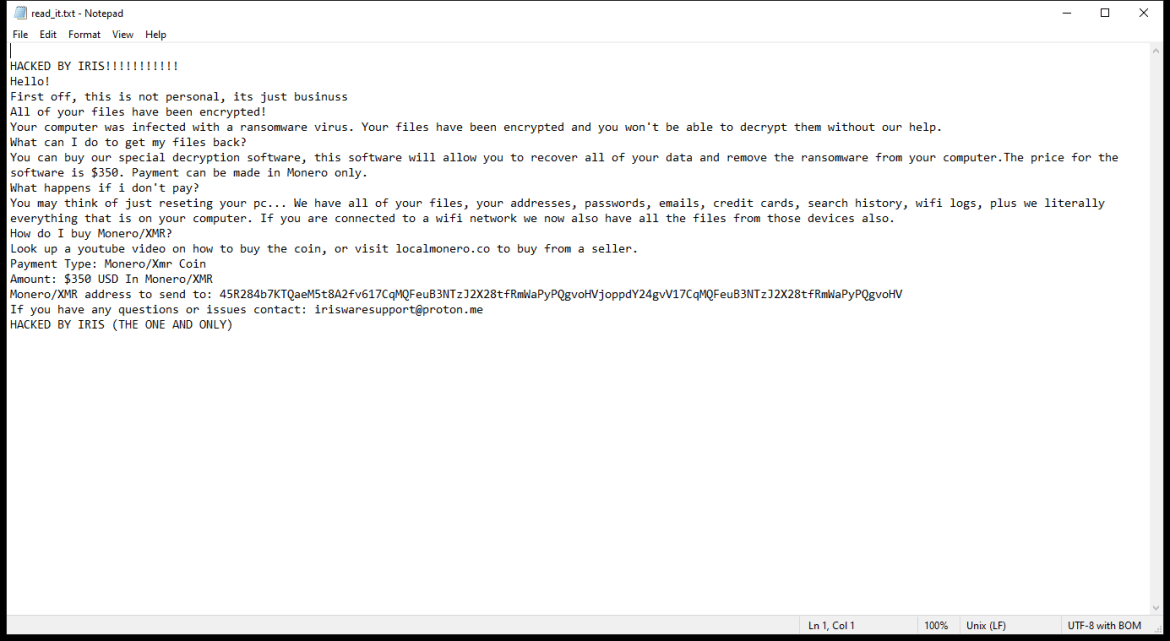
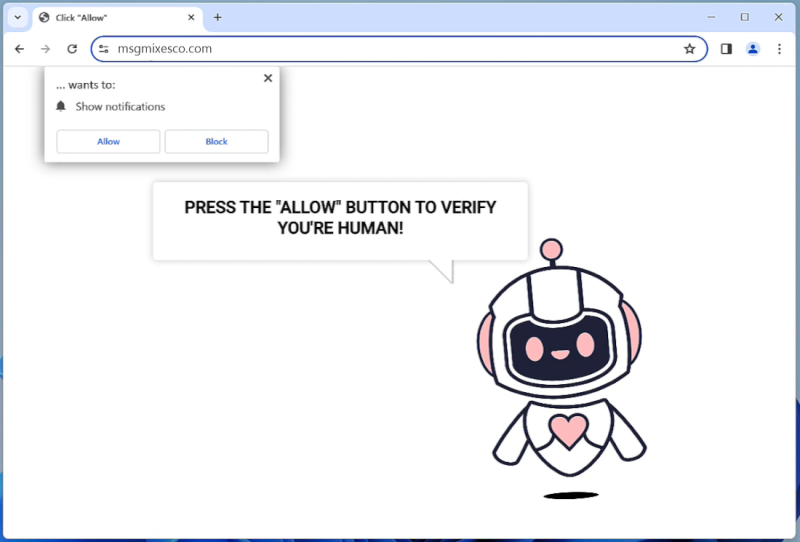
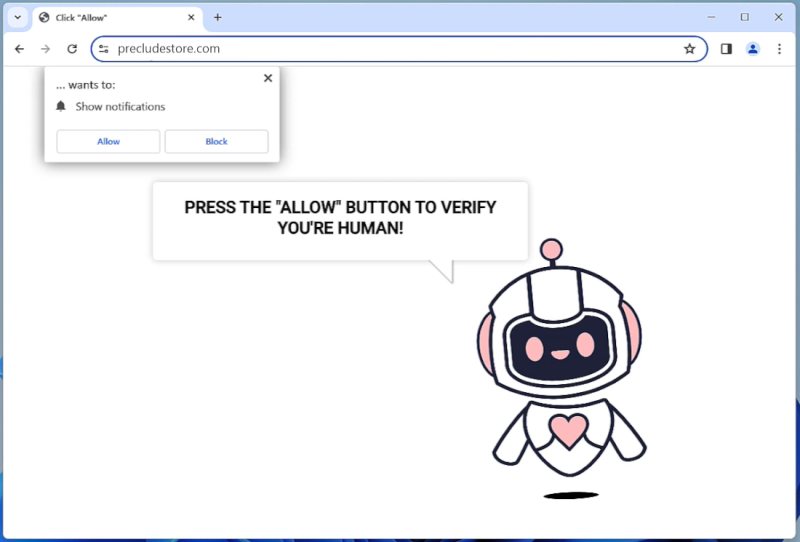
ChainGPT DAPP is a decentralized application that utilizes the power of artificial intelligence to generate text content. It is built on blockchain technology, which ensures that the content created is secure, transparent, and tamper-proof. Users can access ChainGPT DAPP through their web browsers, allowing them to easily create and access text content on the platform.
The reason why ChainGPT DAPP appears in browsers is to provide a user-friendly and accessible interface for users to interact with the application. By integrating with web browsers, users can easily access and utilize the features of ChainGPT DAPP without the need for additional software or downloads. This seamless integration enhances the user experience and makes it convenient for individuals to leverage the power of artificial intelligence for generating text content.