OCEANS Ransomware is a type of malicious software that encrypts files on a computer and demands a ransom to decrypt them. It infects computers through malicious email attachments, software downloads, or exploiting vulnerabilities in the system.
When OCEANS Ransomware encrypts files, it typically adds extensions such as “.oceans” or “.oceanlocked” to the filenames. It uses strong encryption algorithms like AES to lock the files, making them inaccessible without the decryption key.
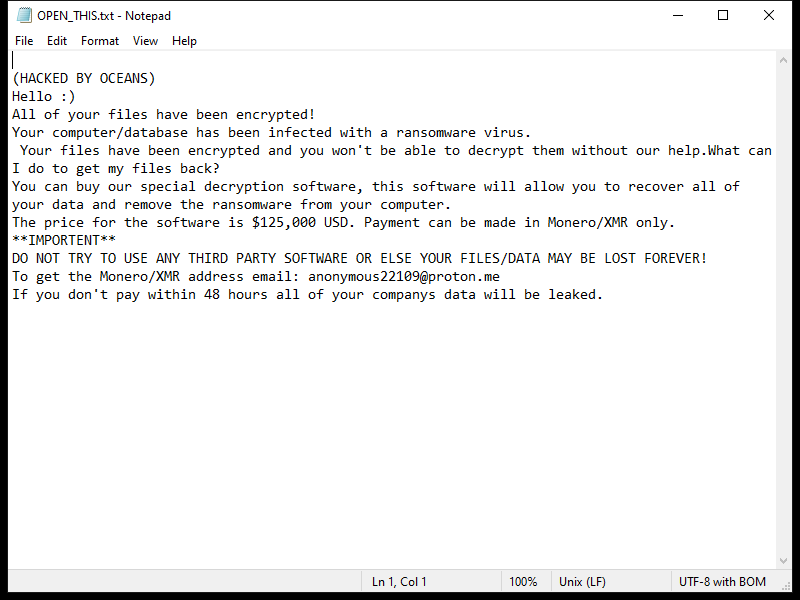
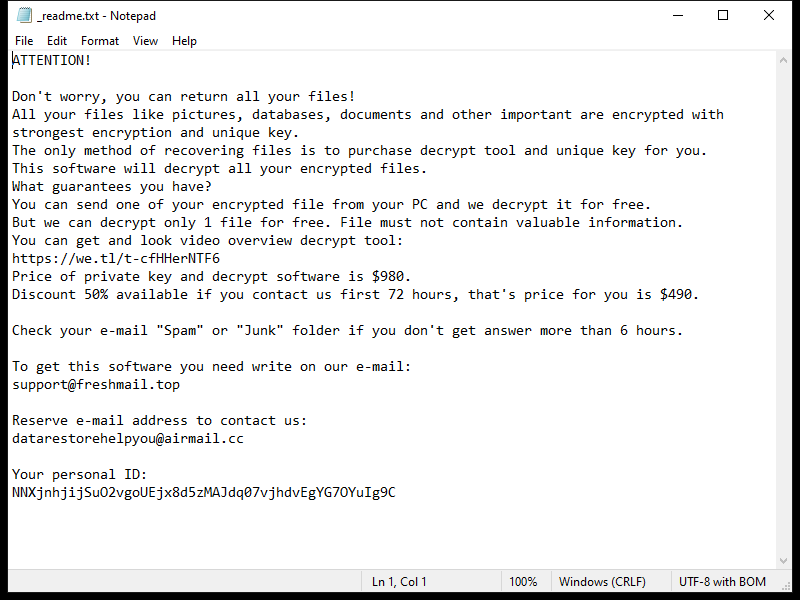
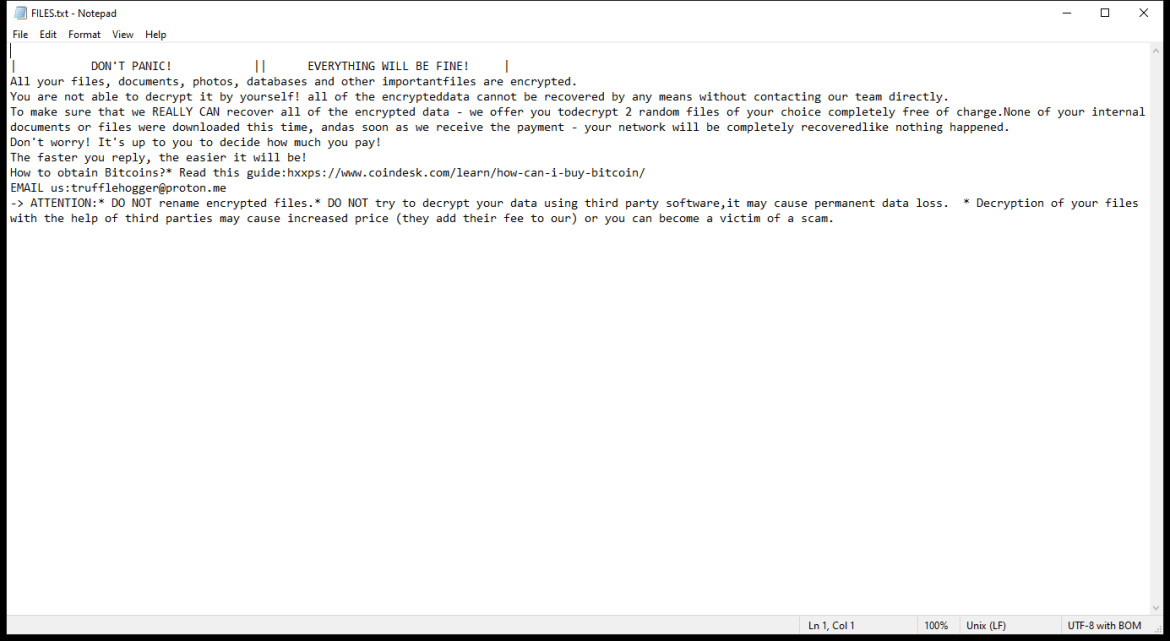
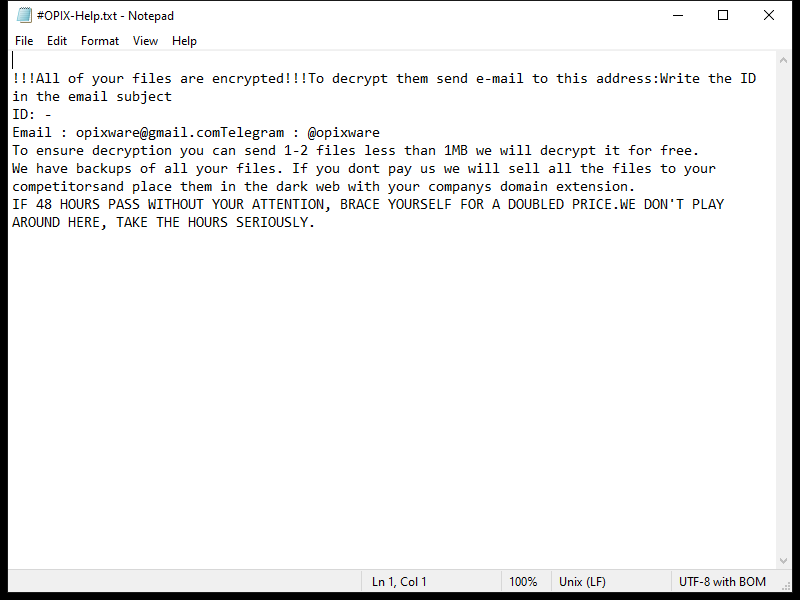
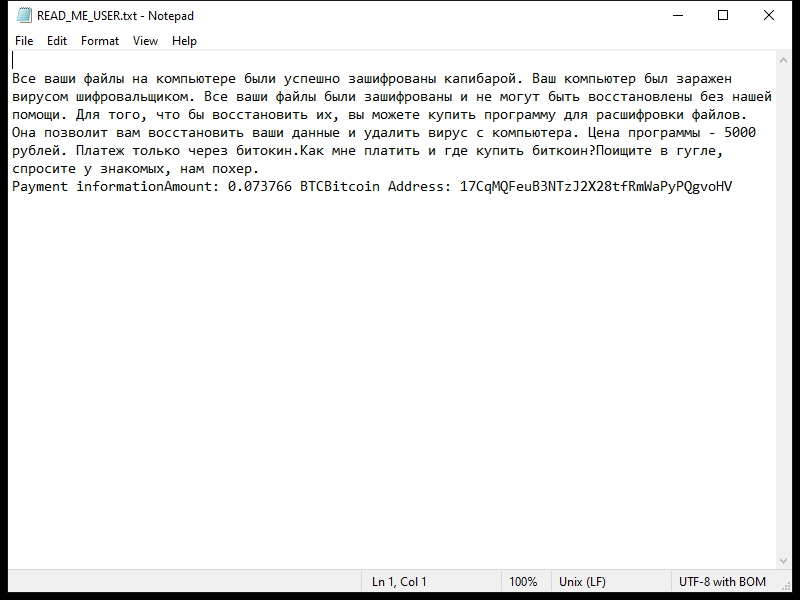
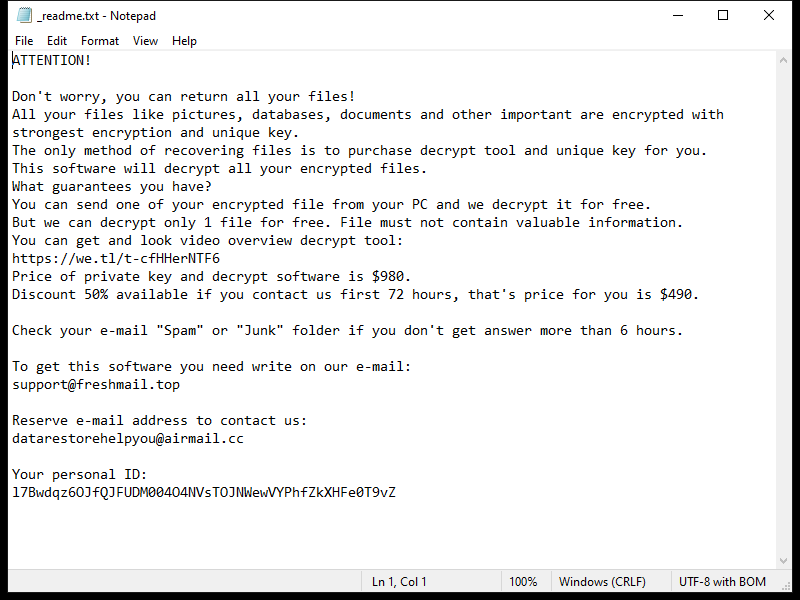
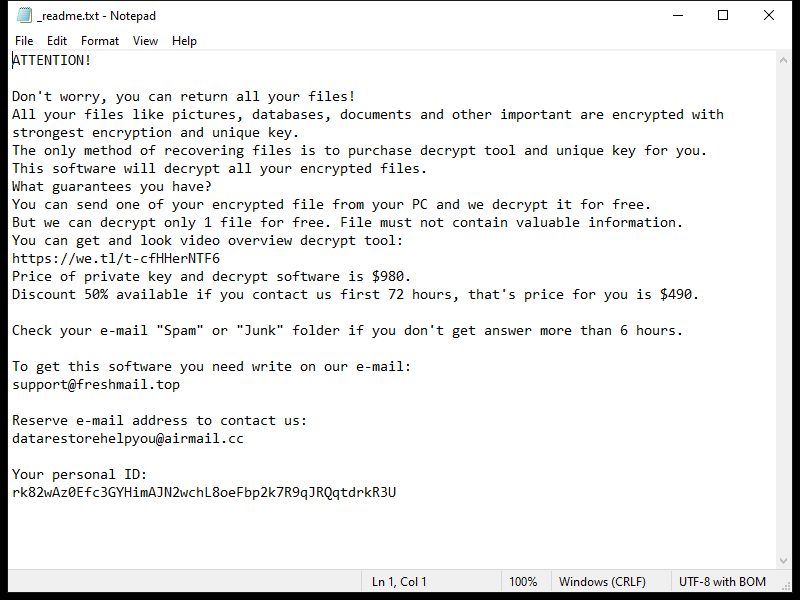
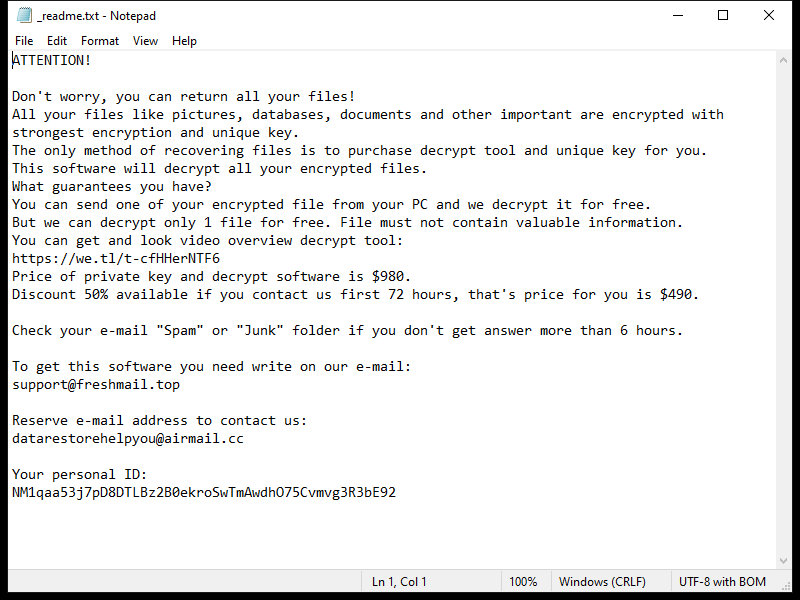
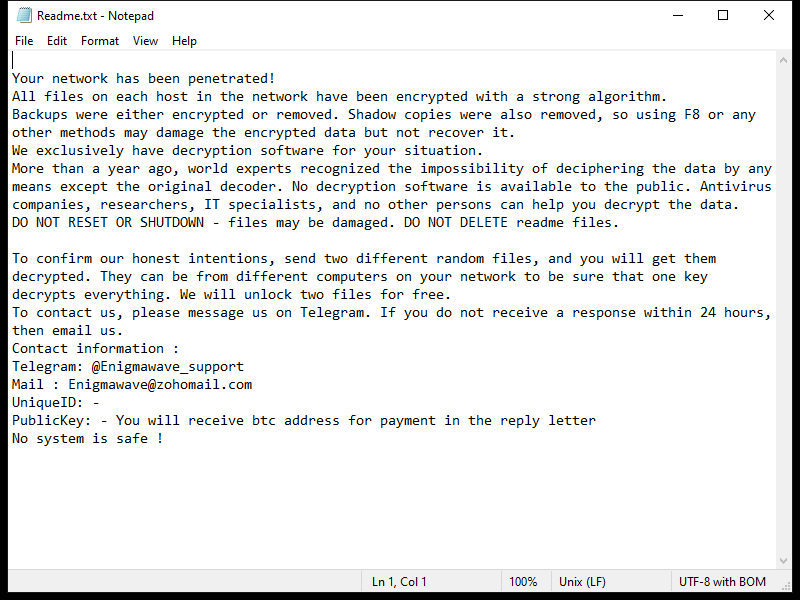
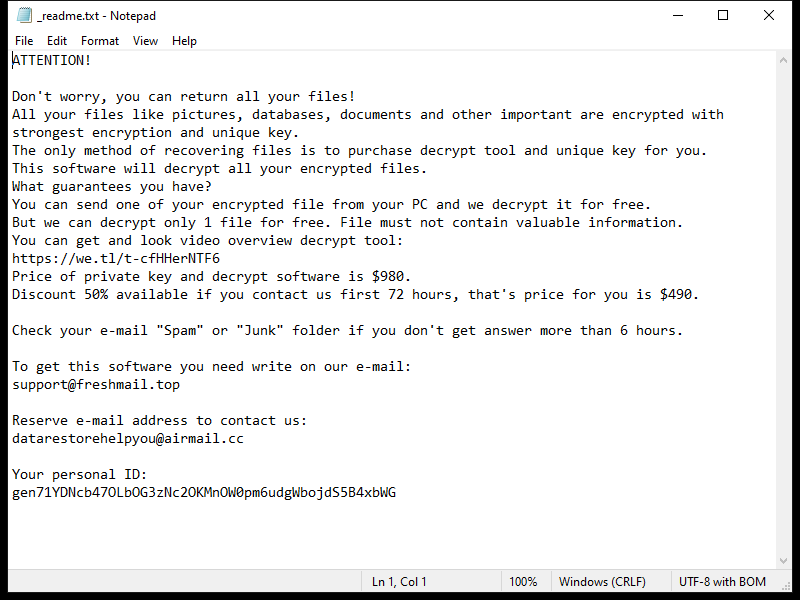
After encrypting the files, OCEANS Ransomware creates a ransom note usually named “HOW-TO-DECRYPT-FILES.txt” or similar, which contains instructions on how to pay the ransom in exchange for the decryption key. This note is usually placed on the desktop or in folders containing encrypted files.
Unfortunately, there are no decryption tools available for OCEANS Ransomware at the moment. However, some victims have reported success in decrypting their files by restoring them from backups or using data recovery software. It is important to note that paying the ransom does not guarantee that you will receive the decryption key, so it is not recommended.
To protect against OCEANS Ransomware and similar threats, it is important to regularly back up your files, keep your software updated, and be cautious when opening email attachments or downloading files from unknown sources.