What is InfoDot Ransomware InfoDot ransomware is a cryptovirus that encrypts user files and extorts money as a ransom. InfoDot ransomware encrypts files using AES-256
Category: Ransomware
How to remove Masked Ransomware and decrypt .masked files
What is Masked Ransomware Masked is another creation of scammers who work in the field of encryption of user data using a multi-stage algorithm, the
How to remove Nols Ransomware and decrypt .nols files
What is Nols Ransomware Nols ransomware is a prominent representative of the STOP (Djvu) cryptovirus family, which has recently spread quite widely around the world.
How to remove Werd Ransomware and decrypt .werd files
What is Werd Ransomware Surely, many users have already heard about the intrigues of attackers who wrote a whole family of cryptoviruses called STOP (Djvu).
How to remove Kiss Ransomware and decrypt .kiss files
What is Kiss Ransomware Kiss ransomware is the next version of cryptoviruses aimed at encrypting user files (photos, videos, audio and much more) and extorting
How to remove Sun Ransomware and decrypt .sun files
What is Sun Ransomware Today in this article we will analyze in detail what Sun ransomware is and how to remove Sun ransomware from your
How to remove Leto Ransomware and decrypt .leto files
What is Leto Ransomware Leto ransomware is a cryptovirus that encrypts user data using a multi-stage algorithm. Genealogically, cryptovirus belongs to the STOP (DJVU) family.
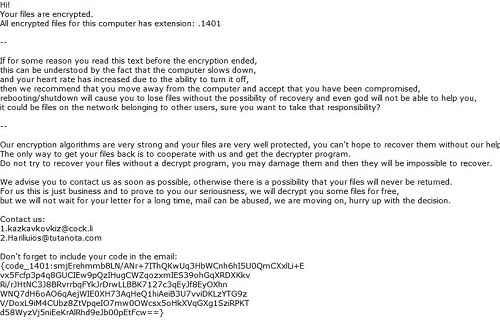
How to remove Kazkavkovkiz Ransomware and decrypt your files
What is Kazkavkovkiz Ransomware Kazkavkovkiz ransomware is a cryptovirus threat that is becoming more dangerous every day. Kazkavkovkiz ransomware encrypts the data in the user’s
How to remove MedusaLocker Ransomware and decrypt .encrypted files
What is MedusaLocker Ransomware Today we will analyze in detail what MedusaLocker ransomware is and how to remove MedusaLocker ransomware from your system. MedusaLocker ransomware
How to remove Cobain Ransomware and decrypt .cobain files
What is Cobain Ransomware Cobain ransomware is a new creation of attackers working in the field of data encryption for the subsequent extortion of money

![How to remove InfoDot Ransomware and decrypt .info@sharebyy[dot]com and .info@mymail9[dot]com](https://malwarewarrior.com/wp-content/uploads/2019/10/infodot-ransomware-mw.png)