SHINRA Ransomware is a type of malware that encrypts files on a victim’s computer, making them inaccessible until a ransom is paid. It typically infects computers through malicious email attachments, fake software updates, or exploit kits.
Once SHINRA Ransomware infects a computer, it adds a random file extension to encrypted files to make them unopenable. The specific file encryption algorithm used by SHINRA Ransomware may vary, but common encryption methods include RSA or AES.
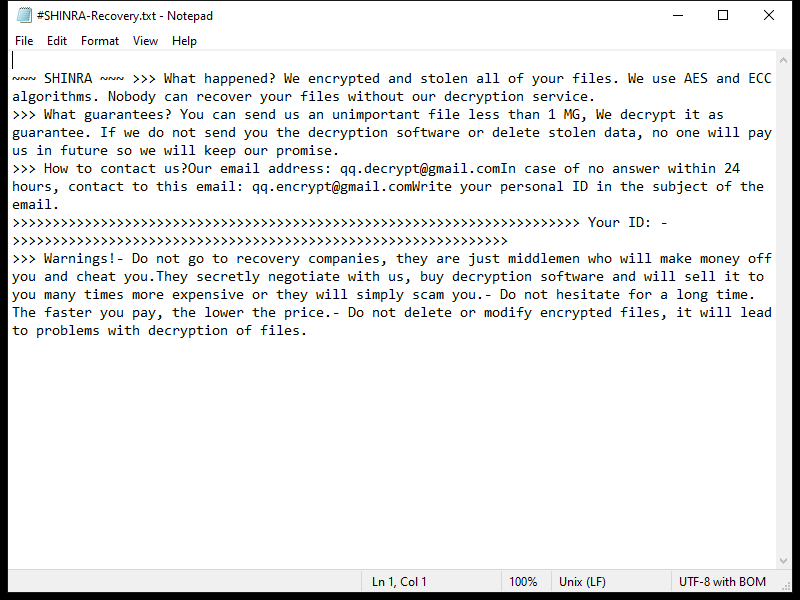
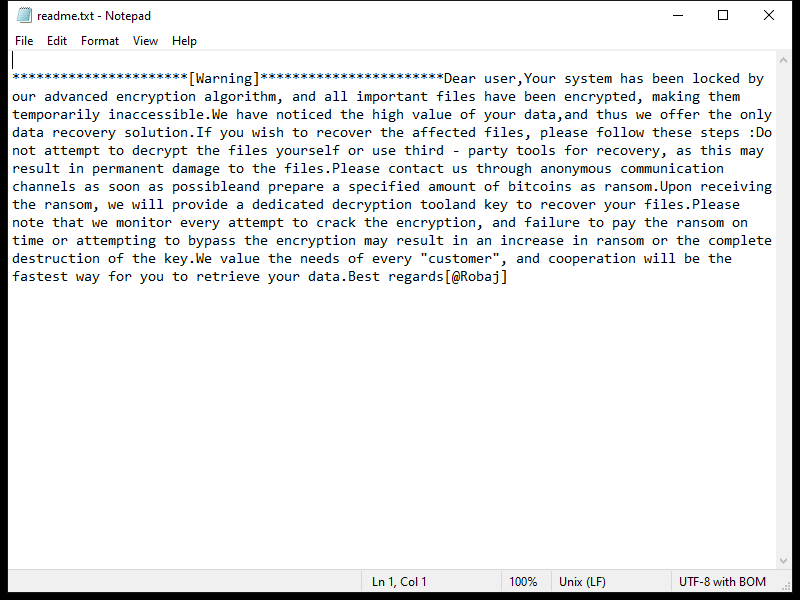
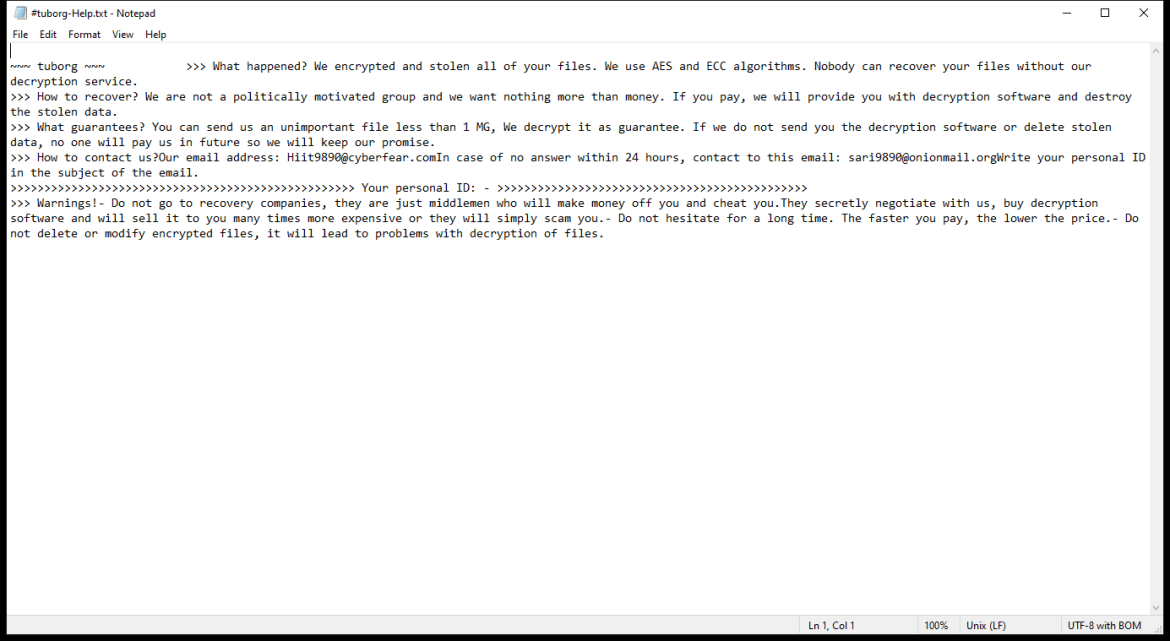
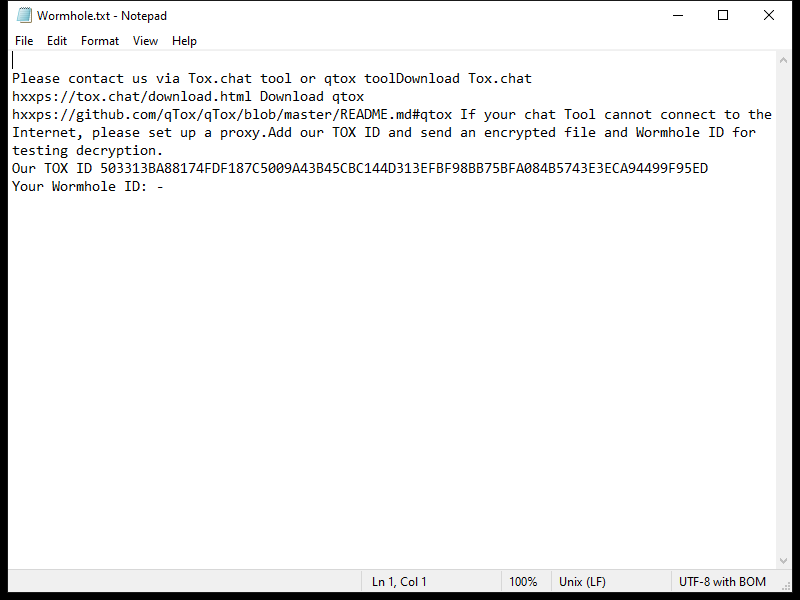
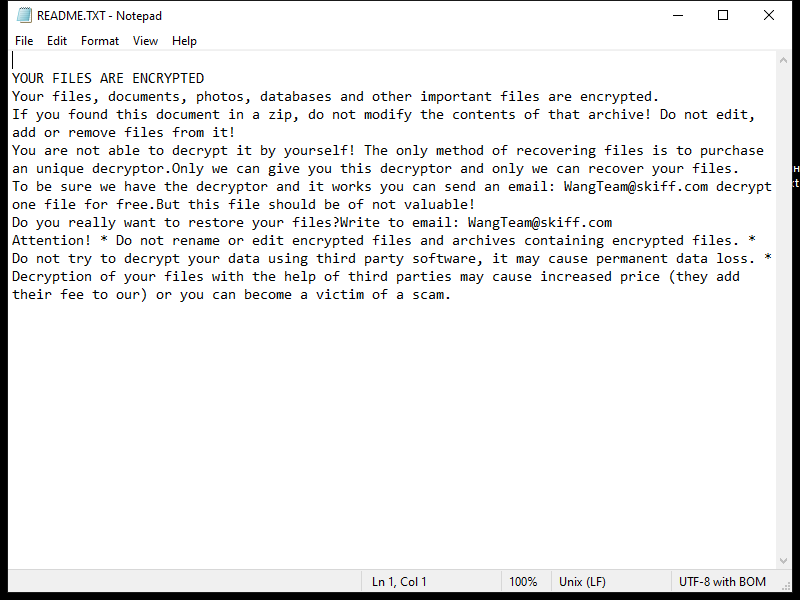
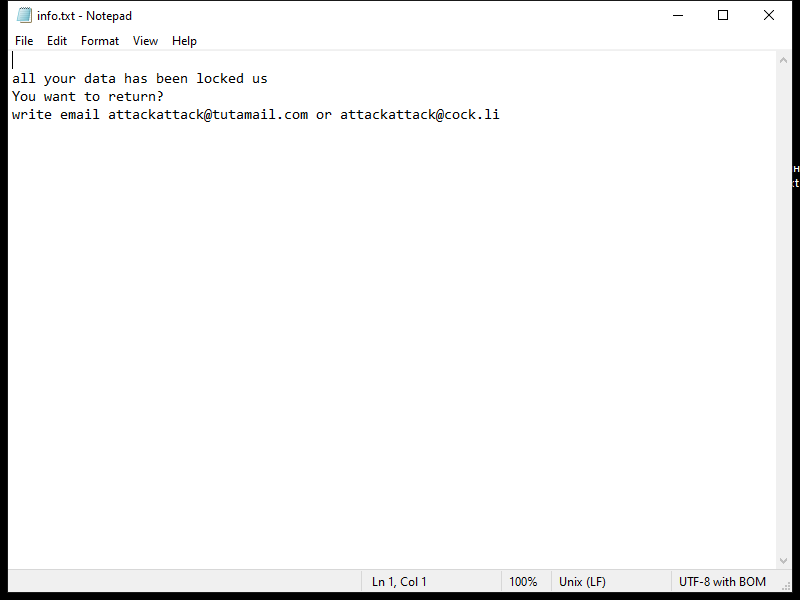
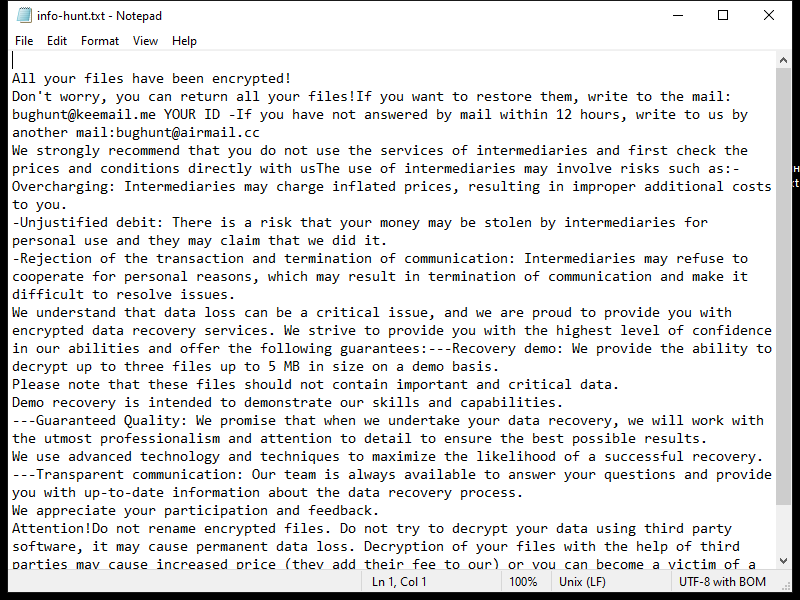
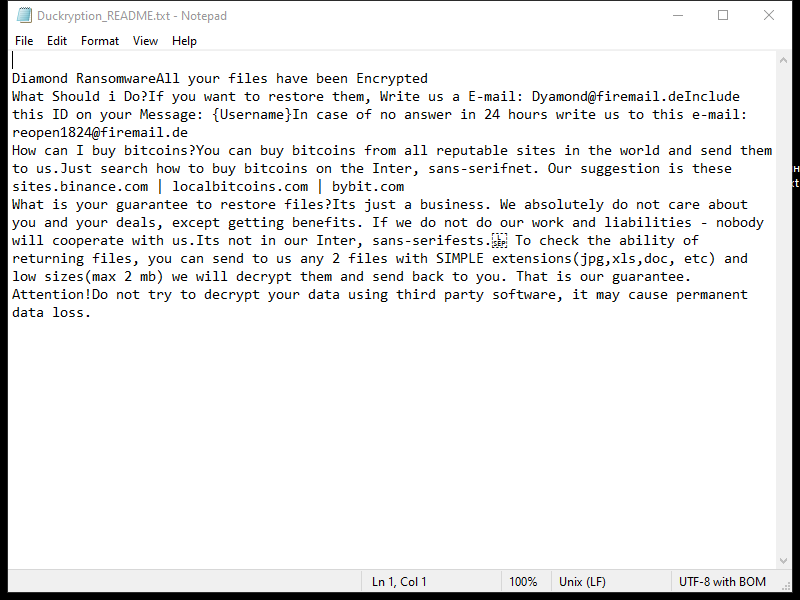
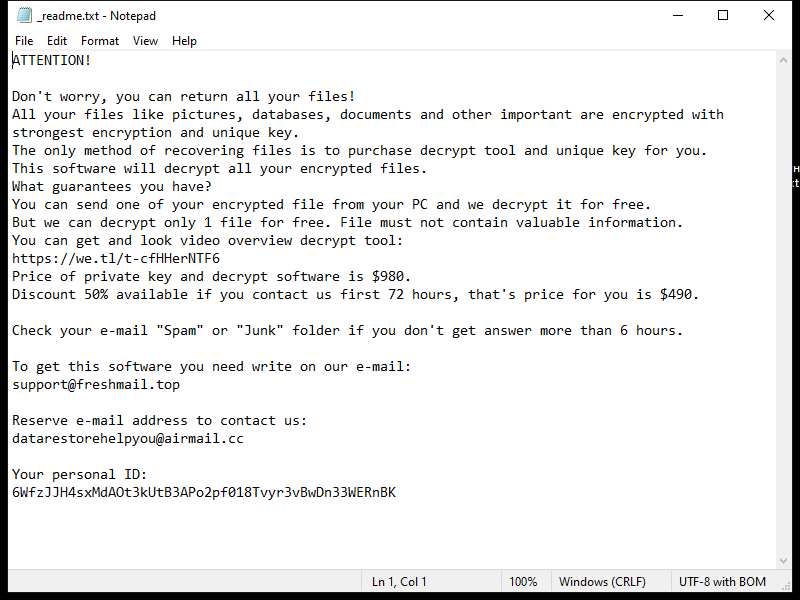
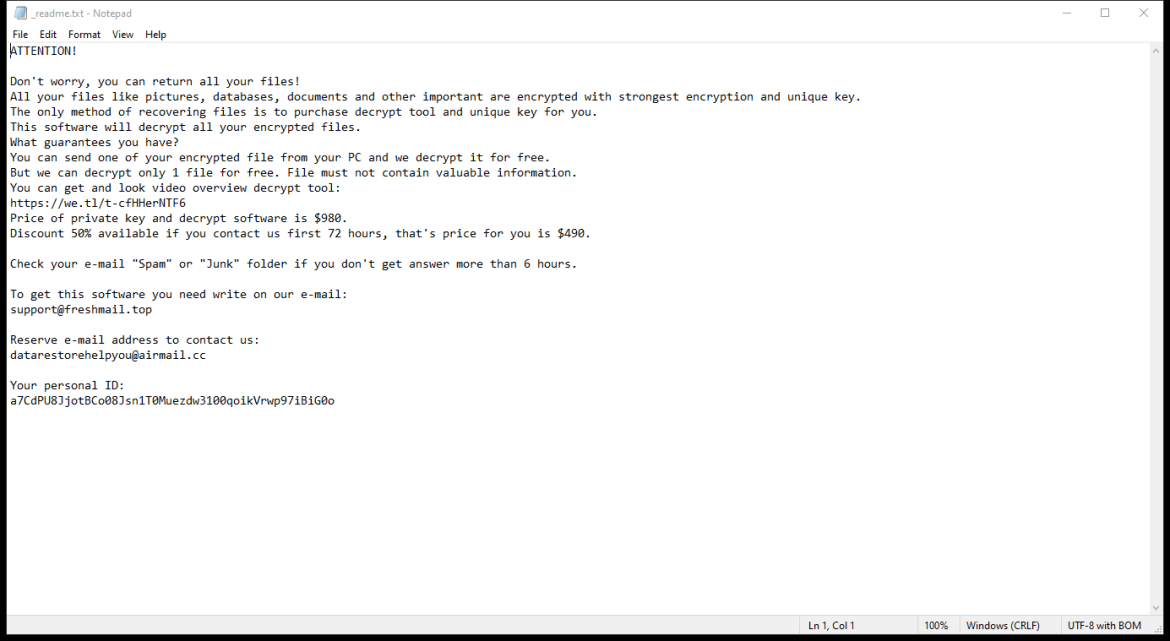
The ransomware typically creates a ransom note in the form of a text file or pop-up window on the infected computer, instructing the victim on how to pay the ransom to decrypt their files. This ransom note is usually placed in folders containing encrypted files or on the desktop.
As of now, there are no known decryption tools available for SHINRA Ransomware. However, victims should not pay the ransom as there is no guarantee that the files will be decrypted even after payment. Instead, victims can try to restore their files from a backup or use third-party data recovery tools.
It is important to regularly back up important files to prevent data loss in case of a ransomware attack. Additionally, users should exercise caution when opening email attachments or downloading software from untrusted sources to prevent malware infections.