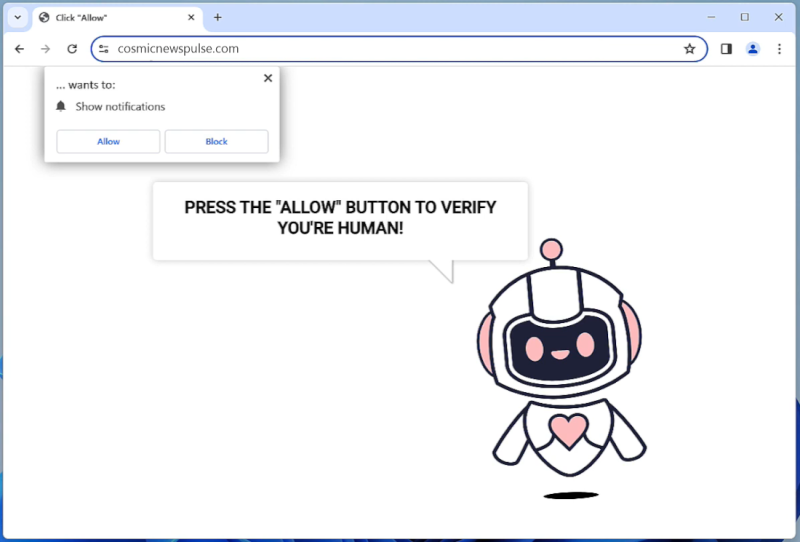
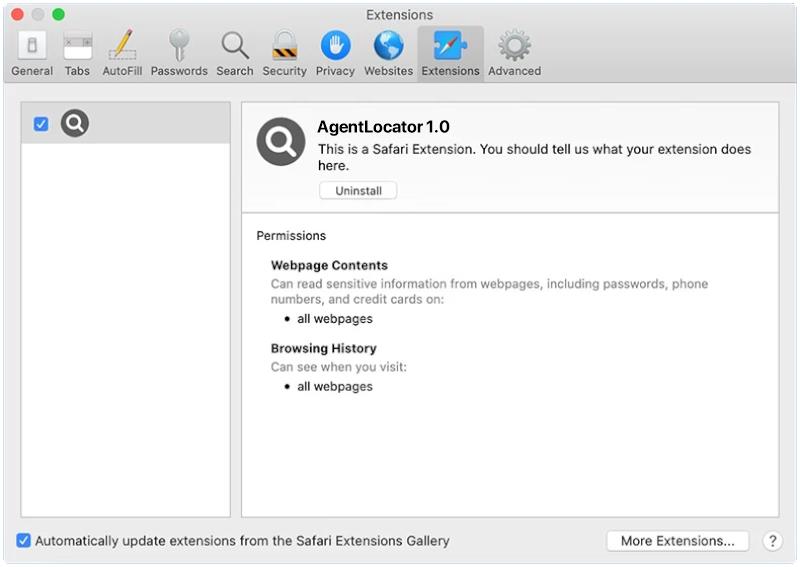
XploitSPY Malware is a type of malicious software that is designed to secretly infiltrate Android devices in order to steal sensitive information and spy on the device’s user. This malware is often distributed through malicious websites, email attachments, or fake apps, and once it infects a device, it can run in the background without the user’s knowledge. XploitSPY Malware is capable of logging keystrokes, capturing screenshots, recording audio and video, and accessing personal data such as passwords, financial information, and personal messages.
One common way that XploitSPY Malware infects Android devices is through phishing attacks, where users are tricked into clicking on a malicious link or downloading a fake app. Once the malware is installed on the device, it can exploit vulnerabilities in the Android operating system to gain access to sensitive information. Additionally, XploitSPY Malware can also spread through infected USB drives, Wi-Fi networks, or by disguising itself as a legitimate app in the Google Play Store. To protect against XploitSPY Malware, users should be cautious when clicking on links or downloading apps from unknown sources, keep their devices up to date with the latest security patches, and use reputable antivirus software to scan for and remove any malicious software.
Read more