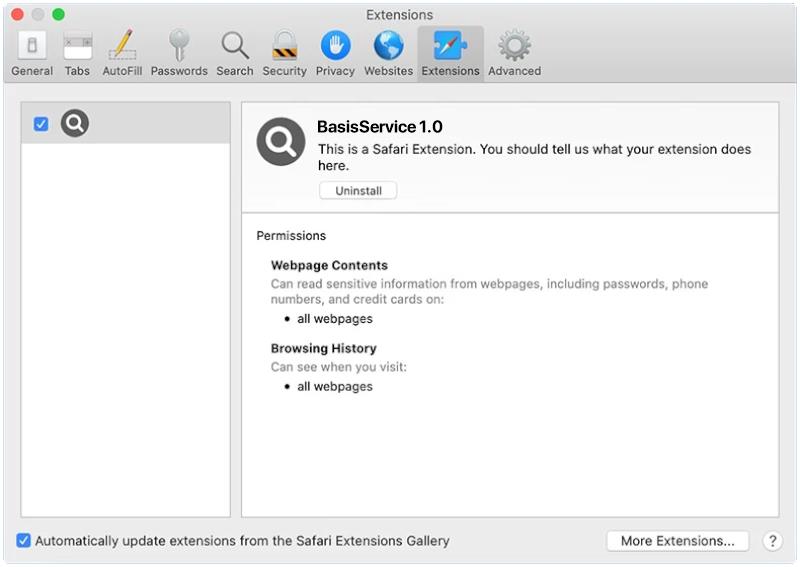
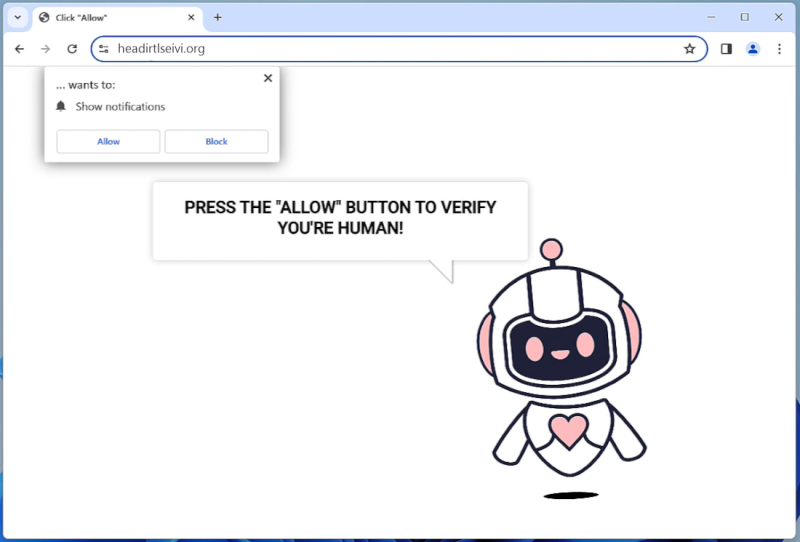
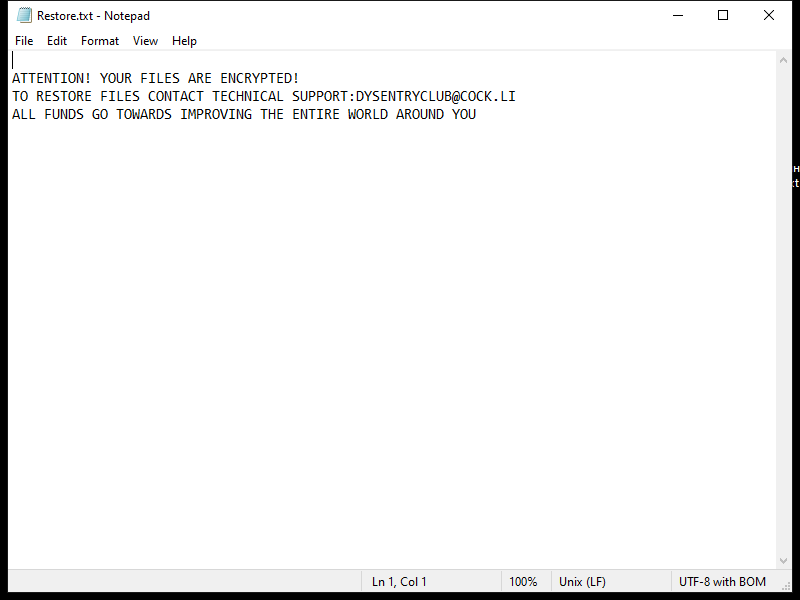
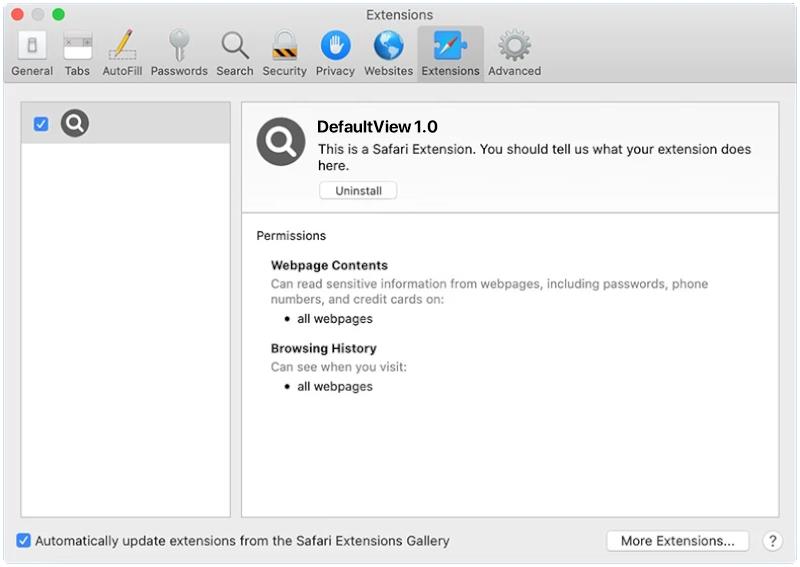
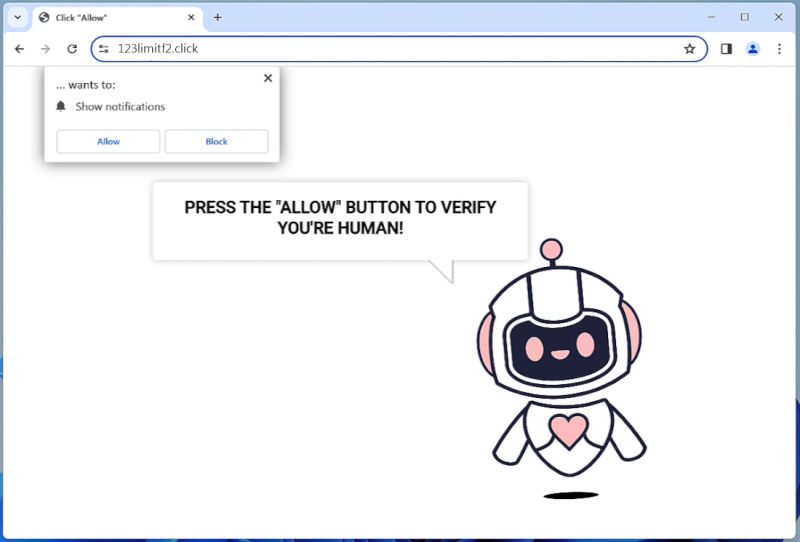
BasisService is a type of malware that specifically targets Mac computers. It is a malicious software that infects Mac systems and can cause a variety of issues, including slow performance, unauthorized access to sensitive information, and system crashes. BasisService is often distributed through phishing emails, malicious websites, or software downloads. Once installed on a Mac computer, BasisService can run in the background without the user’s knowledge, making it difficult to detect and remove.
BasisService infects Mac computers by exploiting vulnerabilities in the operating system or by tricking users into downloading and installing the malware unknowingly. Once installed, BasisService can execute various malicious activities, such as stealing personal information, logging keystrokes, and remotely controlling the infected computer. To protect against BasisService and other malware, Mac users should be cautious when clicking on links or downloading files from unknown sources and should regularly update their system and security software.