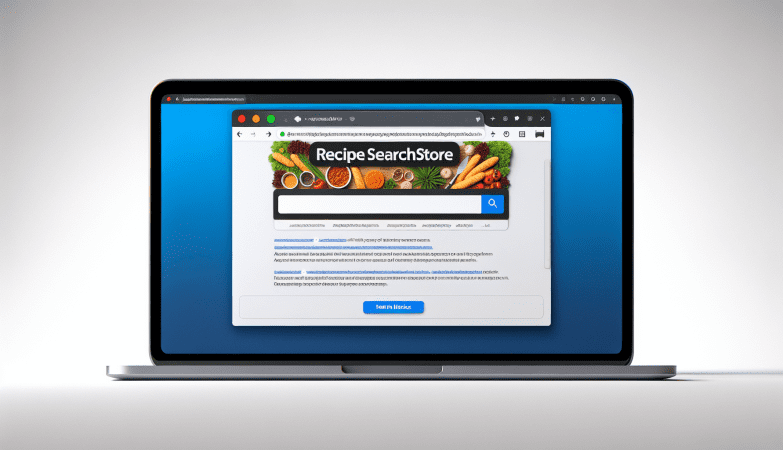
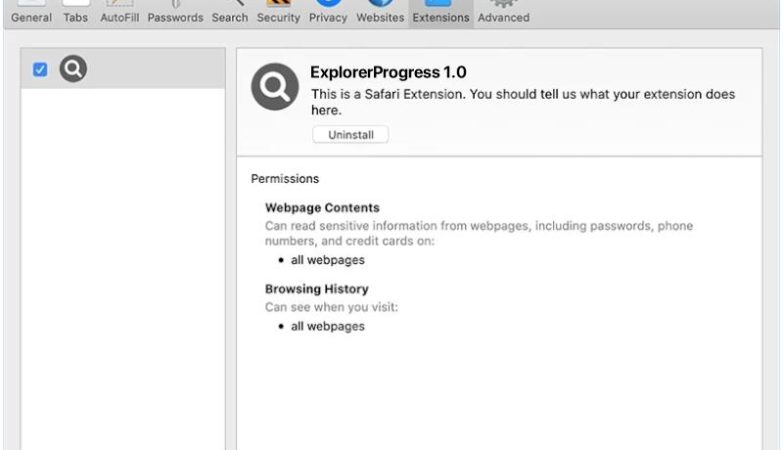
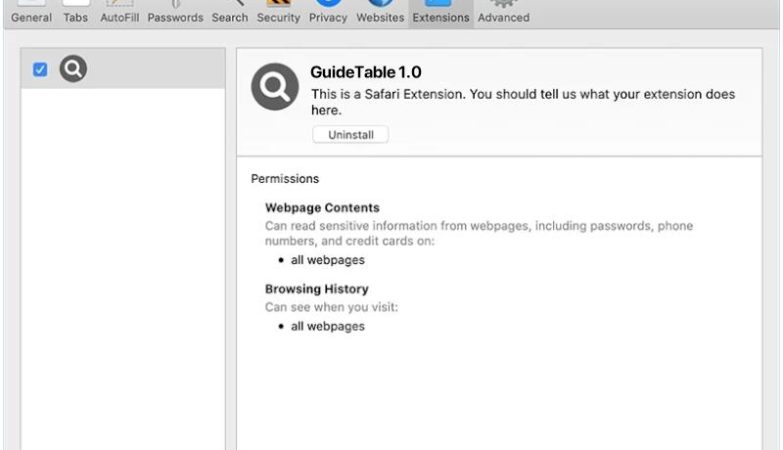
How to remove GlanceHonest (Mac)
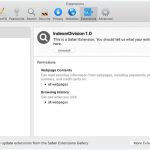
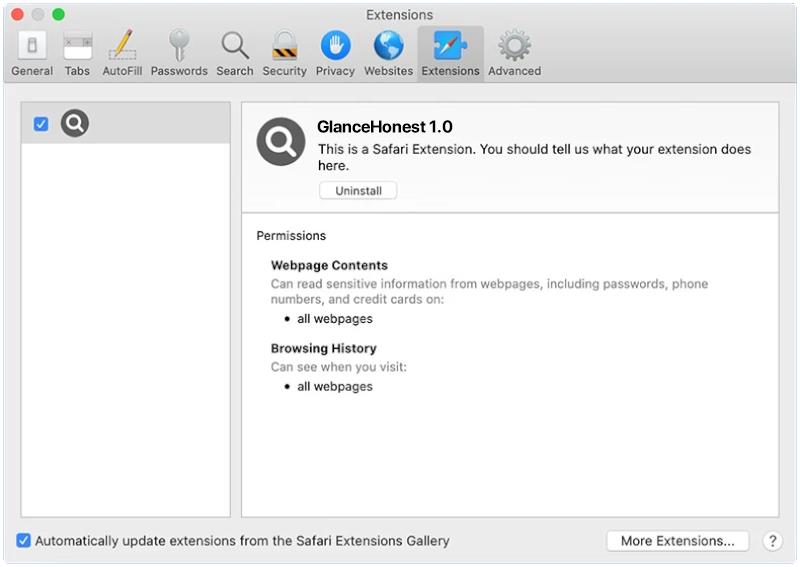
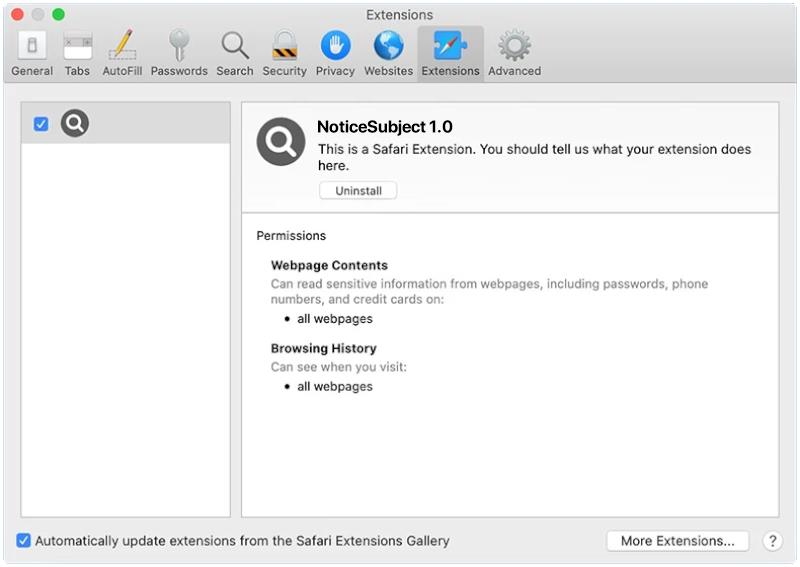
GlanceHonest is a type of potentially unwanted program (PUP) that specifically targets Mac computers. It is categorized as adware, which means its main purpose is to generate revenue for its creators through aggressive advertising techniques. GlanceHonest typically enters a Mac system bundled with other software, often downloaded from unreliable sources or through deceptive advertisements. Once installed, it starts displaying various types of advertisements, including pop-ups, banners, and in-text ads, which can be quite intrusive and annoying for users.
GlanceHonest infects Mac systems by exploiting vulnerabilities in the operating system or by tricking users into downloading and installing it unknowingly. It often comes bundled with freeware or shareware applications that users may download from third-party websites. In some cases, it may also be distributed through malicious advertisements that prompt users to click on them, leading to the unintentional installation of GlanceHonest. Additionally, it can also be spread through fake software updates or by exploiting security loopholes in outdated software versions. Mac users should exercise caution when downloading software from the internet and ensure they only download from trusted sources to prevent the infection of GlanceHonest or other similar adware programs.