How to remove Brain Gym Pro
Brain Gym Pro is a type of adware that infects computers and browsers, causing unwanted advertisements to appear. Adware, short for advertising-supported software, is designed to display advertisements on a user’s device. Brain Gym Pro adware specifically targets computers and browsers, aiming to generate revenue for its creators by displaying intrusive and often misleading ads.
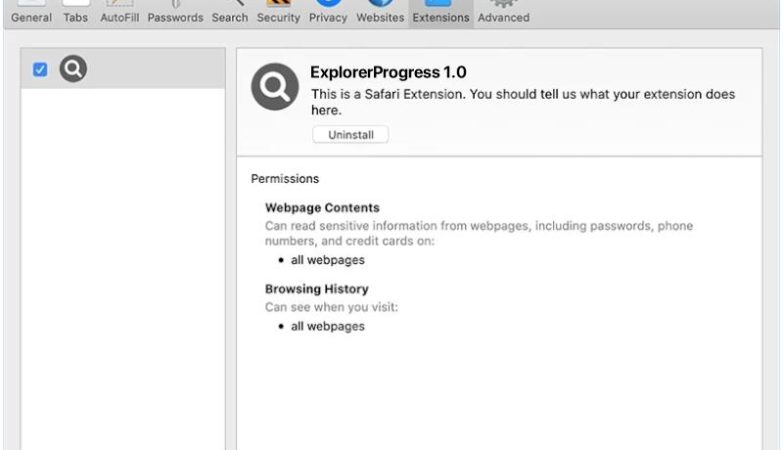
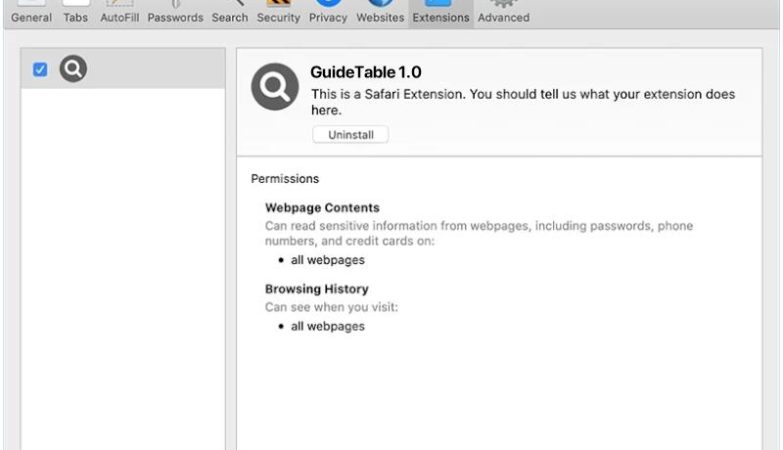
To infect computers and browsers, Brain Gym Pro adware typically employs deceptive tactics. It can be distributed through various channels, such as software bundles, freeware, or malicious websites. Users may unknowingly download and install the adware when they download and install other software or visit compromised websites. Once installed, Brain Gym Pro adware modifies browser settings and injects code into web pages to display advertisements. These ads may appear as pop-ups, banners, or in-text links, disrupting the user’s browsing experience and potentially leading to further malware infections if clicked upon.
It is important for users to be cautious when downloading and installing software from the internet to avoid inadvertently installing adware like Brain Gym Pro. It is recommended to only download software from official and reputable sources. Regularly updating antivirus software and performing system scans can also help detect and remove adware infections. Additionally, users should be cautious when clicking on ads and links, especially if they appear suspicious or come from unknown sources.