How to remove EnumeratorProgress (Mac)
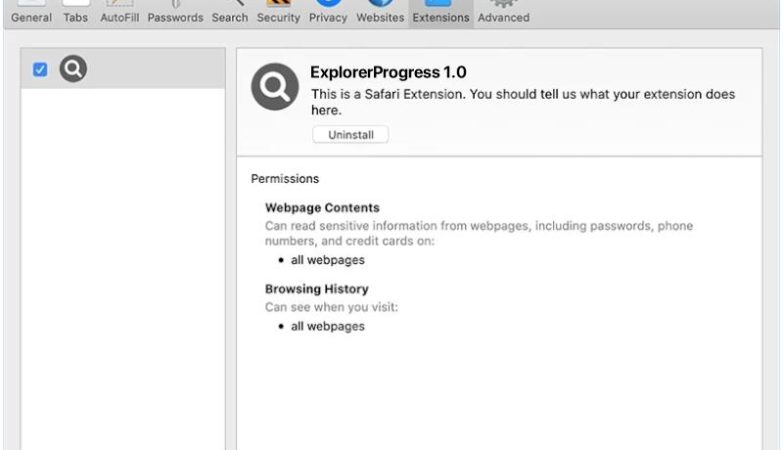
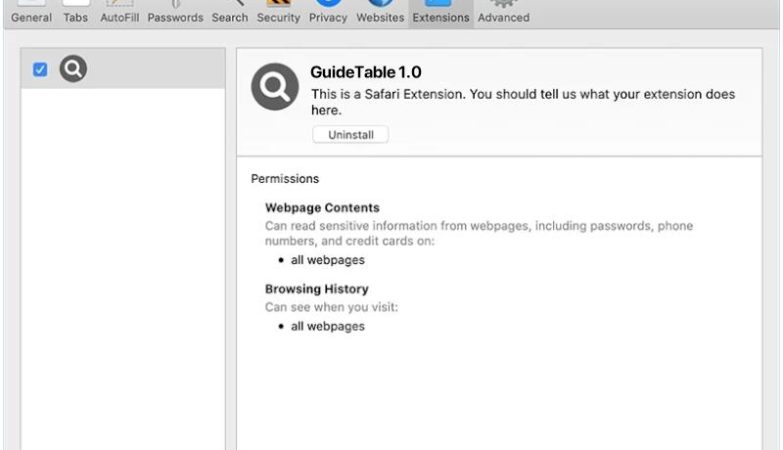
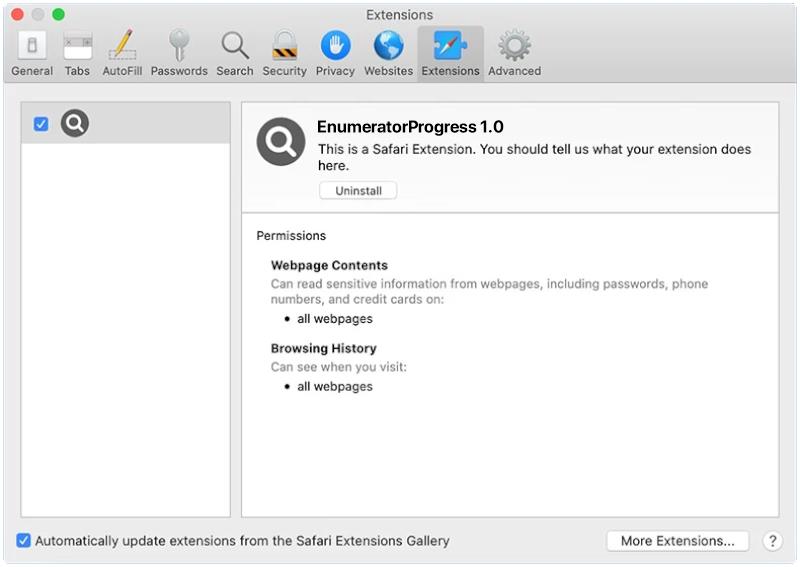
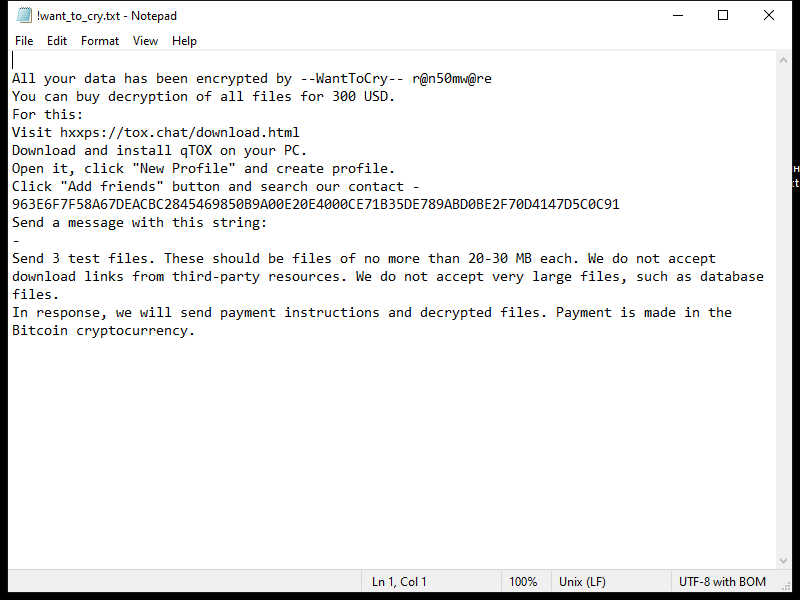
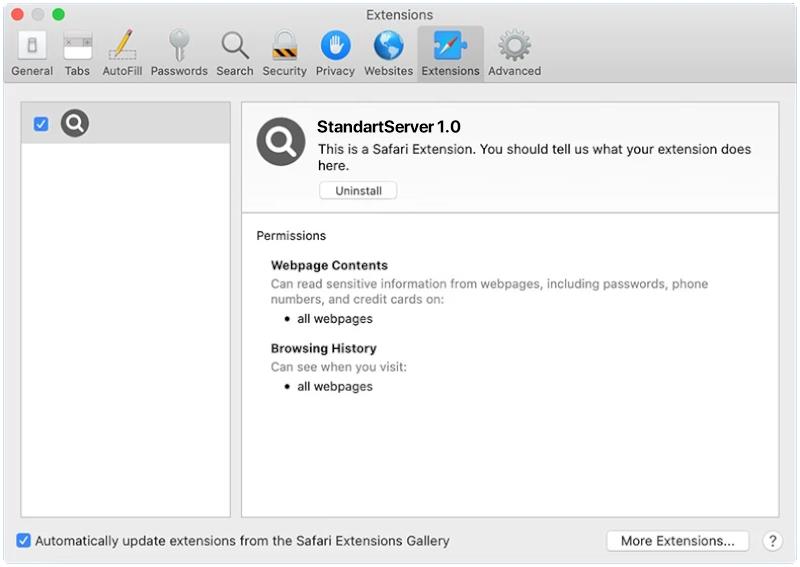
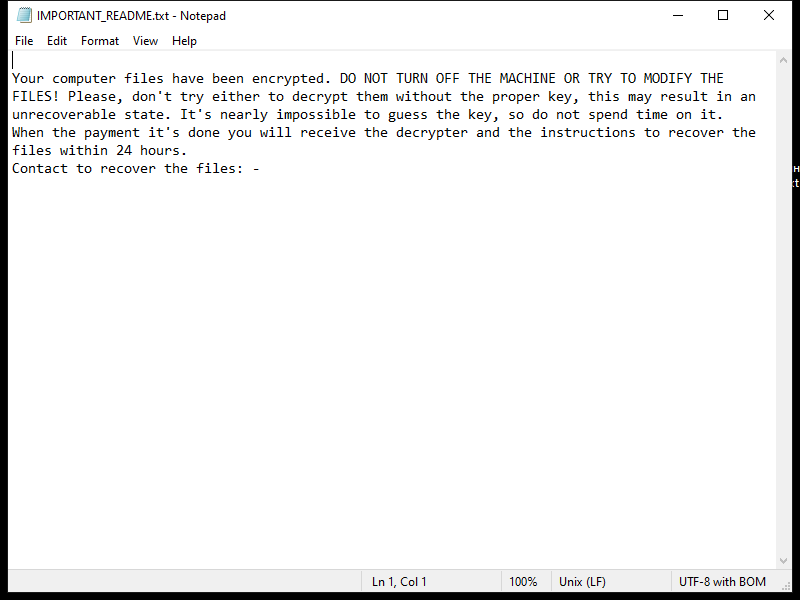
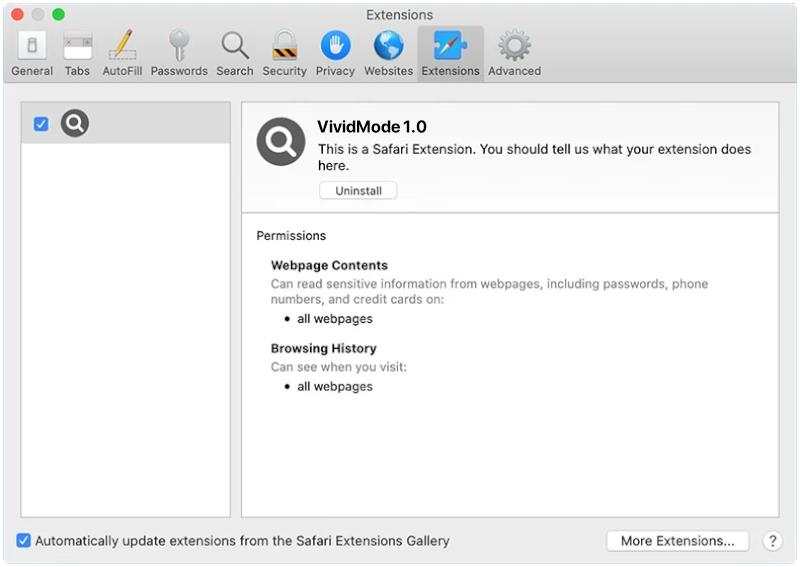
EnumeratorProgress is a potentially unwanted program (PUP) that infects Mac computers by bundling itself with other software that users download from the internet. Once installed, EnumeratorProgress displays intrusive pop-up ads, banners, and coupons on the user’s browser, causing disruptions to their browsing experience. It may also collect browsing data and personal information to display targeted ads to the user.
This type of adware can slow down the performance of the infected Mac and may also track the user’s online activities without their consent. EnumeratorProgress can be difficult to remove manually, as it may hide deep within the system files. Users are advised to use reputable anti-malware software to scan and remove EnumeratorProgress from their Mac to prevent further infections and protect their privacy and security.