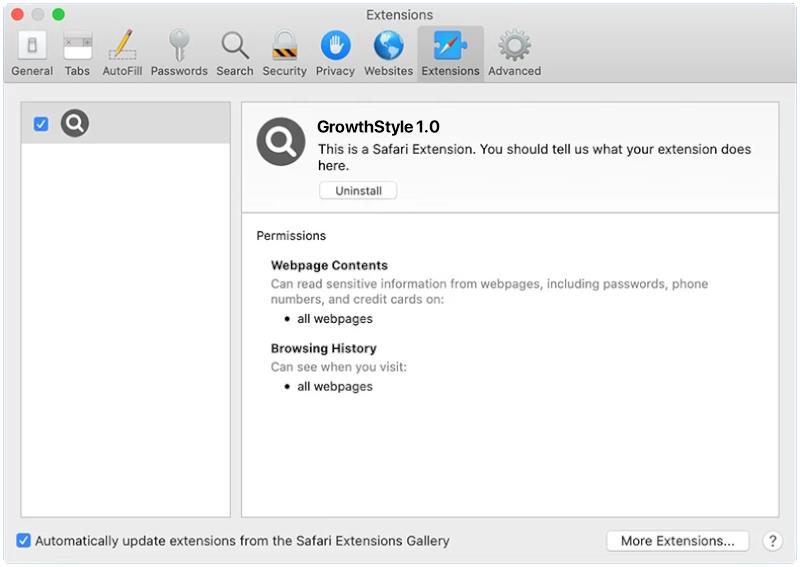
GrowthStyle is a type of adware that infects Mac computers by injecting unwanted advertisements and pop-ups into the user’s web browsing experience. This adware typically sneaks onto a user’s computer through bundled software installations or malicious websites, and once installed, it starts displaying various ads, banners, and sponsored links on the affected system. These ads can be quite intrusive and disruptive, making it difficult for the user to browse the internet without being constantly bombarded with unwanted content.
In addition to displaying ads, GrowthStyle may also track the user’s online activities and collect sensitive information such as browsing history, search queries, and personal data. This information can be used for targeted advertising or sold to third parties, putting the user’s privacy and security at risk. To remove GrowthStyle from a Mac computer, users can try running a reputable anti-malware program or manually delete the adware by locating and deleting its files and directories. It is important to regularly update security software and practice safe browsing habits to prevent future infections by adware like GrowthStyle.