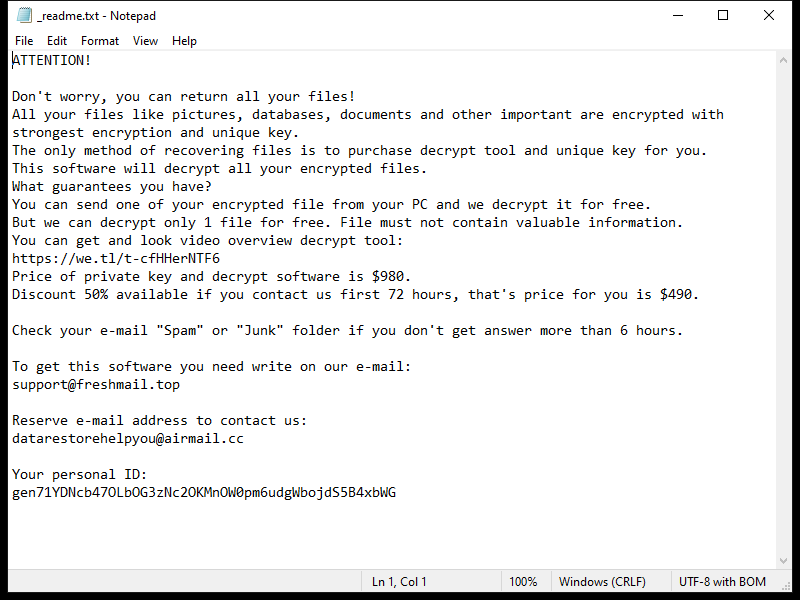
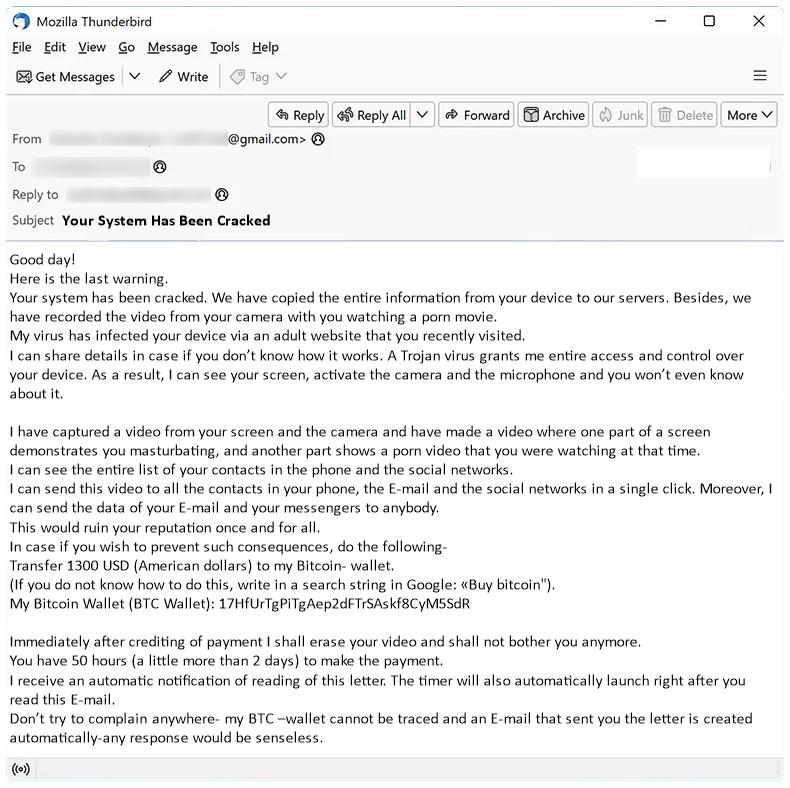
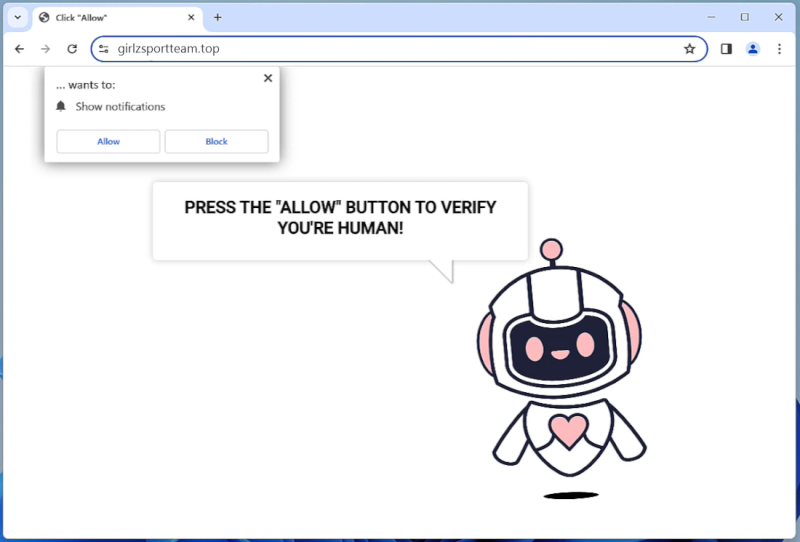
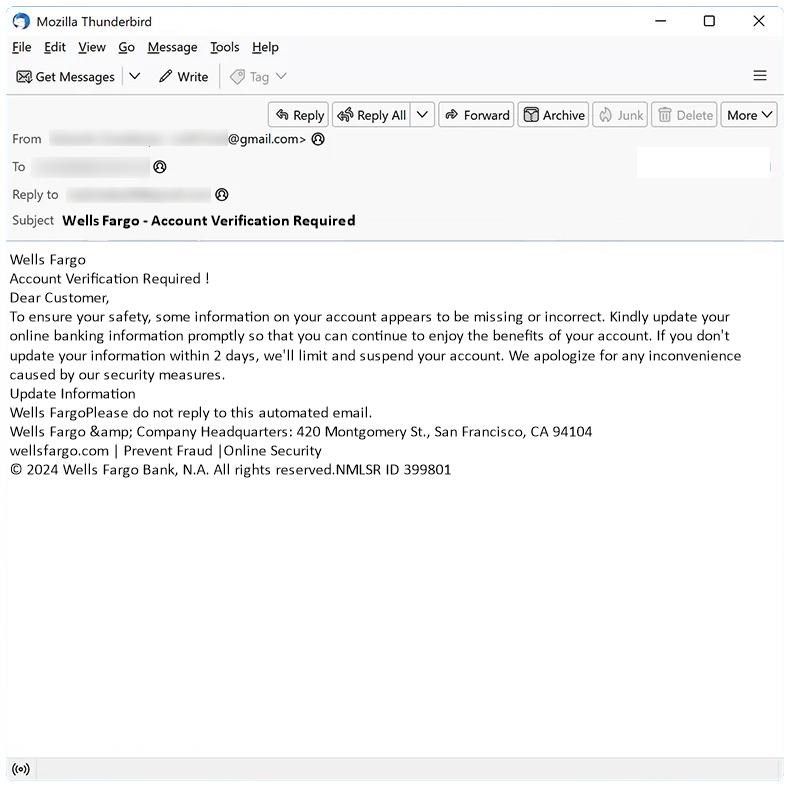
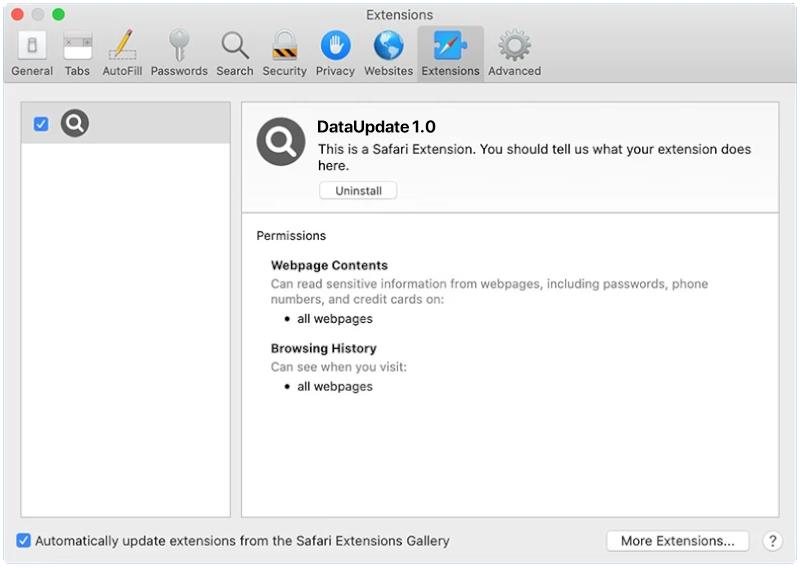
Error In Your IMAP/POP3 Mails Server is a common issue that occurs when there is a problem with the configuration or connectivity of the email server. IMAP (Internet Message Access Protocol) and POP3 (Post Office Protocol version 3) are protocols used for retrieving emails from a mail server. When there is an error in the IMAP/POP3 server, users may experience issues accessing their emails, sending messages, or syncing their mailboxes.
This error can appear in browsers when a user tries to access their email account through a web-based email client. The browser displays a message indicating that there is an issue with the IMAP/POP3 mail server, which prevents the user from accessing their emails. Common causes of this error include incorrect server settings, network issues, server downtime, or security restrictions. Users may need to troubleshoot the problem by checking their email settings, ensuring that their internet connection is stable, or contacting their email service provider for assistance.