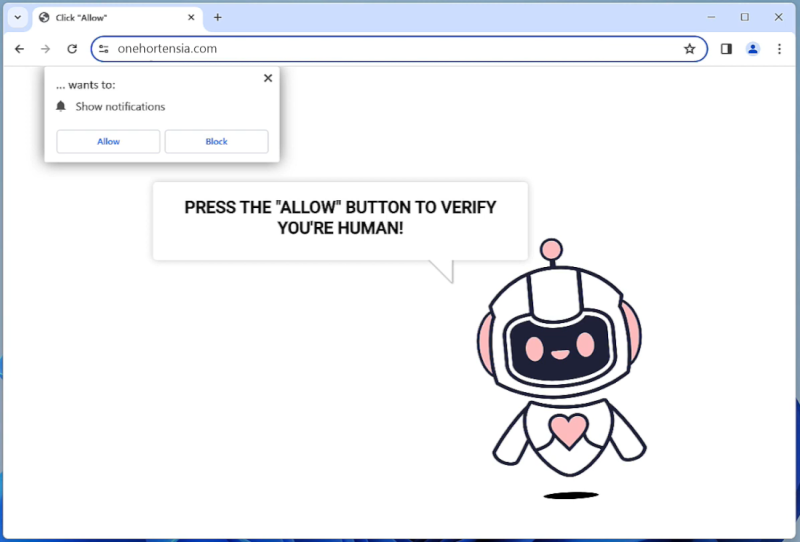
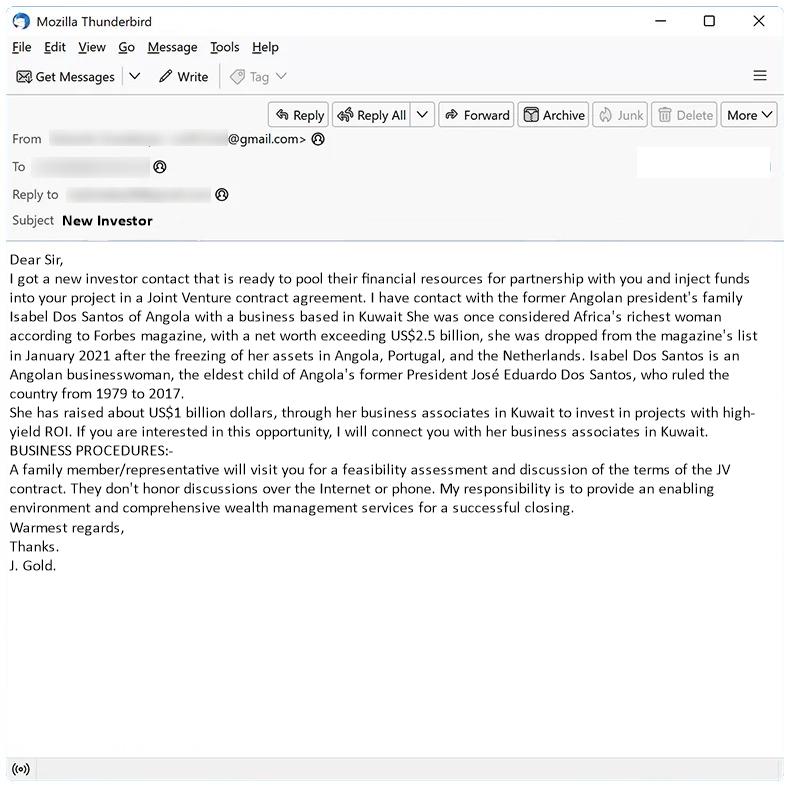
Onehortensia.com is a malicious website known for infecting computers with adware and potentially unwanted programs. It typically tricks users into visiting the site through misleading advertisements or by redirecting them from other websites. Once a user lands on Onehortensia.com, the site may display fake alerts or pop-ups claiming that the user’s device is infected with a virus, prompting them to download a fake antivirus software or click on malicious links.
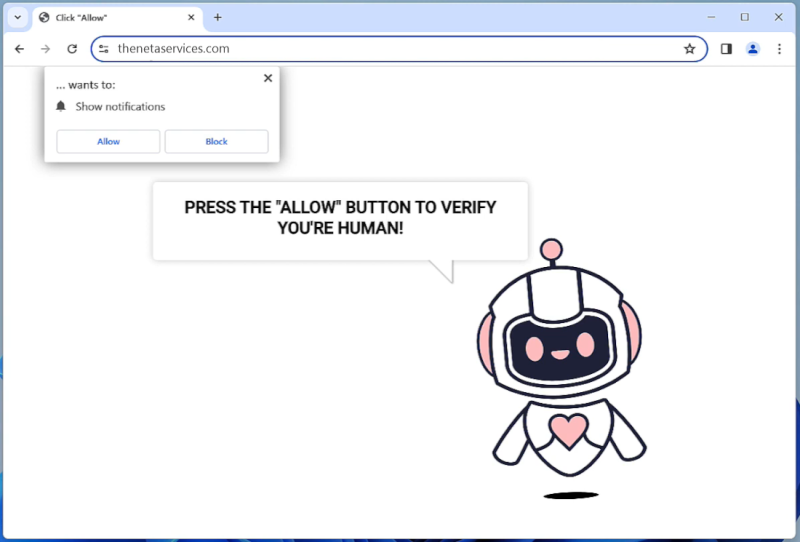
Onehortensia.com can exploit browser notifications by prompting users to allow notifications from the site. If users grant permission, they may start receiving unwanted pop-up notifications even when they are not actively browsing the site. These notifications can contain advertisements, fake alerts, or links to malicious websites. Onehortensia.com primarily targets popular browsers such as Google Chrome, Mozilla Firefox, and Microsoft Edge, and can infect devices running on Windows, Mac, Android, or iOS operating systems. Users are advised to avoid visiting suspicious websites and be cautious about granting permissions to notifications from unknown sources to prevent infections by Onehortensia.com.