Global PC Cleaner Pro is a potentially unwanted program (PUP) that is often categorized as a rogue system optimization tool. This software purports to enhance your computer’s performance by eliminating unnecessary files, fixing registry errors, and boosting speed. However, its real intention is far from beneficial. Rather than improving system performance, Global PC Cleaner Pro often results in system slowdowns and intrusive advertising. This program employs scare tactics, displaying exaggerated scan results and false positives to convince users that their computer has severe performance or security issues, thereby prompting them to purchase the full version of the program. The infection process of Global PC Cleaner Pro is quite subtle. It primarily spreads via bundling, a deceptive software distribution technique. Bundling entails packing several programs into a single software package, allowing the unwanted program to be installed alongside the desired software unknowingly. When users install software from freemium sites or choose the “Recommended” or “Quick” installation settings, they inadvertently consent to installing additional programs like Global PC Cleaner Pro. Once installed, this rogue software initiates system scans automatically and presents the user with alarming results, pushing for the purchase of its premium version. It is important to remember that such programs are designed to exploit users’ fears about their computer’s health, and their claims are rarely accurate. Always ensure to download software from official sources and choose the “Custom” or “Advanced” installation to avoid such unwanted programs.
Category: Unwanted Programs
How to remove PC Booster
PC Booster, in essence, is a type of software that is marketed as a tool to enhance computer performance. It purports to optimize your Personal Computer (PC) by cleaning up junk files, fixing registry errors, and improving overall system speed. However, contrary to these claims, PC Booster is often classified as Potentially Unwanted Program (PUP) due to its malevolent behavior. This software, rather than improving your system’s performance, can potentially lead to various computer-related issues, including system slowdowns, intrusive advertisements, and unauthorized changes to your system settings. PC Booster infects computers mainly through bundled installations. This typically occurs when a user installs a free software package without fully understanding what it entails. The PC Booster software is often hidden within the ‘Advanced’ or ‘Custom’ installation settings of these free software packages. Once installed, it can start causing various problems. Moreover, PC Booster can infect computers by employing deceptive advertising techniques. For instance, it may display pop-up alerts warning about imaginary PC issues and offering to fix them. When the user clicks on these alerts, the PC Booster software gets downloaded and installed. Thus, it is always advisable to exercise caution while installing new software and to steer clear of suspicious pop-up ads to prevent PC Booster and similar programs from infecting your computer.
How to remove Personalized Notepad with Reminders
Personalized Notepad with Reminders is a seemingly harmless application that claims to enhance productivity and organization by providing users with a digital notepad and reminder system. It appears as a legitimate software solution, often offering customizable features to suit individual preferences. Users are enticed by the idea of an efficient and personalized note-taking tool, making them more susceptible to falling victim to this deceitful software. However, beneath its innocent facade, Personalized Notepad with Reminders harbors malicious intentions. Once installed on a computer, it gains unauthorized access to personal data, monitors online activities, and even modifies system settings without the user’s consent. It may also display intrusive advertisements or redirect users to suspicious websites, further compromising computer security and user privacy.
How to remove SAproduct
SAproduct is a potentially unwanted program (PUP) that is classified as adware. It is known for its intrusive behavior, which includes delivering unwanted ads, redirecting browser searches to dubious websites, and gathering users’ browsing data. SAproduct is typically disguised as a useful tool or software that offers features such as improving computer performance, blocking unwanted ads, or protecting the user’s privacy. However, once installed, it begins to perform activities that can compromise the user’s privacy and security. The infection process of SAproduct typically involves a deceptive marketing method known as “bundling.” It is often bundled with free software that users download from the internet. During the software installation process, the user might unknowingly agree to install additional programs, one of which could be SAproduct. In some instances, users may be tricked into downloading SAproduct through a misleading pop-up ad or a fake software update notification. Once installed, SAproduct starts displaying intrusive ads, redirecting searches, and collecting user data, all of which can lead to various privacy and security issues. Therefore, it is essential for users to be cautious when downloading and installing software from the internet to avoid potentially unwanted programs like SAproduct.
How to remove OneSafe PC Cleaner
OneSafe PC Cleaner is a computer optimization tool that claims to improve the performance of your computer by scanning for and removing junk files, unnecessary registry entries, and other redundant items. However, it is essential to note that this program is often categorized as potentially unwanted software (PUS) or a potentially unwanted program (PUP). This is primarily due to its deceptive distribution methods and the misleading information it provides about the status of your computer. In many cases, OneSafe PC Cleaner tends to exaggerate the level of threat or issues present in the system, creating an illusion of severe problems to persuade users into purchasing its full version. The infiltration of OneSafe PC Cleaner into computers typically involves software bundling, a common technique used by many PUP developers. This method entails packaging the unwanted program with other popular free software, so users inadvertently download and install the PUP while installing the desired software. Users may also unwillingly download OneSafe PC Cleaner from deceptive pop-up advertisements or compromised websites that trick visitors into believing their computers are at risk. Once installed, OneSafe PC Cleaner starts performing unnecessary system scans and displaying alarming results to create a sense of urgency, encouraging users to buy its premium version. Therefore, although it is not a virus or malware, the manipulative tactics employed by OneSafe PC Cleaner classify it as a potentially unwanted program.
How to remove PC HelpSoft Driver Updater
PC HelpSoft Driver Updater is a system optimization tool designed to manage your computer’s drivers. It operates as an automated tool that scans your computer to identify outdated or missing drivers, subsequently updating them to improve the system’s performance and stability. This software claims to significantly enhance your PC’s functionality by ensuring its drivers are up-to-date, thereby reducing system crashes and improving overall performance. However, despite its utility-focused facade, PC HelpSoft Driver Updater is often categorized as potentially unwanted software (PUS). This categorization is due to its intrusive behavior, as it frequently lands on computer systems without the user’s explicit consent. It mainly infects computers through bundling, a marketing strategy used by many free software providers. In this strategy, the PC HelpSoft Driver Updater comes as an additional package or a ‘recommended application’ alongside another software that the user intends to download. As a result, it often gets installed unbeknownst to the user, leading to unwanted changes in the system. Furthermore, once installed, it tends to perform automatic system scans and generate alarming results concerning outdated drivers, compelling the user to purchase its full version for driver updates. This invasive behavior and the deceptive scare tactics used to encourage purchases are key reasons why PC HelpSoft Driver Updater is often deemed undesirable.
How to remove PCHelpSoftUpdate
PCHelpSoftUpdate is a software updater tool developed by PCHelpSoft, a company that specializes in providing various system optimization and maintenance utilities. It is designed to streamline the process of updating software applications installed on a computer, ensuring that users have the latest versions with enhanced features, bug fixes, and security patches. PCHelpSoftUpdate is intended to simplify the task of manually checking for and installing updates by automating the process, saving users time and effort.
While PCHelpSoftUpdate itself is not inherently malicious, it can inadvertently become a conduit for potentially unwanted programs (PUPs) or even more harmful malware infections. One of the common ways PCHelpSoftUpdate can infect computers is through software bundling. Some software developers employ deceptive techniques by bundling PCHelpSoftUpdate with their applications, often without the user’s knowledge or explicit consent during installation. Consequently, users may unknowingly install PCHelpSoftUpdate alongside the desired software, leading to unintended consequences.
How to remove Haenkyouv.space
What Is Haenkyouv.space? Haenkyouv is persistent malware that attacks your device with persistent pop-ups that appear out of the blue, covering the content of a
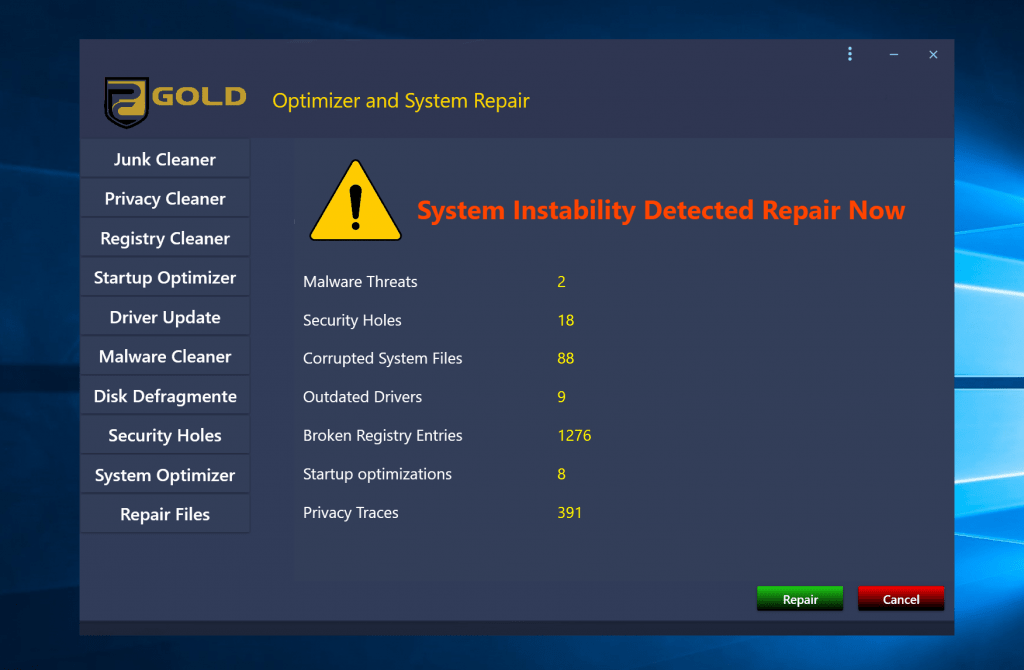
How to remove PC Gold Optimizer and System Repair
What is PC Gold Optimizer and System Repair PC Gold Optimizer and System Repair is a potentially unwanted program that could cause irreparable harm to
How to remove Mac Fixer Pro from Mac
What is Mac Fixer Pro In this article, we will analyze in detail what is Mac Fixer Pro and how to remove it from the