The 2000USD Ransomware is a type of malware that encrypts the files on a victim’s computer and demands a ransom of 2000 USD in exchange for the decryption key. It typically infects computers through malicious email attachments, software downloads, or exploiting vulnerabilities in the system.
Once the ransomware infects a computer, it adds a specific file extension to the encrypted files, such as “.2000usd“. It uses a strong encryption algorithm to lock the files, making them inaccessible without the decryption key.
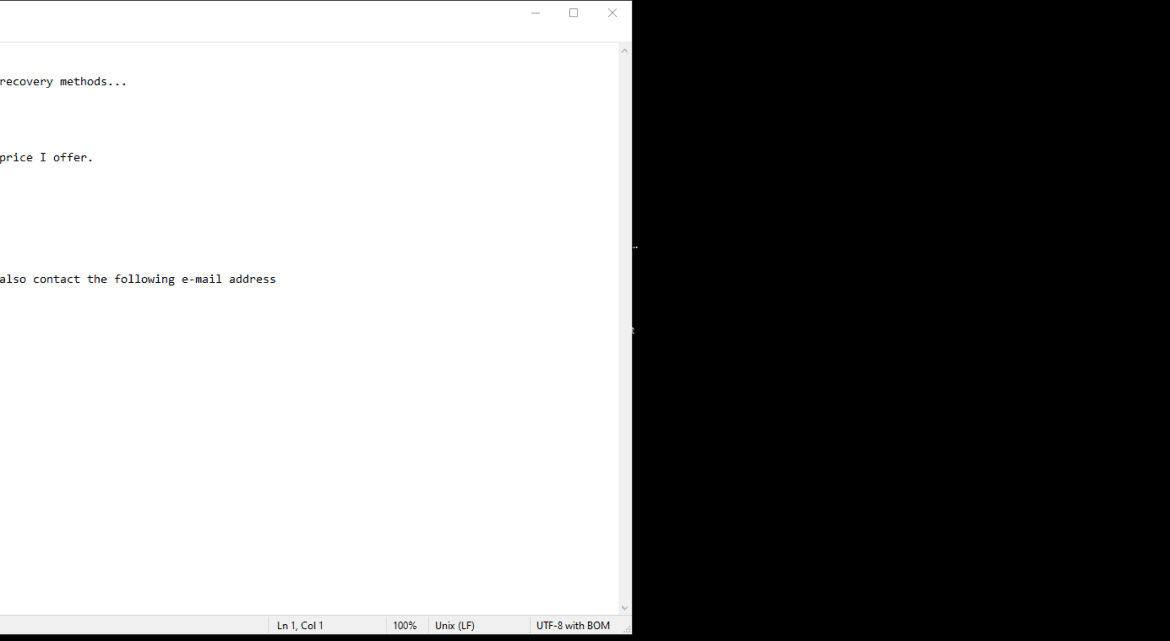
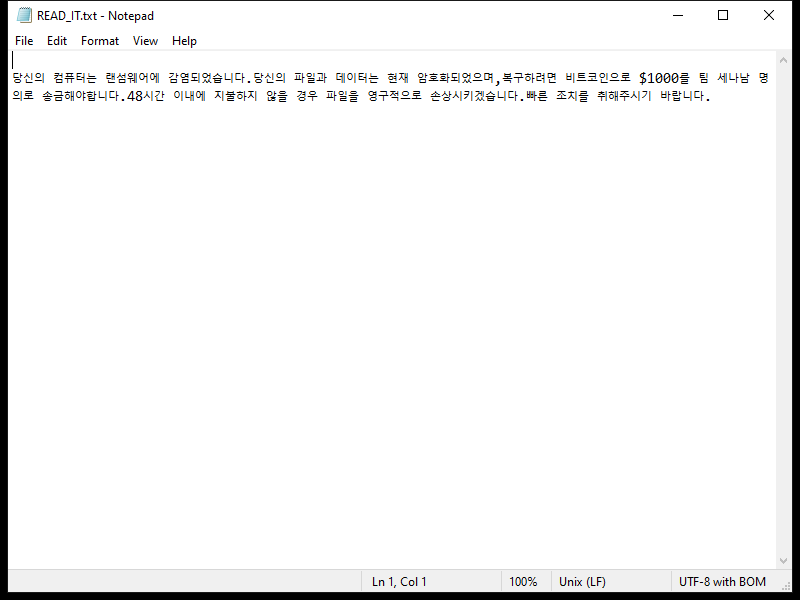
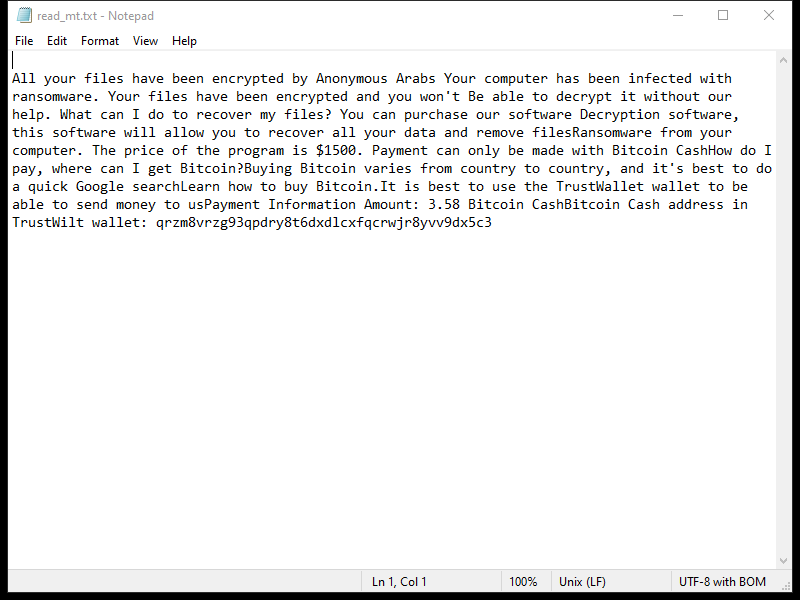
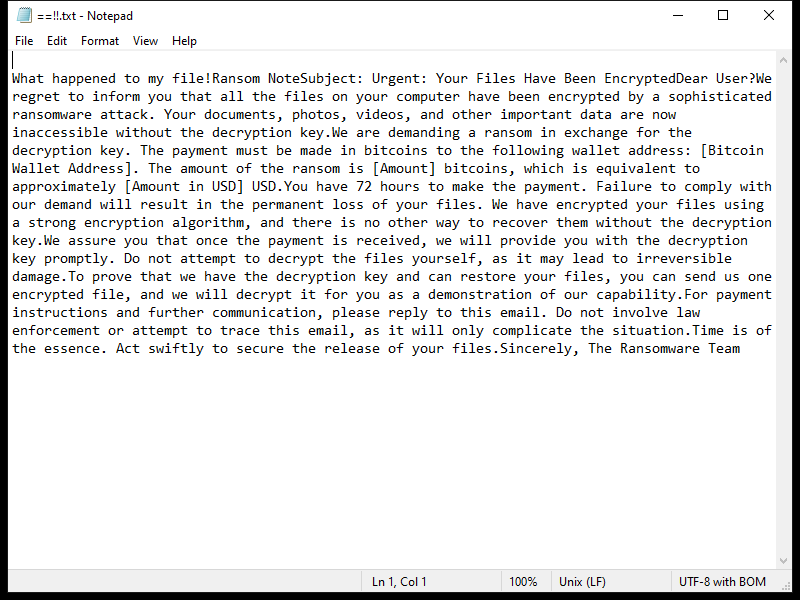
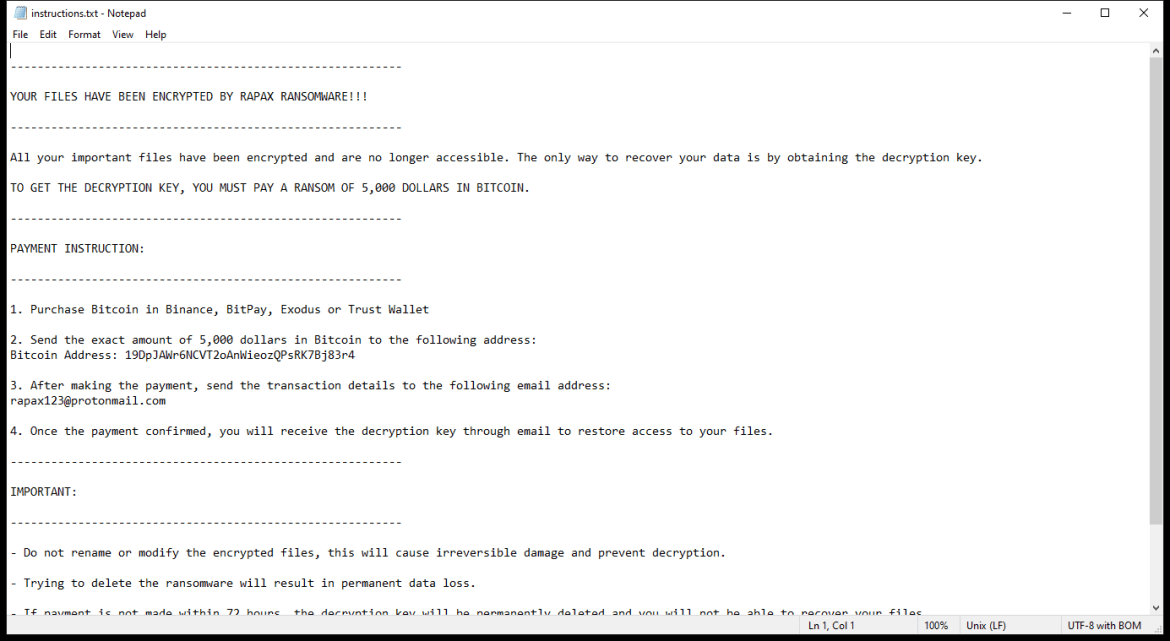
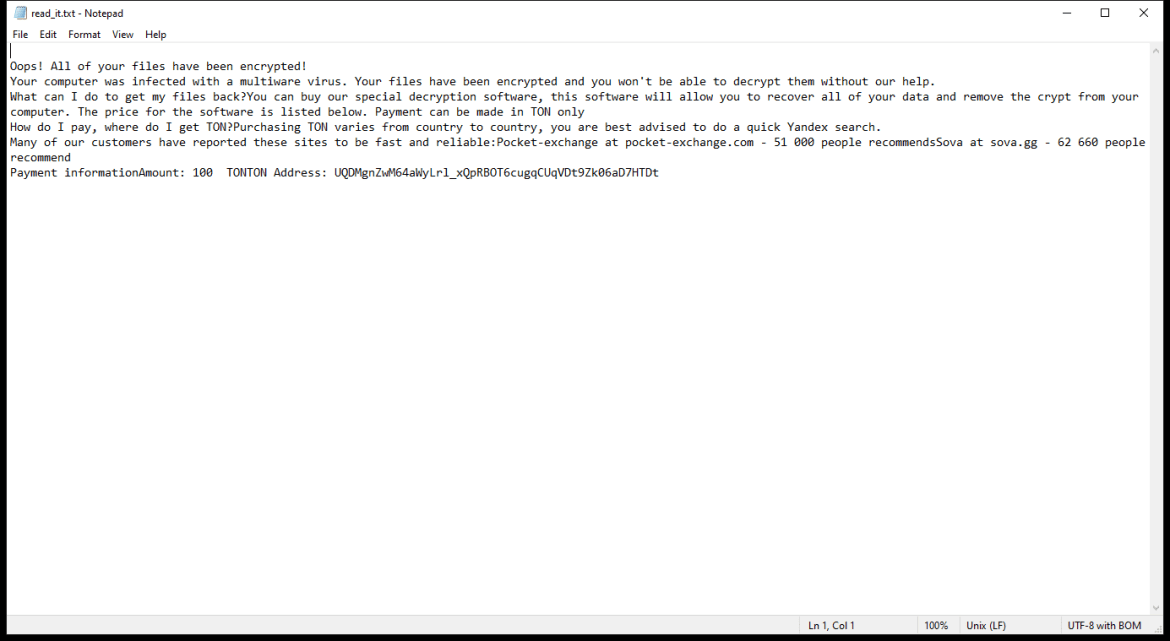
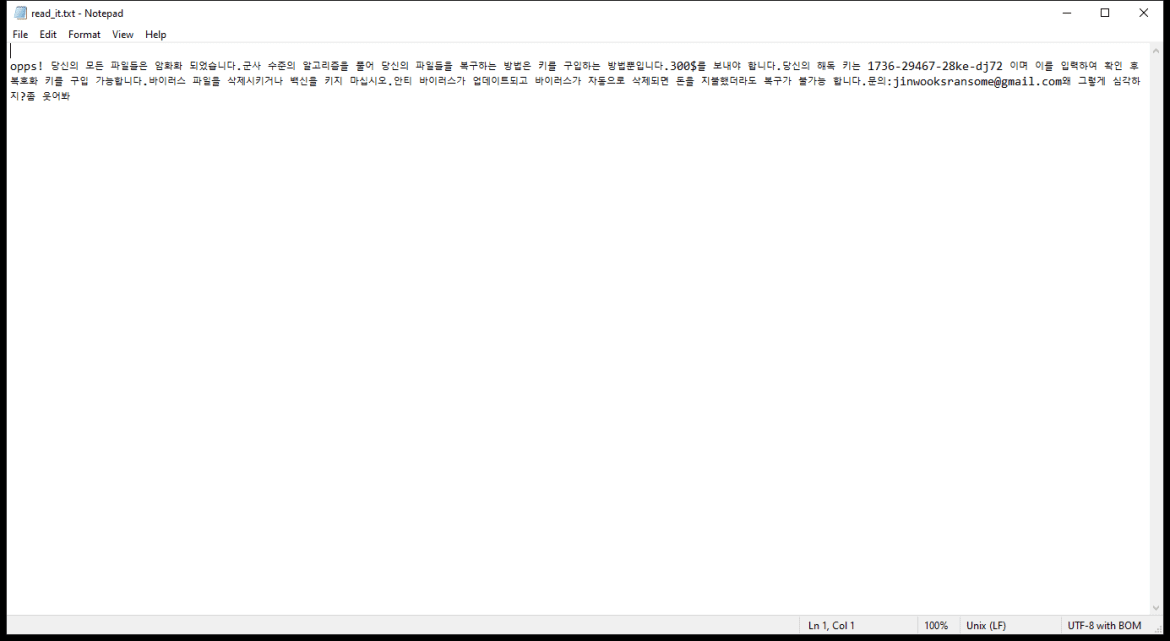
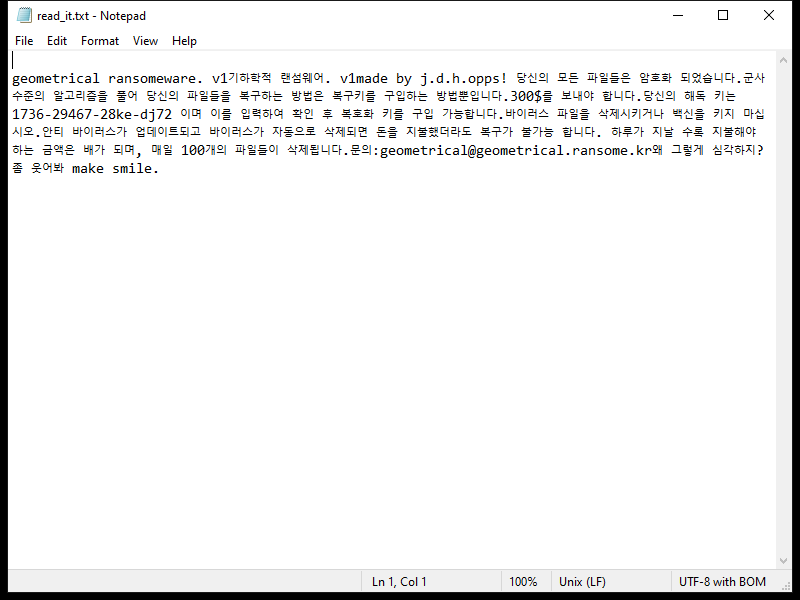
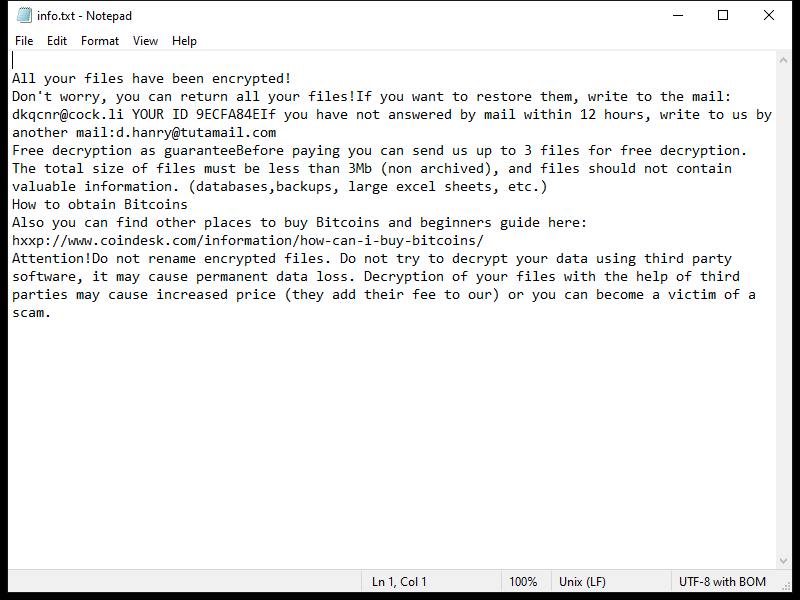
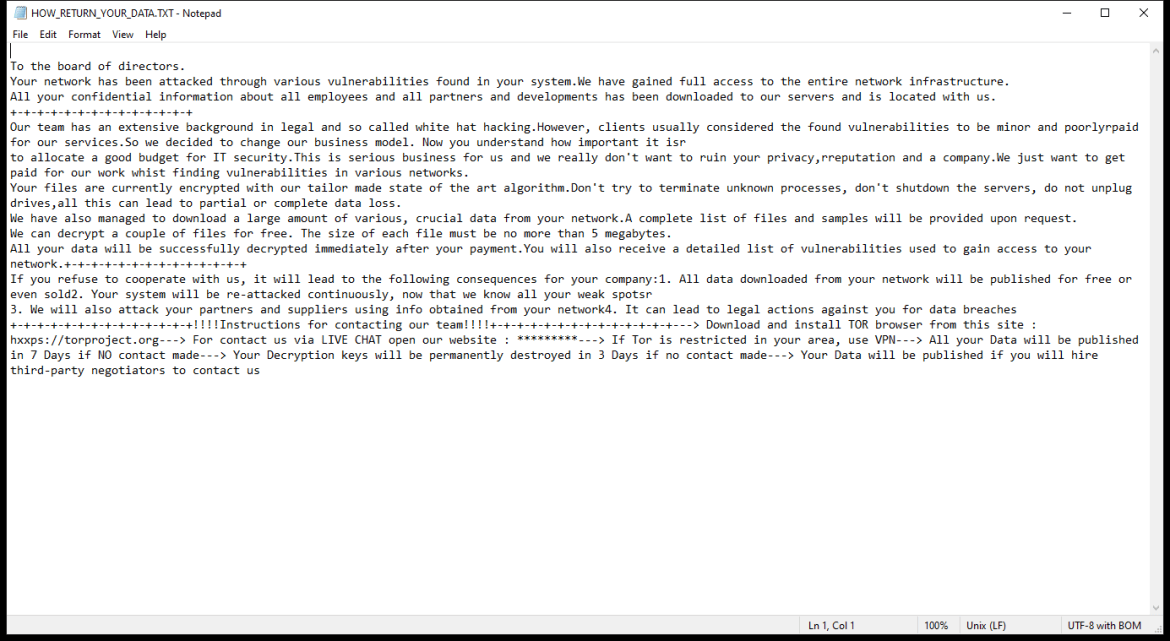
The ransom note created by the 2000USD Ransomware usually appears on the desktop or in folders containing encrypted files. It provides instructions on how to pay the ransom and receive the decryption key.
As of now, there are no decryption tools available for decrypting files encrypted by the 2000USD Ransomware. However, it is recommended not to pay the ransom as there is no guarantee that the cybercriminals will provide the decryption key after receiving the payment.
In case your files have been encrypted by the 2000USD Ransomware, you can try to restore them from a backup if you have one. Additionally, you can seek help from cybersecurity professionals or law enforcement agencies for further assistance.