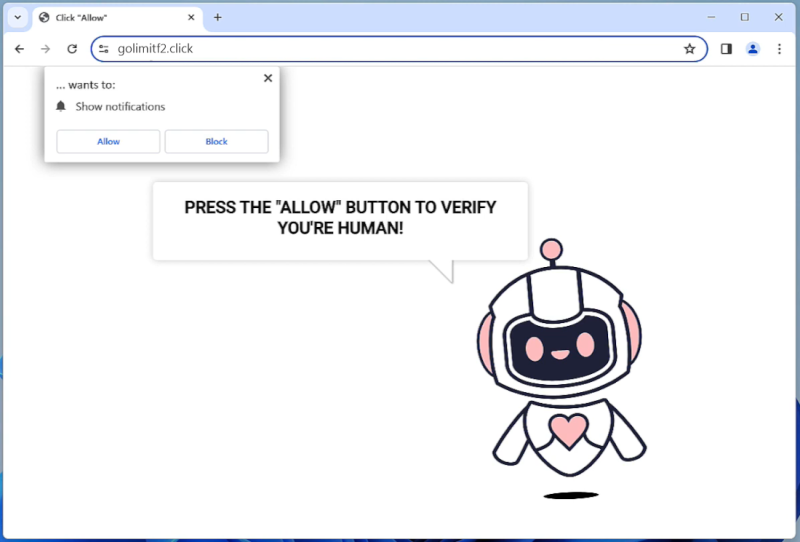
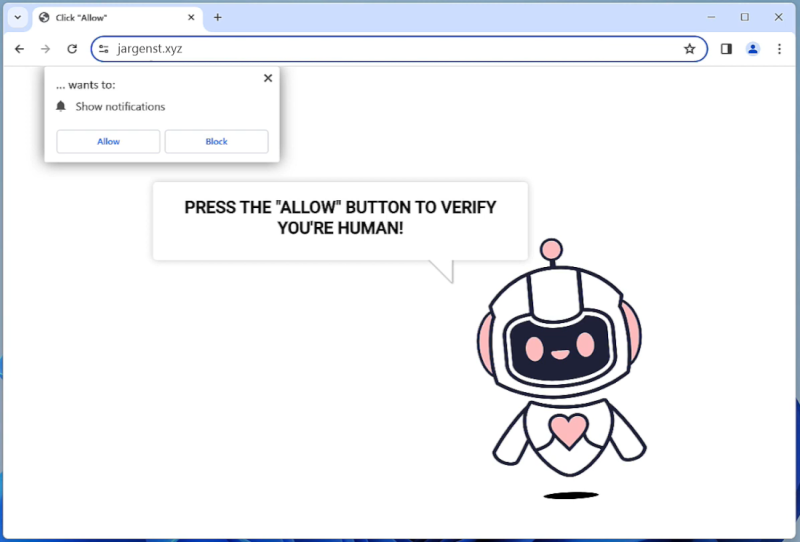
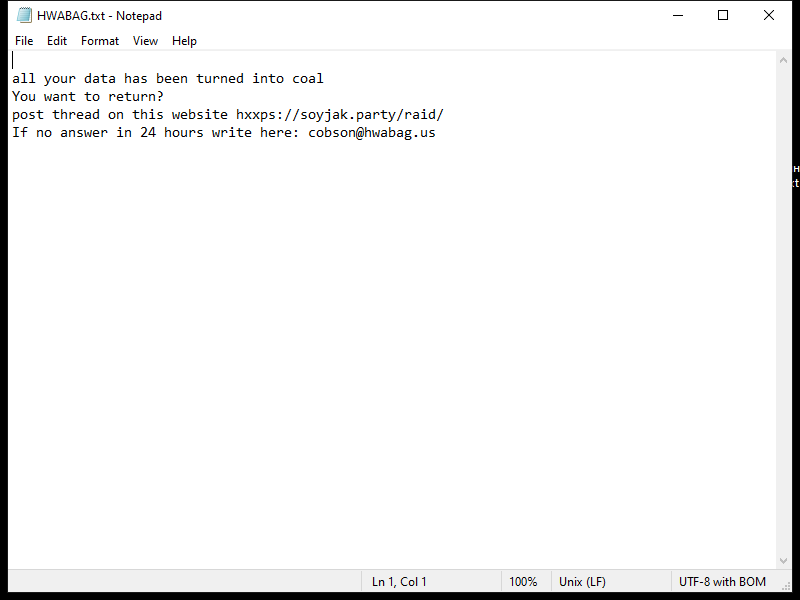
Bitcoin L2 Restaking refers to the process of staking or locking up Bitcoin on Layer 2 solutions, such as the Lightning Network, in order to earn rewards or fees. By staking their Bitcoin on Layer 2, users can contribute to the security and scalability of the network while also potentially earning passive income in the form of additional Bitcoin. This process is similar to staking on other blockchain networks, where users lock up their cryptocurrency to support network operations and receive rewards in return.
Bitcoin L2 Restaking may appear in browsers as a way for users to easily access and participate in staking opportunities on Layer 2 solutions. By integrating staking functionalities into web browsers, users can conveniently stake their Bitcoin without having to use separate wallets or platforms. This ease of access can help increase participation in Bitcoin L2 Restaking and further strengthen the security and efficiency of Layer 2 networks. Additionally, browsers may also provide users with information and updates on their staking rewards and performance, making it easier for users to track their staking activities.