Heur:Trojan.Androidos.Boogr.Gsh is a type of Trojan malware that specifically targets Android operating systems. This Trojan is designed to steal sensitive information from infected devices, such as personal data, login credentials, and financial information.
Heur:Trojan.Androidos.Boogr.Gsh can infect Android devices through various means, including:
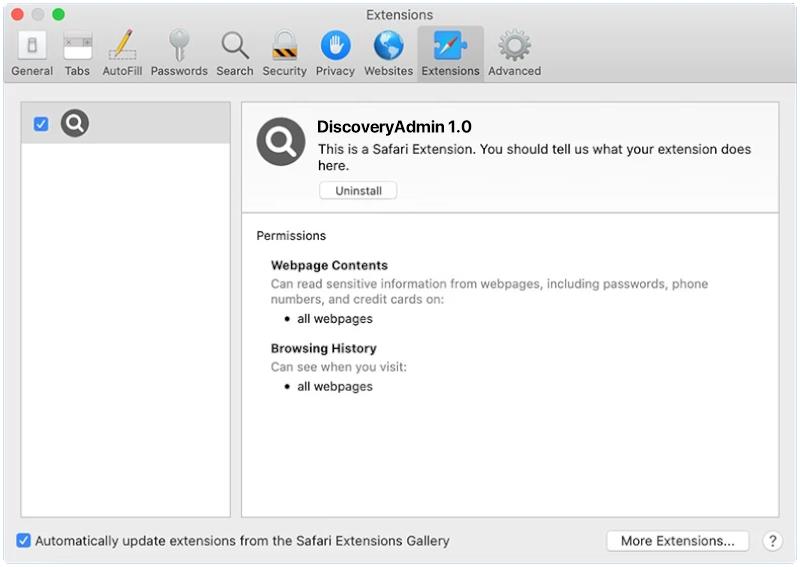
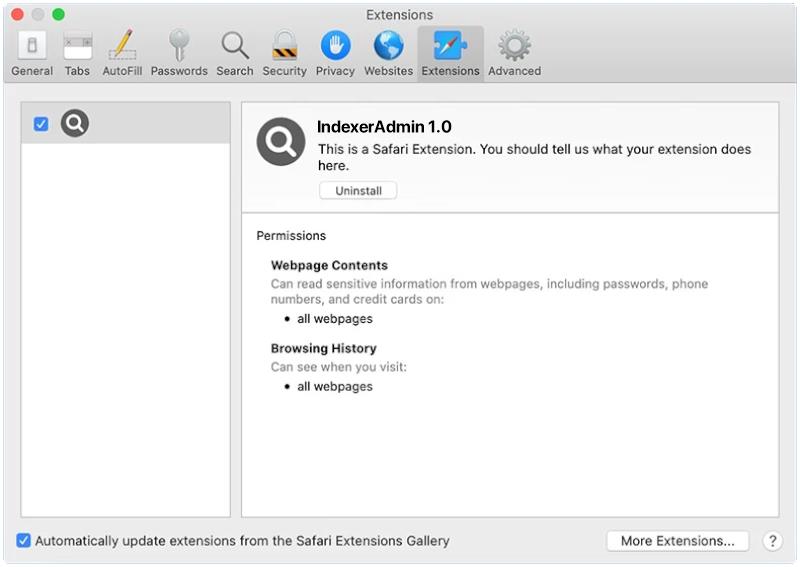
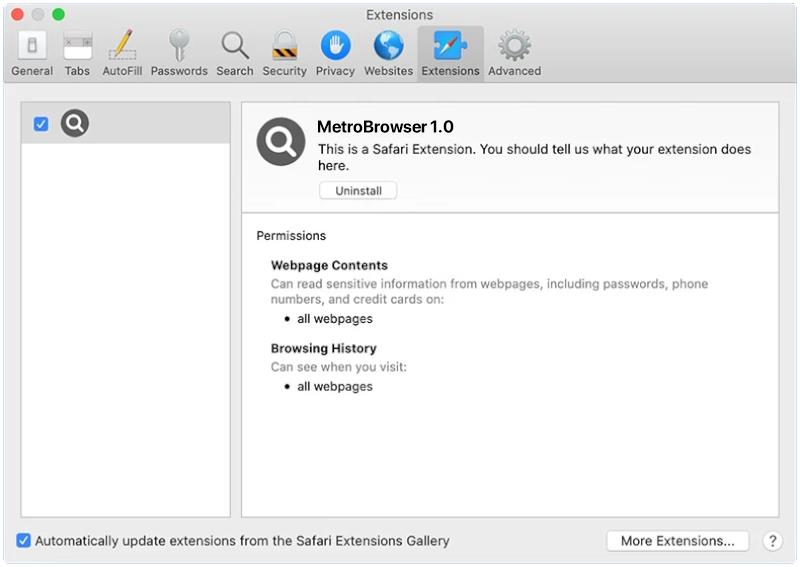
1. Malicious apps: The Trojan may be hidden within seemingly legitimate apps that users download from third-party app stores or websites.
2. Phishing links: Users may be tricked into clicking on malicious links in emails, text messages, or social media posts, which can lead to the installation of the Trojan on their device.
3. Exploiting vulnerabilities: The Trojan may exploit security vulnerabilities in the Android operating system or other software to gain access to the device.
Once installed, Heur:Trojan.Androidos.Boogr.Gsh can run in the background of the infected device, collecting and transmitting data to remote servers controlled by cybercriminals. It can also perform other malicious activities, such as downloading additional malware or displaying unwanted advertisements.
To protect against Heur:Trojan.Androidos.Boogr.Gsh and other types of malware, users should only download apps from trusted sources, keep their devices and software up to date with the latest security patches, and avoid clicking on suspicious links or downloading files from unknown sources.