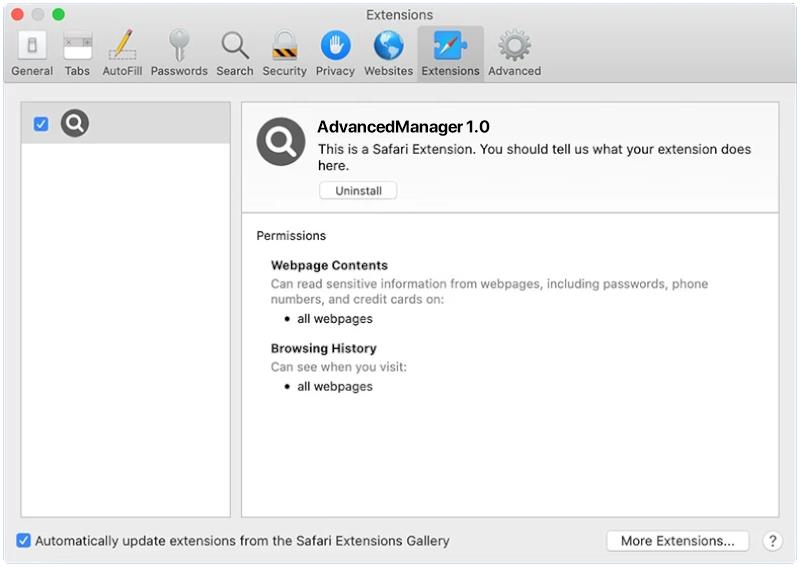
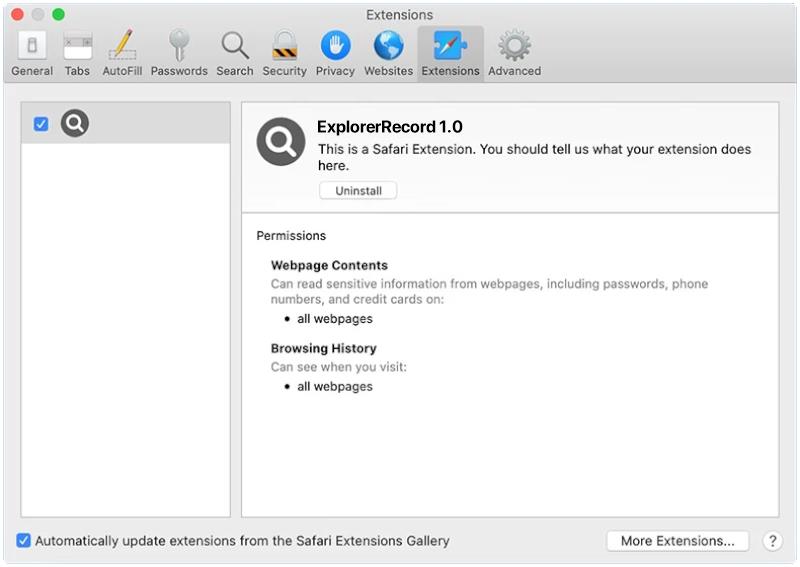
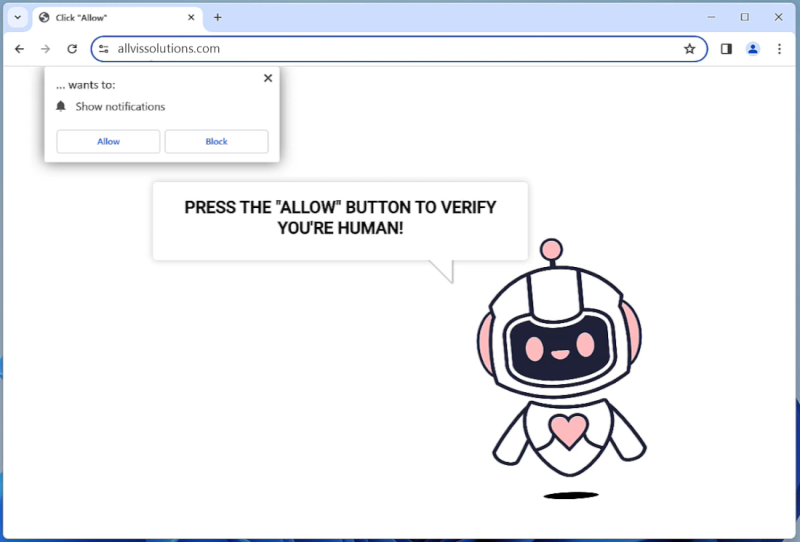
AdvancedManager is a type of malicious software that infects Mac computers to steal personal information, track online activities, and display unwanted advertisements. This malware can be distributed through malicious websites, email attachments, or disguised as legitimate software downloads. Once installed on a Mac system, AdvancedManager can gain access to sensitive data such as usernames, passwords, and credit card information, putting the user at risk of identity theft and financial fraud.
AdvancedManager infects Mac computers by exploiting vulnerabilities in the operating system or through social engineering tactics such as phishing emails or fake software updates. Once the malware is installed, it can run silently in the background, collecting data and sending it to remote servers controlled by cybercriminals. Users may notice a decrease in system performance, unusual pop-up ads, or unauthorized changes to browser settings, indicating that their Mac has been infected with AdvancedManager. To protect against this threat, users should regularly update their operating system, avoid clicking on suspicious links or downloading unknown software, and use reputable antivirus software to detect and remove malware infections.