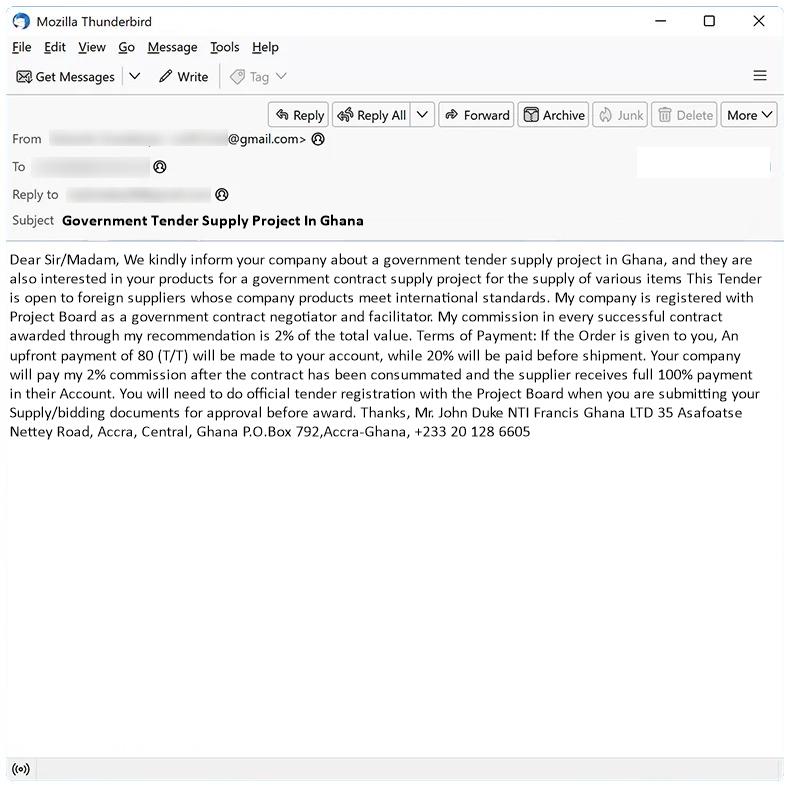
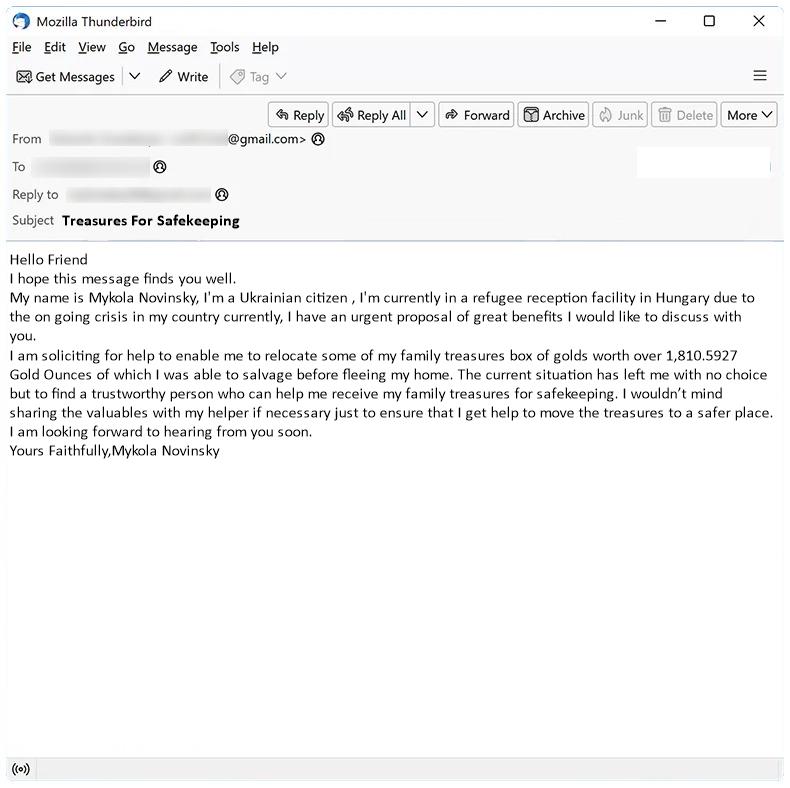
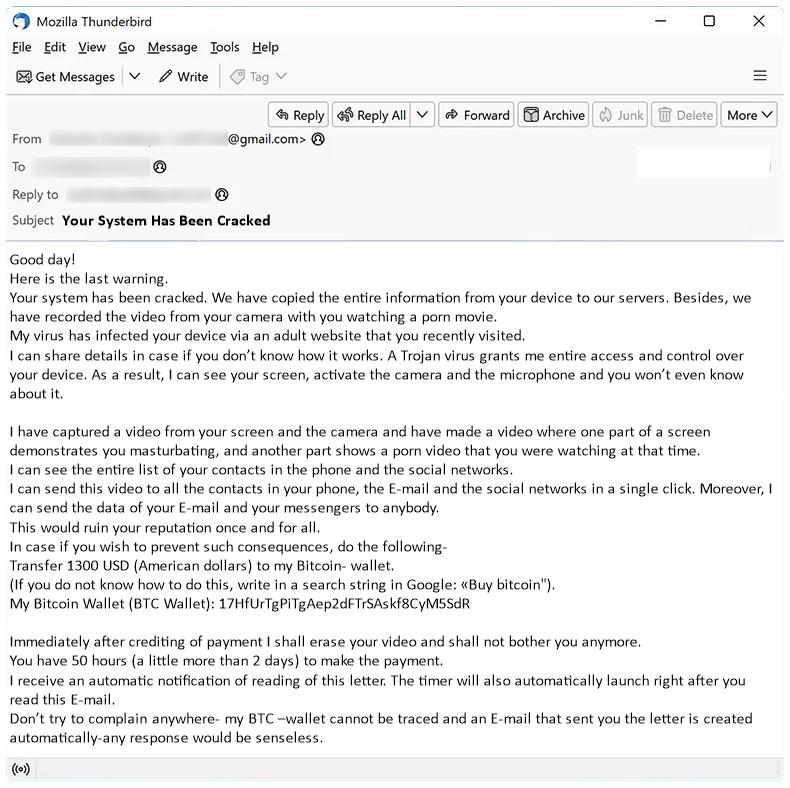
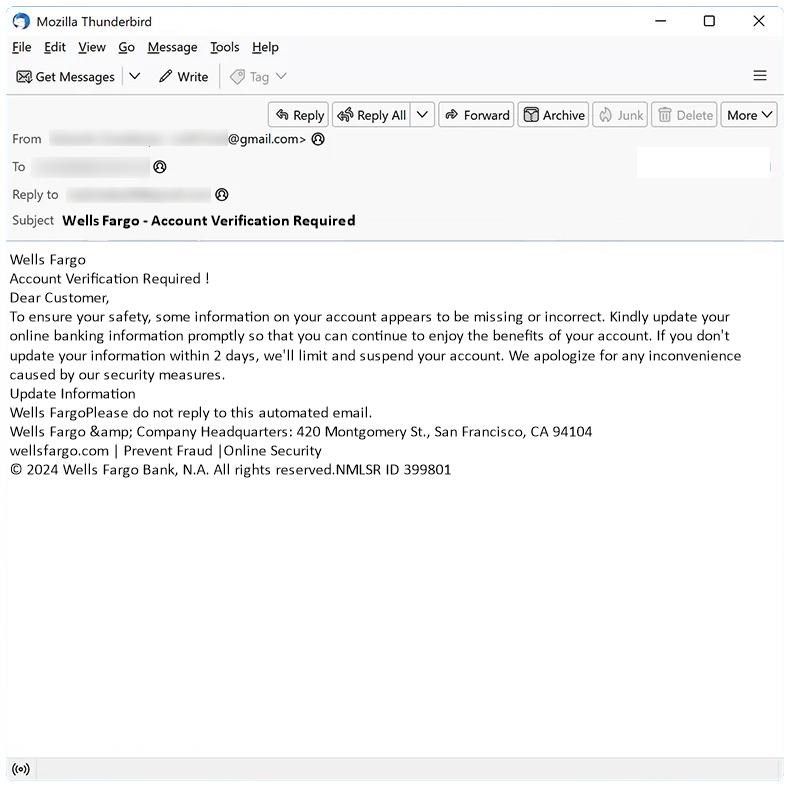
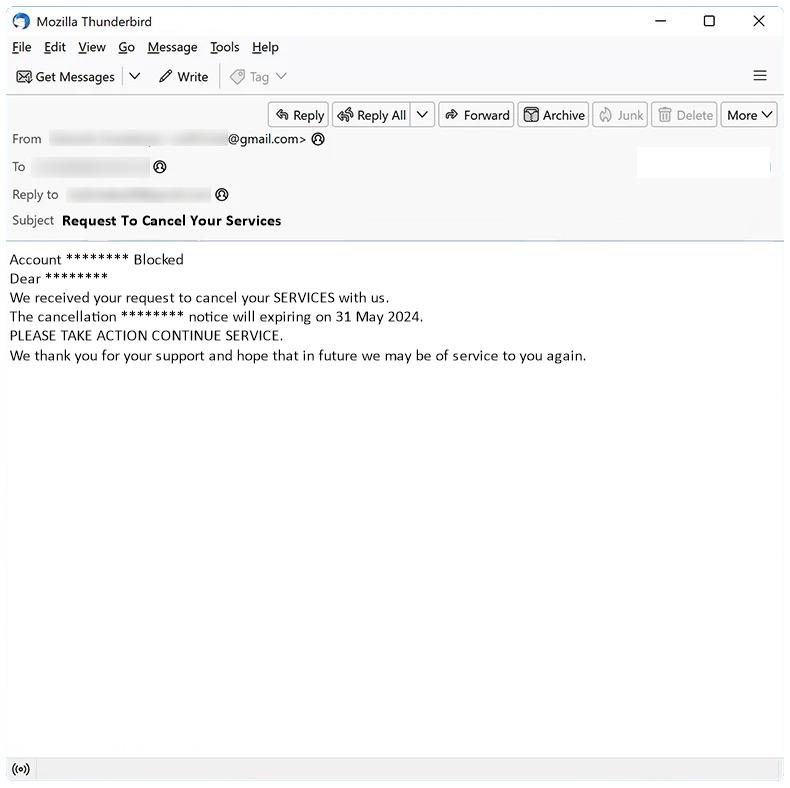
Government Tender Supply Project In Ghana email spam is a type of phishing scam where cybercriminals impersonate government agencies or organizations in Ghana to trick recipients into providing personal information or making fraudulent payments.
These spam campaigns typically involve sending out emails claiming that the recipient has been awarded a government tender supply project in Ghana and must provide personal information or pay a fee to secure the contract. The emails often contain fake documents or references to make them appear legitimate.
Interacting with Government Tender Supply Project In Ghana email scam poses several risks, including:
1. Identity theft: Providing personal information in response to the email scam can lead to identity theft, where cybercriminals use the information to commit fraud or access sensitive accounts.
2. Financial loss: Victims of the scam may be tricked into making fraudulent payments or providing financial information, resulting in financial loss.
3. Malware infection: In some cases, email scams may contain malicious attachments or links that, when clicked, can infect the recipient’s computer with malware, such as ransomware or spyware.
To protect yourself from falling victim to Government Tender Supply Project In Ghana email spam, it is important to be cautious of unsolicited emails, especially those requesting personal information or payment. Verify the legitimacy of the sender and the email content before taking any action. Additionally, make sure to keep your computer’s security software up to date to help prevent malware infections.