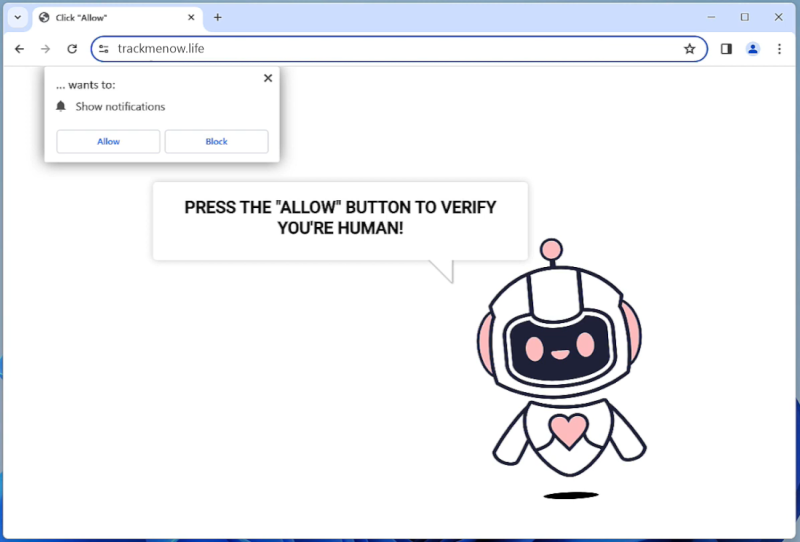
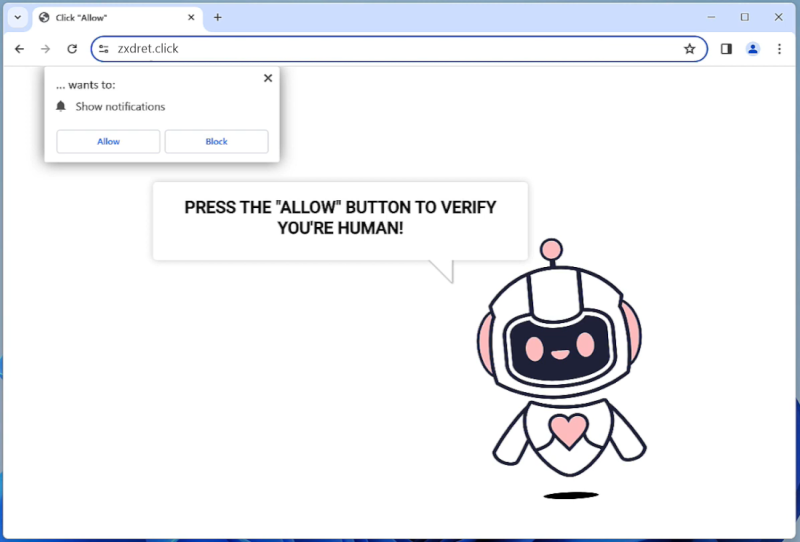
Seekatonce.com is a type of adware that displays intrusive advertisements, pop-ups, and banners on web browsers. It can also redirect users to sponsored websites and collect browsing data to target users with more personalized ads. Seekatonce.com adware can slow down the performance of the infected computer and disrupt the browsing experience.
Seekatonce.com typically infects computers through software bundling, where the adware is included in free software downloads. Users unknowingly install the adware along with the desired program, allowing Seekatonce.com to take over their browser settings. Additionally, clicking on malicious links or visiting compromised websites can also lead to the infiltration of Seekatonce.com adware. Once installed, Seekatonce.com can be difficult to remove and may require the use of anti-malware tools to completely eradicate it from the system.