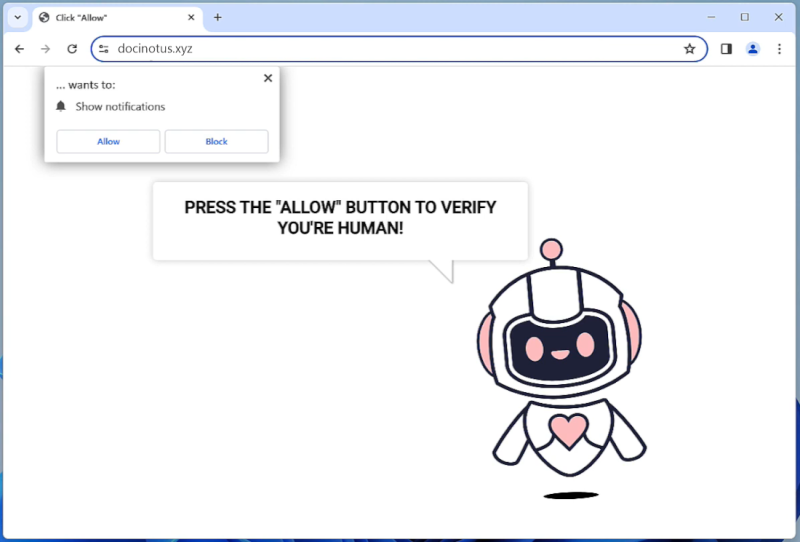
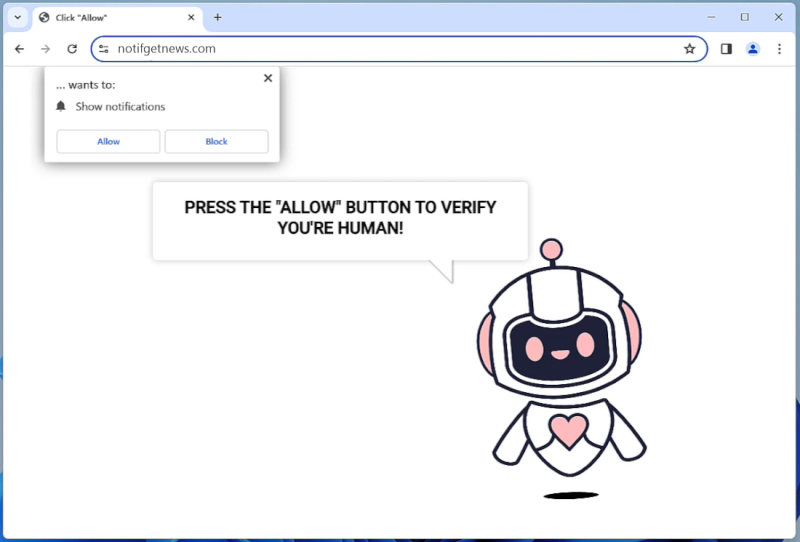
Notifgetnews.com is a malicious website that infects computers by tricking users into allowing push notifications. Once a user visits the website, they are prompted with a message asking to enable notifications to continue browsing. If the user agrees, they unknowingly give permission for Notifgetnews.com to send unwanted notifications directly to their desktop or mobile device.
Notifgetnews.com exploits browser notifications by bombarding users with pop-up messages containing advertisements, fake alerts, or links to other malicious websites. These notifications can be very intrusive and disruptive to the user’s browsing experience. Notifgetnews.com primarily targets popular web browsers such as Google Chrome, Mozilla Firefox, and Safari, and can infect both desktop and mobile devices. Users are advised to be cautious when visiting unfamiliar websites and to always decline notifications from suspicious sources to prevent infection by Notifgetnews.com.

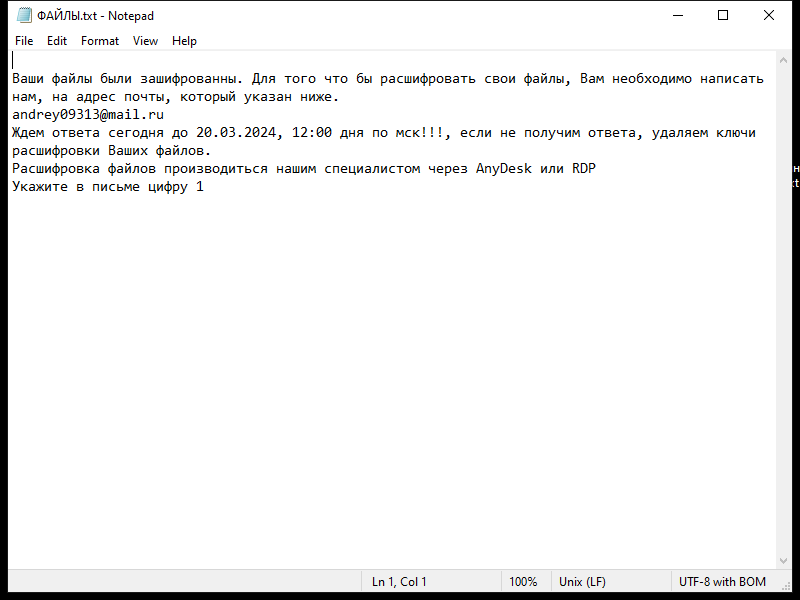
![How to remove Win32:Gepys-B [Trj]](https://malwarewarrior.com/wp-content/uploads/2024/03/win32-gepys-b-trj--1170x669.png)