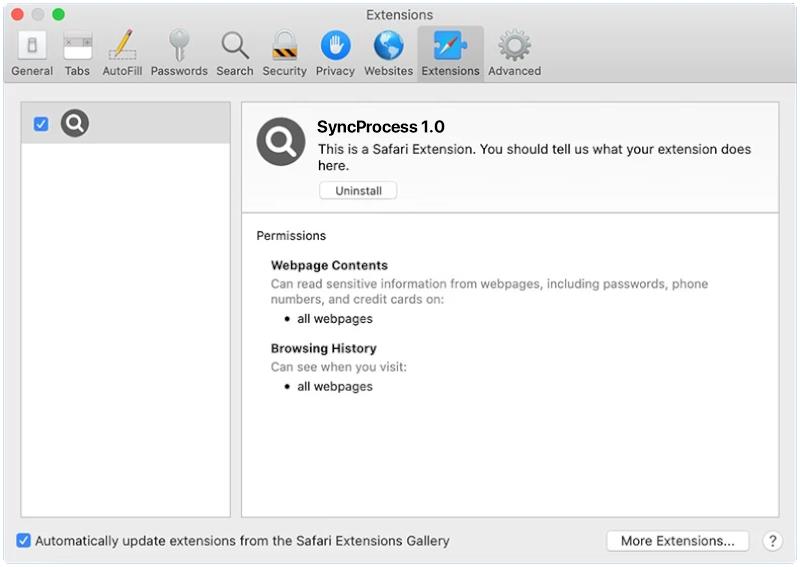
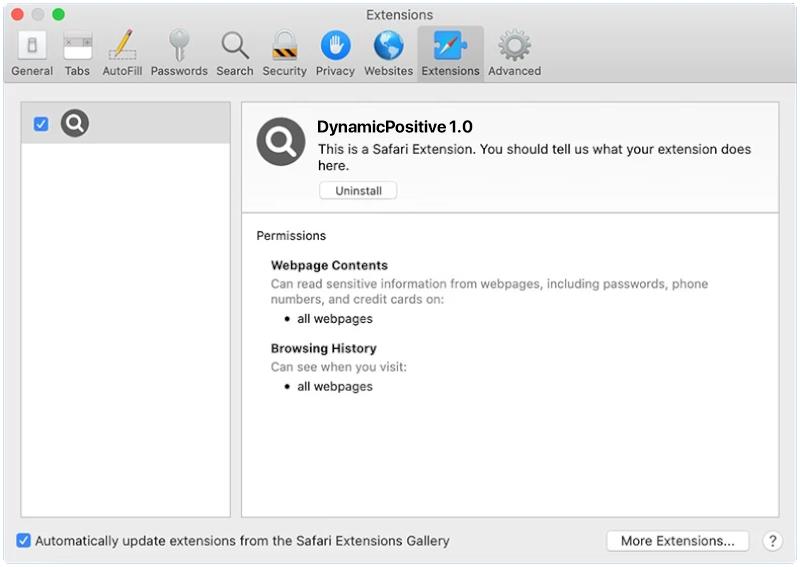
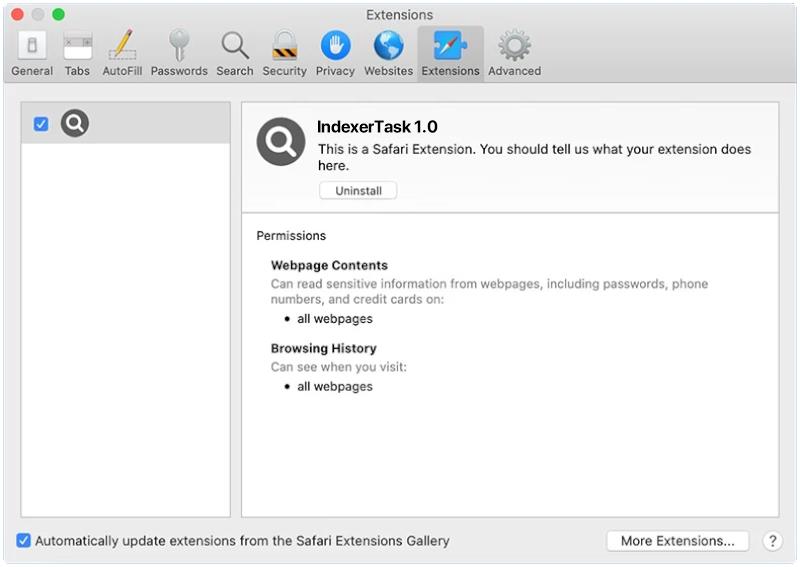
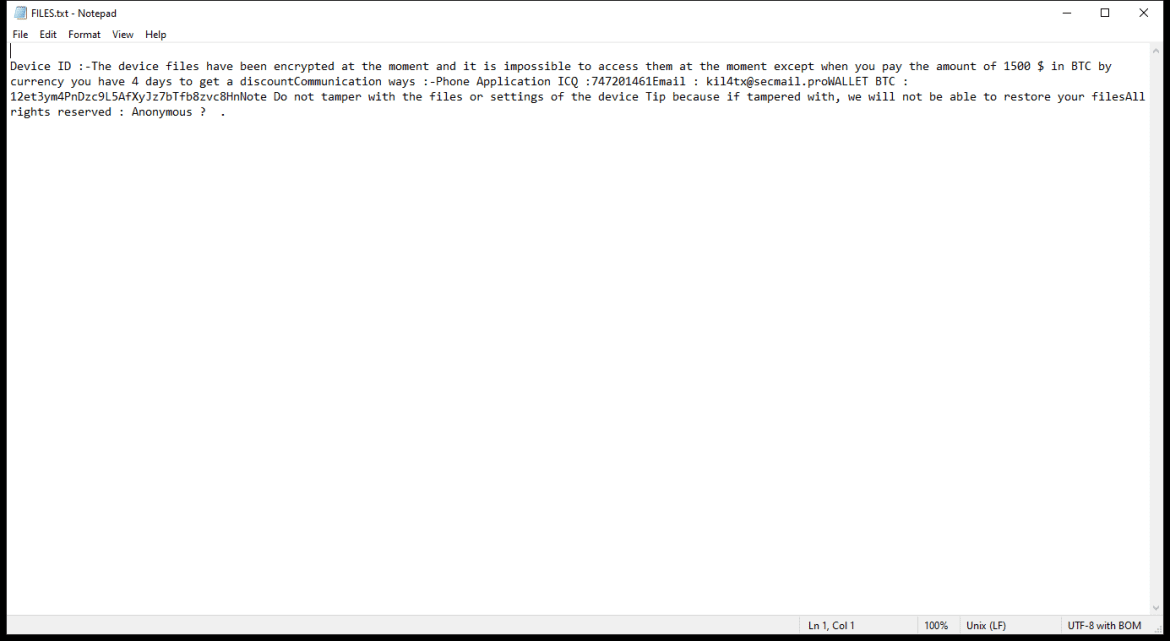
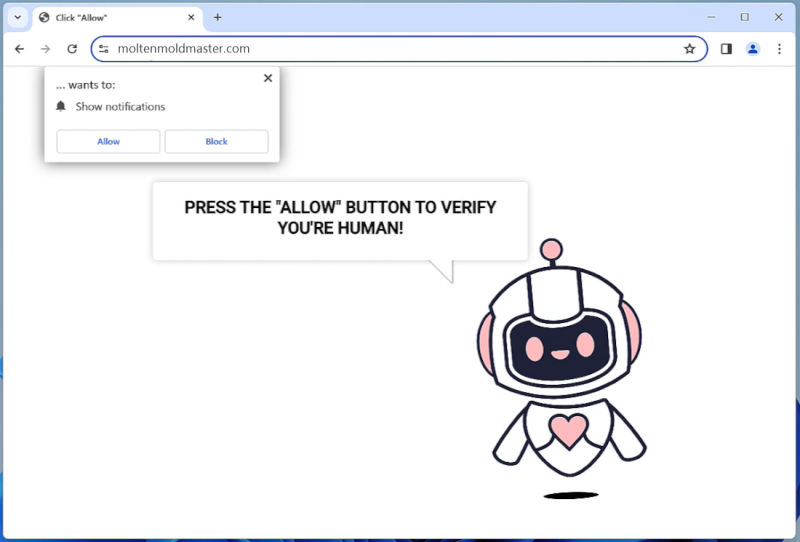
SyncProcess is a type of malware that specifically targets Mac computers. It is designed to infect Mac systems and carry out various malicious activities, such as stealing sensitive information, monitoring user activities, and delivering unwanted advertisements. SyncProcess is a potentially harmful program that can disrupt the normal functioning of a Mac computer and compromise the security and privacy of the user.
SyncProcess can infect Mac computers through various means, including malicious email attachments, software downloads from untrustworthy sources, or by exploiting vulnerabilities in the operating system. Once installed on a Mac system, SyncProcess can run silently in the background, making it difficult for users to detect its presence. It can also spread to other devices on the same network, further compromising the security of the entire network. To protect against SyncProcess and other malware, Mac users should be cautious when downloading software, avoid clicking on suspicious links or email attachments, and regularly update their operating system and security software.