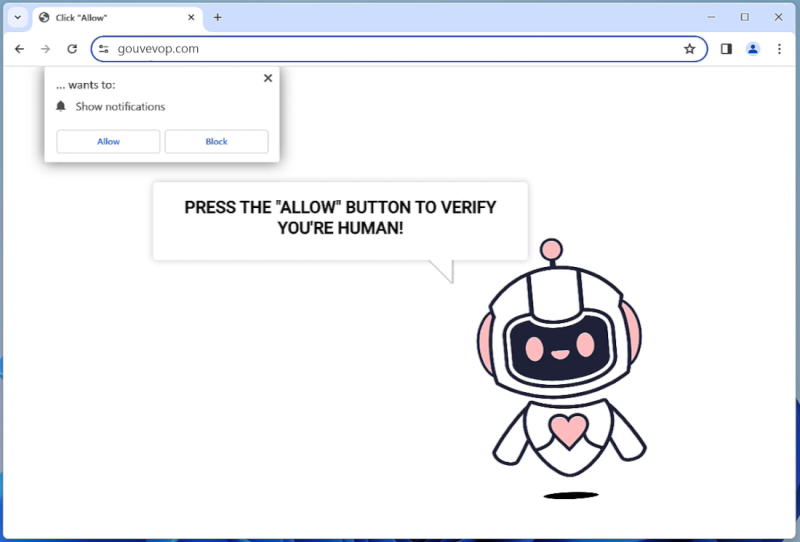
Lookingup-lookup.com is a type of adware that infiltrates computers and web browsers in order to display unwanted advertisements to users. This adware typically gets installed on a computer when a user downloads and installs freeware or shareware programs from untrustworthy sources. Once installed, Lookingup-lookup.com modifies browser settings and starts displaying pop-up ads, banners, and sponsored links on websites that the user visits.
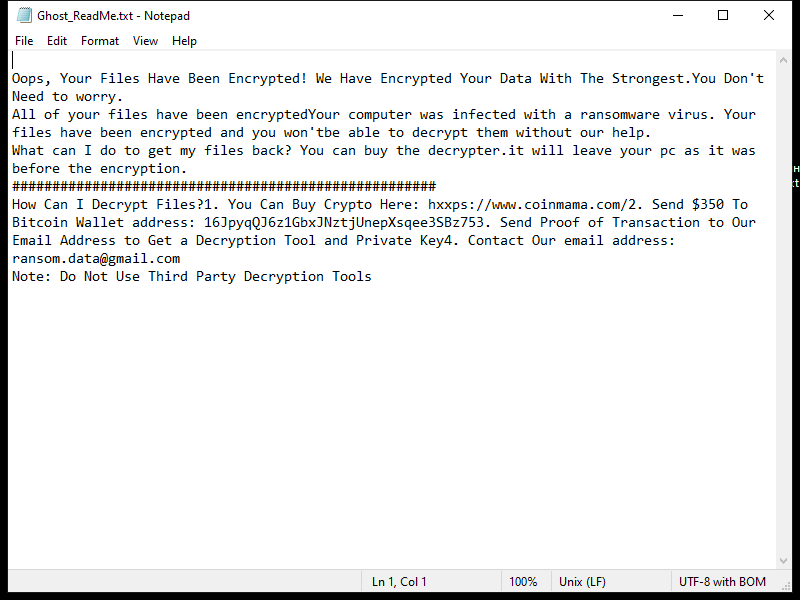
Lookingup-lookup.com adware can also infect computers through malicious websites, email attachments, or fake software updates. It can track users’ browsing habits and collect personal information, such as browsing history, search queries, and IP address. This information is then used to display targeted ads to the user. Additionally, Lookingup-lookup.com adware can slow down the computer’s performance, cause browser crashes, and redirect users to potentially harmful websites. It is important for users to regularly scan their computers for adware and avoid downloading software from unknown sources to prevent infections like Lookingup-lookup.com.