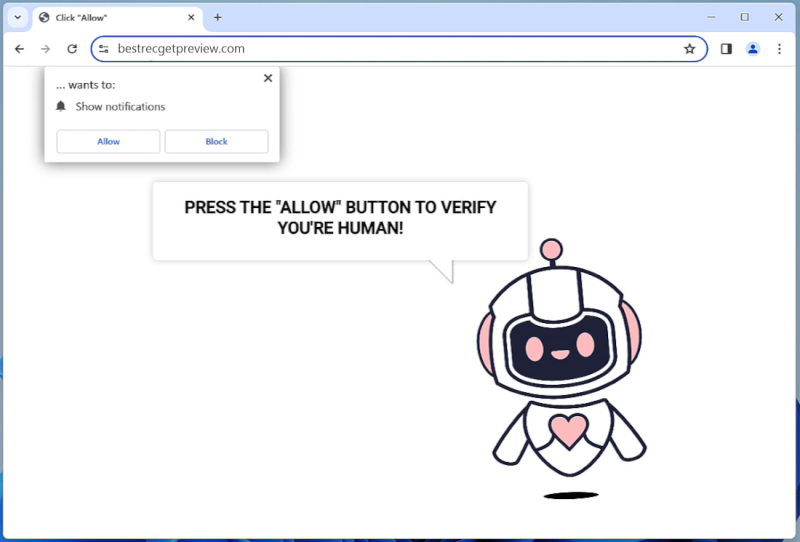
Lookupsearchers.com is adware that is designed to display unwanted advertisements and redirect users to sponsored websites. This adware typically infects computers and browsers through software bundling, where it is included in the installation package of free software and installed on the system without the user’s knowledge or consent. Once installed, Lookupsearchers.com starts displaying pop-up ads, banners, and in-text ads on the affected browsers, making the browsing experience unpleasant and potentially exposing users to malicious content.
Lookupsearchers.com can also infect computers and browsers through malicious websites, fake software updates, or clicking on malicious links. Once installed, it may collect user data, such as browsing history and search queries, to display targeted advertisements. In addition, Lookupsearchers.com may also change browser settings, such as the default homepage and search engine, to promote sponsored websites and products. To remove Lookupsearchers.com adware, users should use reputable anti-malware software to scan and clean their systems.