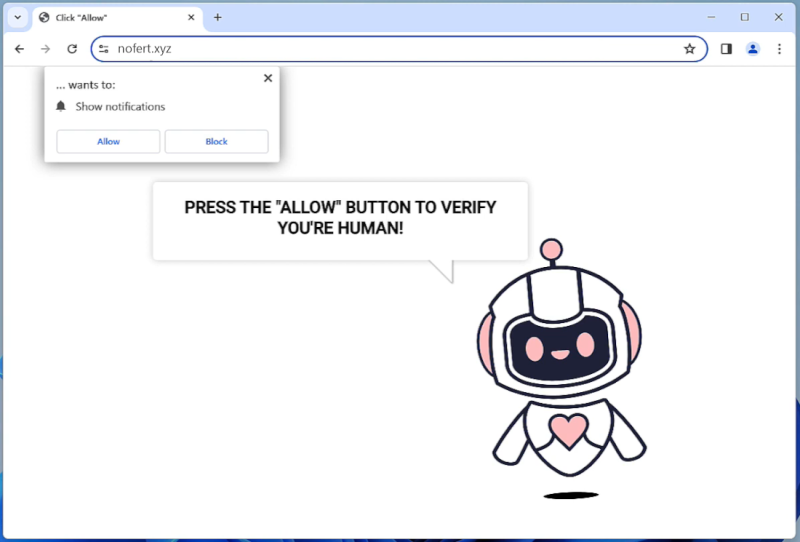
Nofert.xyz is a malicious website that infects computers by tricking users into allowing push notifications. It typically spreads through deceptive ads, fake software updates, or malicious websites. Once a user clicks on the notification prompt, they unknowingly give permission for Nofert.xyz to send them unwanted notifications.
After gaining access to the browser notifications, Nofert.xyz can bombard users with intrusive pop-ups, ads, and redirects to other malicious websites. It can also collect sensitive information about the user’s browsing habits and use it for targeted advertising or other malicious purposes. Nofert.xyz primarily targets popular web browsers like Google Chrome, Mozilla Firefox, and Safari, and can infect a variety of devices, including desktops, laptops, and mobile phones. Users are advised to be cautious when browsing online and to avoid clicking on suspicious links or allowing notifications from unknown websites to prevent infection by Nofert.xyz.