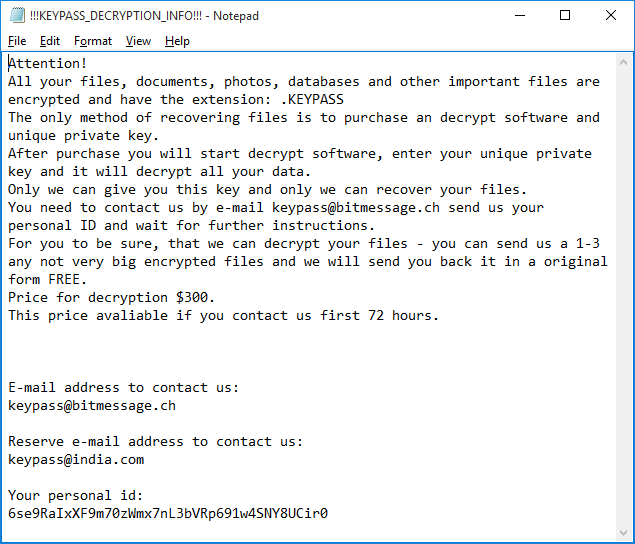
KEYPASS ransomware is a new version of an old STOP ransomware, that have several versions of it. Cyber criminals responsible for this virus are developing new versions in order to increase their revenue. KEYPASS Ransomware can encode important files on a computer. Encryption is blocking any access to the file, that’s why ransomware viruses is critical and considered to be very dangerous. If your computer is infected with KEYPASS ransomware, do not rush to pay for decryption of your files, because cyber criminals are not going to decrypt your files. Still, you may remove KEYPASS ransomware and decrypt .KEYPASS files without paying anything.
Category: Ransomware
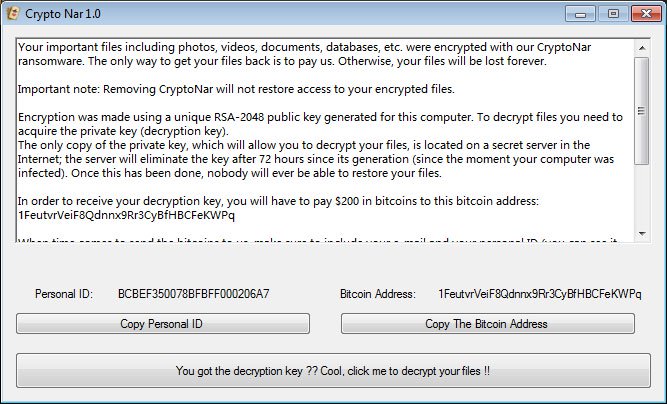
How to remove CryptoNar ransomware and decrypt .cryptoNar files
CryptoNar is a newest ransomware, that came out in the beginning of September, 2018. The virus is developed by someone called CryptoJoker A.E. CryptoNar will encrypt victim’s data with AES encryption algorythms, then ask for money in exchange for decoding. One of the interesting features of CryptoNar ransomware is full and partial types of encryption. This ransomware will add .fully.cryptoNar or .partially.cryptoNar extension. If your files are enciphered, you may use this guide in order to remove CryptoNar ransomware and decrypt .cryptoNar files.
How to remove Good ransomware and decrypt .good files
Good is a ransomware, that came from Scarab ransomware family. Distribution rate of their ransomware viruses is not that big, however these cyber crooks create a lot of different versions of their viruses. Good ransomware is one of the newest viruses. It will encrypt all sensitive files (videos, photos, documents) and ask for ransom in order to recover them. The whole point of ransomware viruses is to get money from a victim. In case your computer is infected with this virus, do not worry, in this guide you may find out how to remove Good ransomware and restore .good files.
How to remove Termite Ransomware and decrypt .aaaaaa files
Termite ransomware is a new crypto-virus, that was reported on August 27, 2018. Termite ransomware is quite unusual ransomware, because it would not ask for any money or do any kind of blackmail. It will encrypt victim’s files though, and the files must be decrypted to be accessed. Here is an encipher workflow: first, it read the original data; then the virus removes it; then creates the encoded files, adding extension .aaaaaa; finally the ransomware writes the encoded files. If you got your PC infected with this virus, use this guide to remove Termite ransomware and decrypt .aaaaaa files.
How to remove Cassetto ransomware and decrypt .cassetto files
Cassetto – is a crypto-virus, that will run AES encryption algorithms on infected computer. After this process, a victim of this virus will find out that all documents, images, text files, videos, audios and other sensitive and important files can not be accessed or opened anymore because of sophisticated encryption. The files can function normally once they are decrypted, but to make this decryption happen cyber criminals demand for ransom. If you got your files encrypted by Cassetto ransomware, let us warn you – do not pay these people, they are likely to ignore their victims. Still, you may get your files back. Learn how to remove Cassetto ransomware and decrypt .cassetto files in this guide.
How to remove CreamPie ransomware and decrypt .[backdata@cock.li].CreamPie files
CreamPie – is a virus, that is able to lock all the personal and important for any user files. It will sneak into victim’s system, start the encoding procedure, then ask for big sum of money as a ransom. Once the payment is done, cyber crooks supposed to do their part of the deal, however there is no guarantee that they would help. The virus itself can be distributed by hacking through an unprotected RDP configuration, email spam and malicious attachments, fraudulent downloads, exploits, web injections, fake updates, repackaged and infected installers. Use this guide to remove CreamPie ransomware and decrypt .[backdata@cock.li].CreamPie files without paying anything.
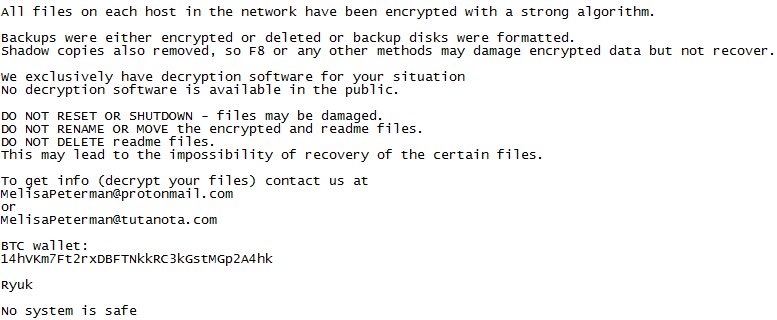
How to remove Ryuk ransomware and recover files
Ryuk ransomware is a crypto-virus, that is developed by Lazarus Group. This group is notorious for their ransomware distribution, they are mainly targeting corporations that are able to pay huge ransom for decryption of their spoiled data. The ransom cost may be from 15 (100’620$) to 50 BTC (335’500$)! A common user may also be the target of Ryuk ransomware attack, that is why this is essential to have a proper anti-virus. If your computer is infected, learn how to remove Ryuk ransomware and decrypt infected files in this guide.
How to remove Kraken Cryptor and decrypt .onion files
Kraken Cryptor is a ransomware, that will encode all the personal files with AES-128/256 (CBC mode), RSA, Salsa20, RC4 encryption algorithms and ask for 0.25 BTC (~1650$) ransom cost in order to decode the encrypted data. The encryption will make any file inaccessible and the fact is that Kraken Cryptor, as any other ransomware from the global net, will target vitally important files like all sorts of documents, photos, videos, audio files and so on. If your computer is infected with this virus and all your files are encrypted with .onion extension, do not contact cyber crooks as it will lead you into big money loss. However, you may use this guide to remove Kraken Cryptor and decrypt .onion files.
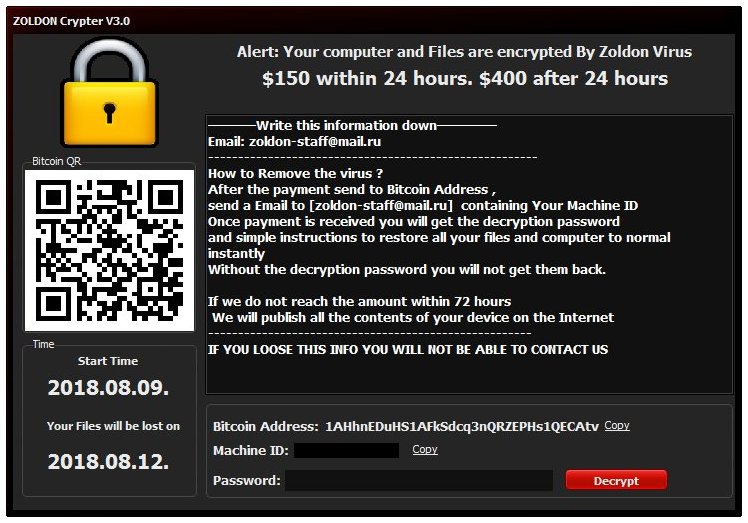
How to remove ZOLDON Crypter V3.0 and restore files
ZOLDON Crypter V3.0 – is a dangerous and fast-spreading virus, that is able to encrypt all the files on victim’s computer and make them unreadable. In order to access these files again user have to pay ransom cost, which is commonly quite huge – in this particular case the cost is about 150$ in BitCoins. If your computer is infected with ZOLDON Crypter V3.0 ransomware, you should not pay for decryption of your files, because there is no guarantee that cyber criminals will ever answer and provide decryption. Still, you may remove ZOLDON Crypter V3.0 ransomware and recover infected files without paying any ransom.
How to remove EvilLocker and decrypt .[evil@cock.lu].EVIL files
EvilLocker – is not a brand new virus, more than that – it is just a version of notorious Everbe ransomware. However the developers of these viruses are eager to go further and infect as many users as they can. The purpose is very simple – more victims, more profit. In order to infect more users cyber crooks drop new versions of EvilLocker ransomware – this one have different ransom note and file extension .[evil@cock.lu].EVIL. However, the way this new version works is quite the same as the old one. EvilLocker will use exploits, botnets, trojans, fake updaters and installers, spam email attachments to get into system. Once it is in a victim’s computer, it will encipher all the important files (documents, photos, videos etc.) and ask for money in order to decrypt them. Let us warn you – there is no guarantee that cyber criminals will help you after the payment. If you have this crypto-virus on your computer, use this guide to remove EvilLocker ransomware and restore .EvilLocker files.


![How to remove CreamPie ransomware and decrypt .[backdata@cock.li].CreamPie files](https://malwarewarrior.com/wp-content/uploads/2018/08/MW-backdata@cock.li_.CreamPie-files.jpg)
![How to remove EvilLocker and decrypt .[evil@cock.lu].EVIL files](https://malwarewarrior.com/wp-content/uploads/2018/08/evil@cock.lu_.EVIL-Extension-Virus.png)