DHL Lottery is a scam that involves sending fraudulent emails or pop-up notifications claiming that the recipient has won a lottery organized by DHL, a reputable international shipping company. The scammers typically ask for personal information or payment in order to claim the prize, but in reality, there is no legitimate lottery and the victims end up losing money or having their personal information stolen.
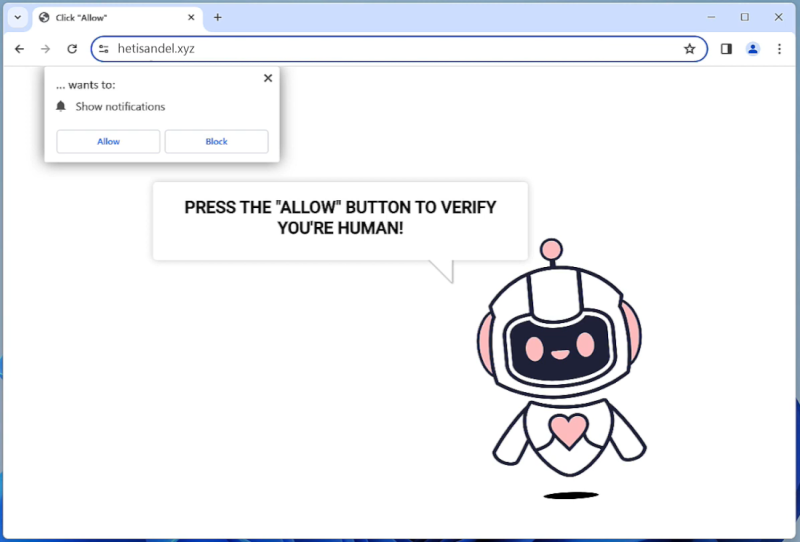
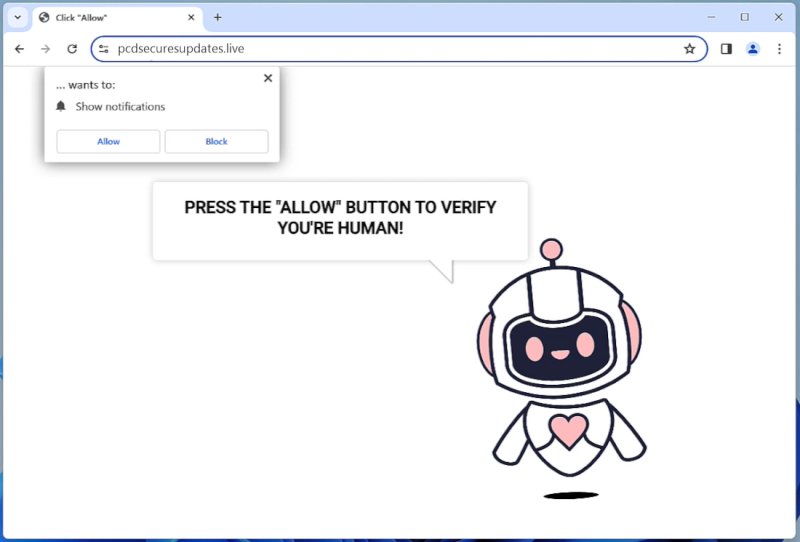
When DHL Lottery appears in browsers, it is usually due to malicious software or adware that has infected the device. These programs can cause pop-up notifications or redirect users to fake websites claiming to be affiliated with DHL in order to trick them into providing personal information or making payments. It is important to be cautious when encountering these types of notifications and to never provide personal information or payment details to unknown sources.