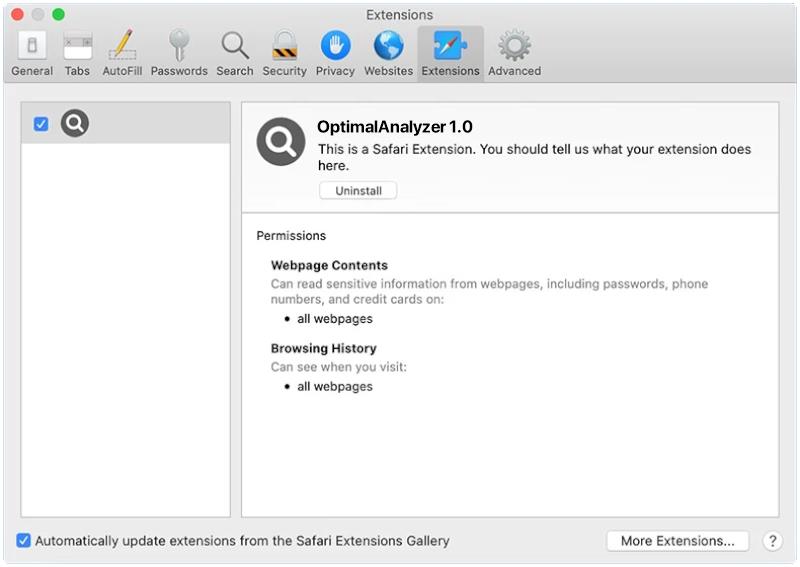
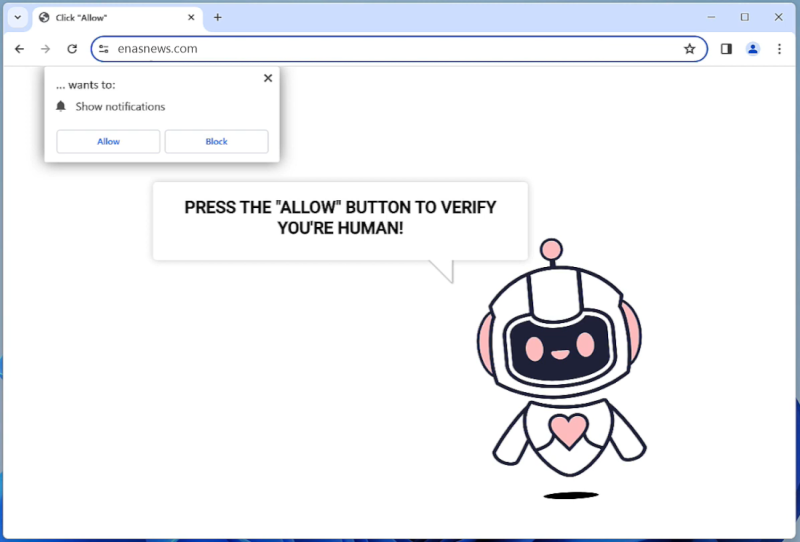
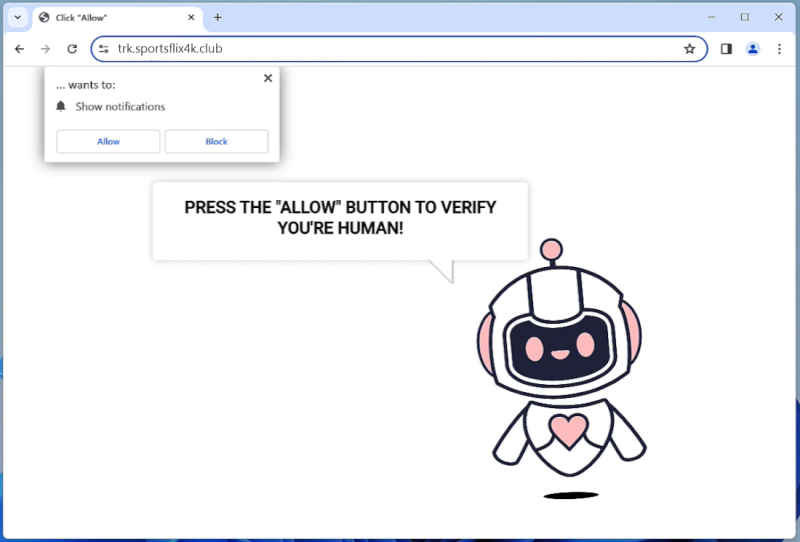
OptimalAnalyzer is a type of potentially unwanted program (PUP) that is designed to infect Mac computers and display intrusive advertisements to users. This software often gets installed on a user’s system without their knowledge or consent, typically through software bundling or deceptive marketing tactics. Once on a Mac, OptimalAnalyzer may run in the background, collecting user data and browsing habits to serve targeted ads. It can also slow down the system’s performance and cause unwanted pop-ups to appear on the screen.
To infect a Mac, OptimalAnalyzer may be bundled with other free software that users download from the internet. Once installed, it can modify browser settings and inject ads into web pages, making it difficult to browse the internet without being bombarded with advertisements. Users may also notice a decrease in their computer’s speed and performance as a result of the program running in the background. To remove OptimalAnalyzer from a Mac, users can use reputable antivirus software or follow manual removal instructions provided by cybersecurity experts.