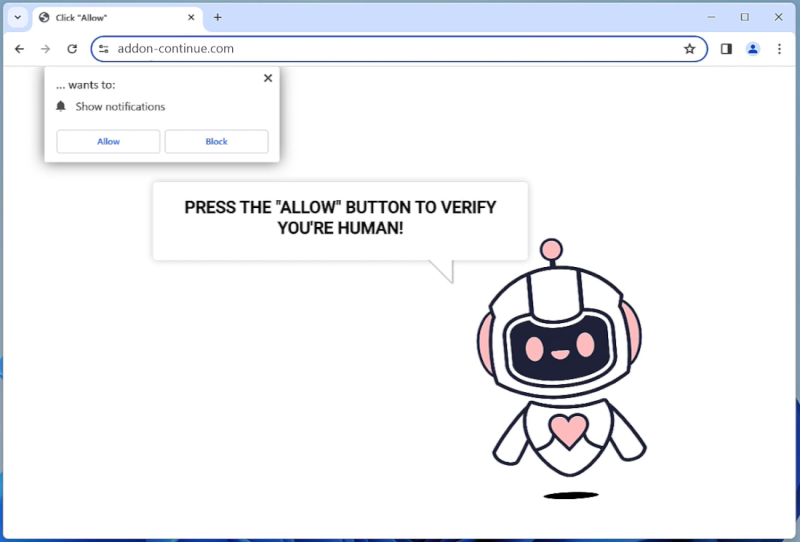
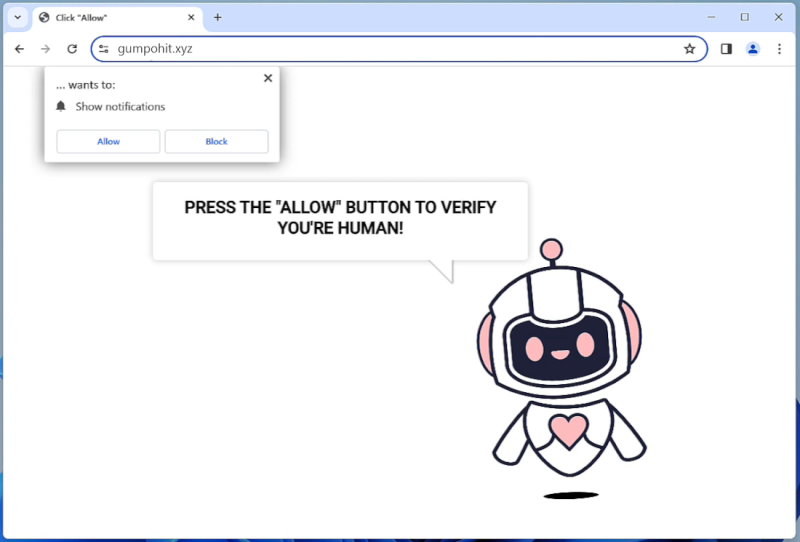
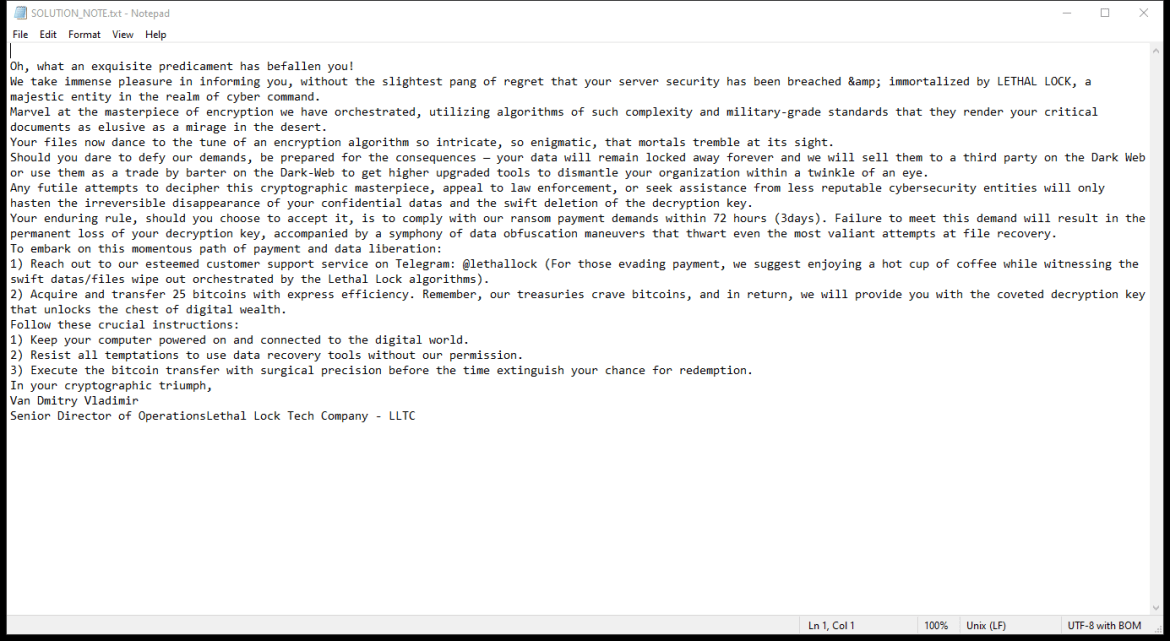
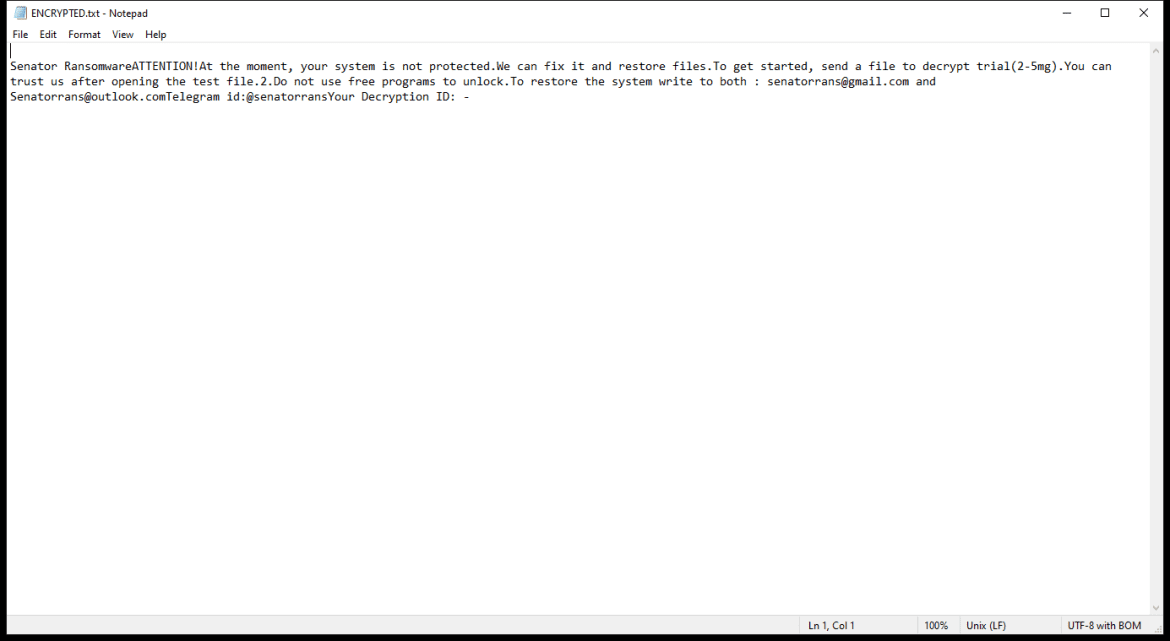
Addon-continue.com is a malicious website that infects computers by tricking users into allowing browser notifications. It often disguises itself as a legitimate website or a pop-up ad, prompting users to click on a button to continue or access content. Once users click on the button, they unknowingly grant permission for Addon-continue.com to send notifications to their browser.
Once Addon-continue.com gains access to the browser notifications, it can start displaying intrusive pop-ups, ads, and notifications that can redirect users to more malicious websites or prompt them to download malware. This can lead to a compromised browsing experience, slower computer performance, and potential security risks. Addon-continue.com can infect various browsers such as Google Chrome, Mozilla Firefox, and Microsoft Edge, and it can target both desktop and mobile devices. It is important for users to be cautious when granting permissions for browser notifications and to regularly scan their devices for any signs of malware or unwanted programs.