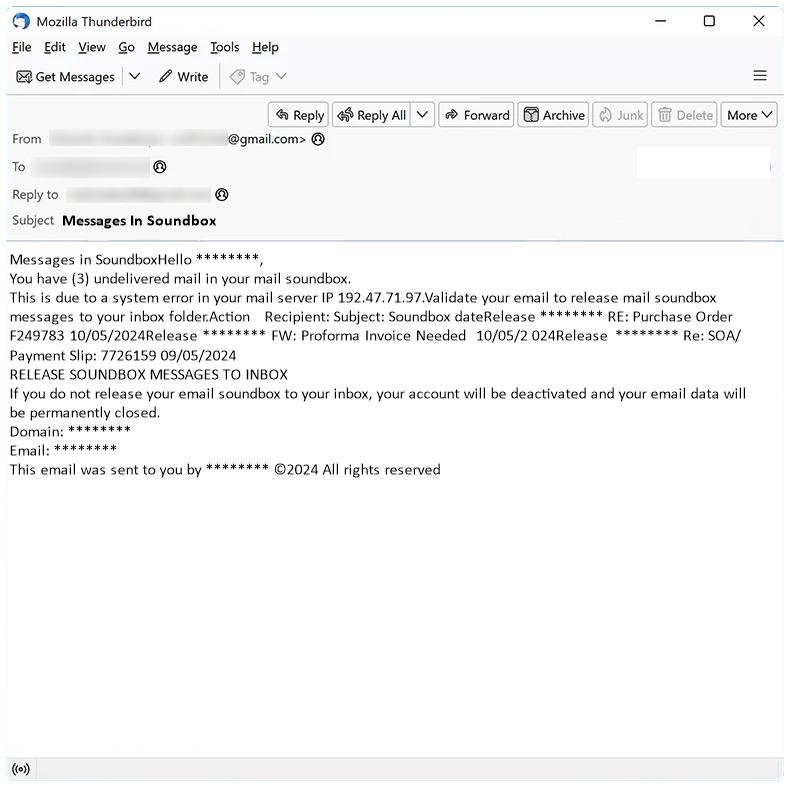
Messages In Soundbox email spam is a type of scam email that tries to trick recipients into clicking on malicious links or downloading harmful attachments. These emails may appear to be from a legitimate company or organization, but they are actually designed to steal personal information or infect computers with malware.
Messages In Soundbox spam campaigns can infect computers in several ways, including through malicious email attachments, phishing links, or by tricking users into entering personal information on fake websites. Once a computer is infected, the malware can steal sensitive data, track online activities, or even take control of the machine.
Interacting with Messages In Soundbox email scams can pose several risks, including:
1. Identity theft: Scammers may use the information collected from infected computers to steal identities, open fraudulent accounts, or commit other types of financial fraud.
2. Financial loss: Malware installed through Messages In Soundbox spam campaigns can allow cybercriminals to access bank accounts, credit card information, and other sensitive financial data.
3. Data loss: Some malware can encrypt files on infected computers and demand payment for decryption, leading to potential data loss if the ransom is not paid.
4. Compromised security: Once a computer is infected, cybercriminals may be able to access other devices on the same network, compromising the security of personal and sensitive information.
To protect against Messages In Soundbox email spam and other types of phishing scams, it is important to be cautious when opening emails from unknown senders, avoid clicking on suspicious links or downloading attachments from untrusted sources, and regularly update antivirus software to detect and remove malicious threats.
Read more