How to stop Sigrid Trust Rim Foundation email scam
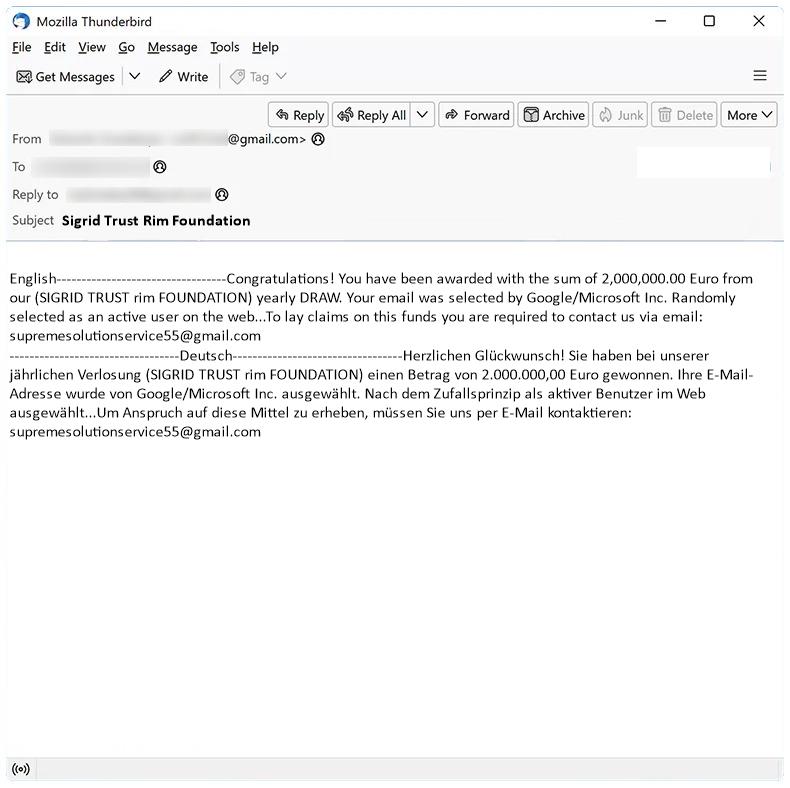
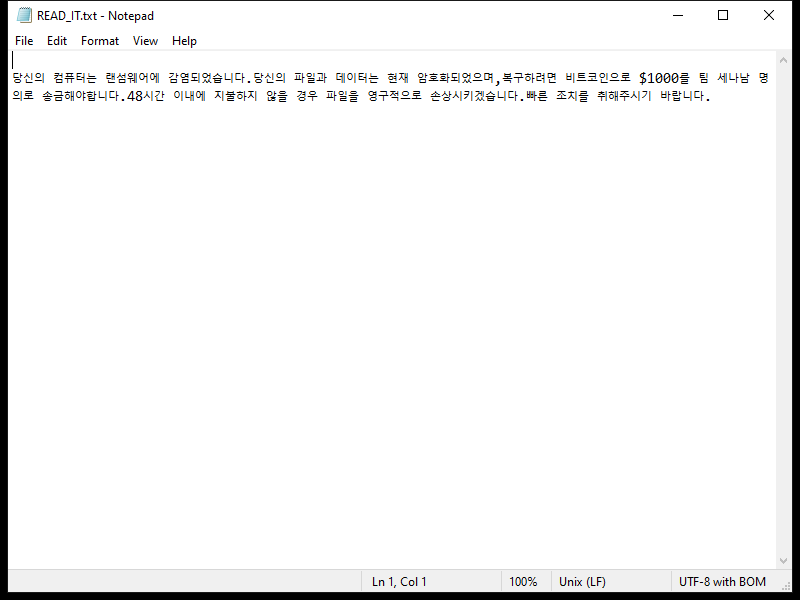
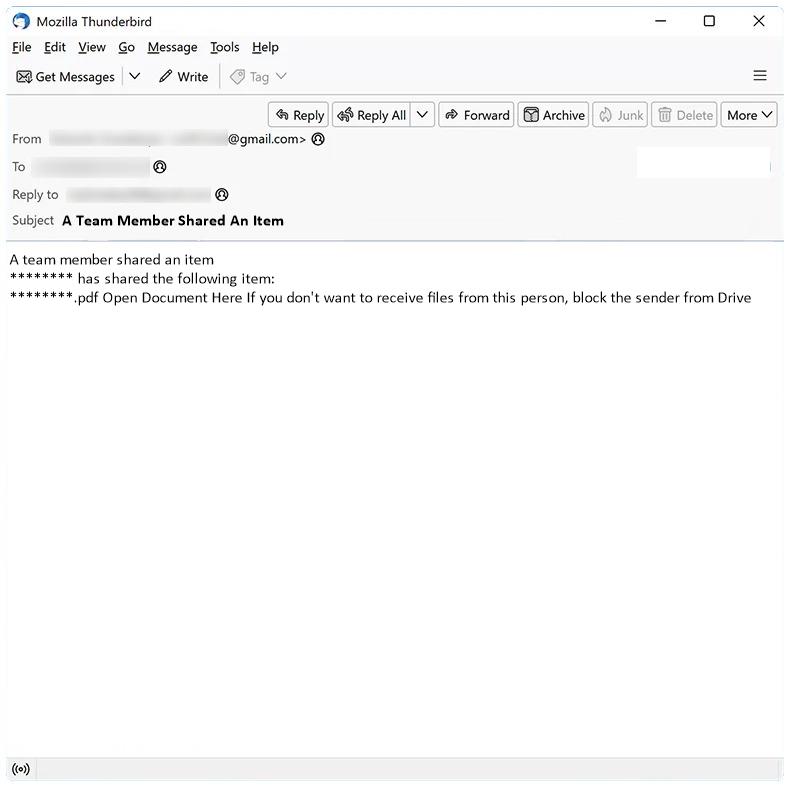
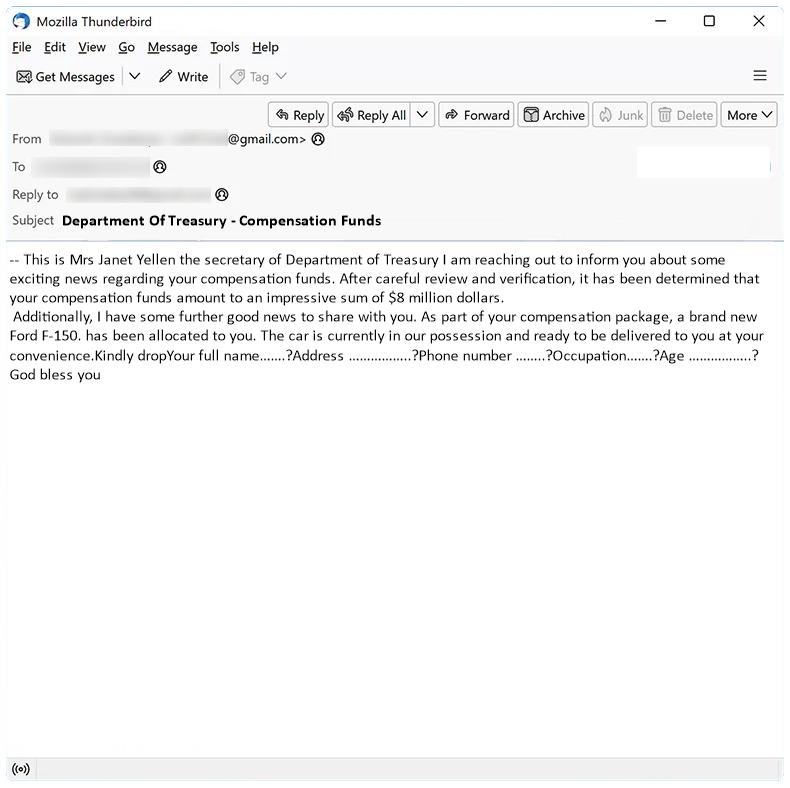
Sigrid Trust Rim Foundation email spam is a type of phishing scam where cybercriminals impersonate a legitimate organization in order to trick recipients into revealing sensitive information or sending money. These spam campaigns typically involve sending emails that claim the recipient has won a lottery or prize from the foundation, and instruct them to provide personal information or make a payment to claim their winnings.
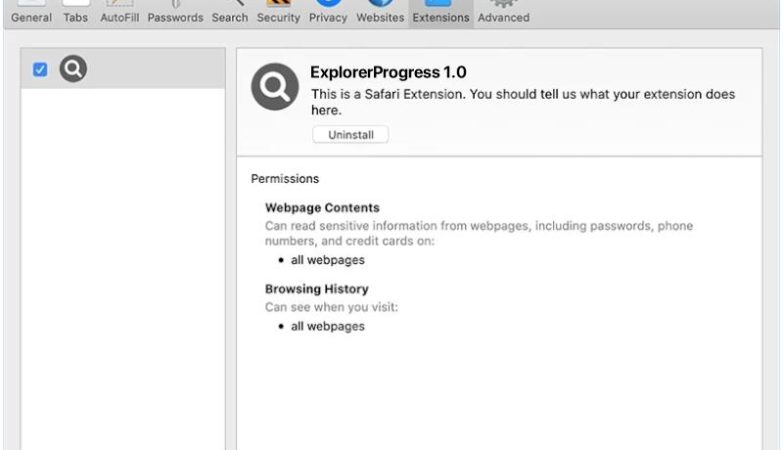
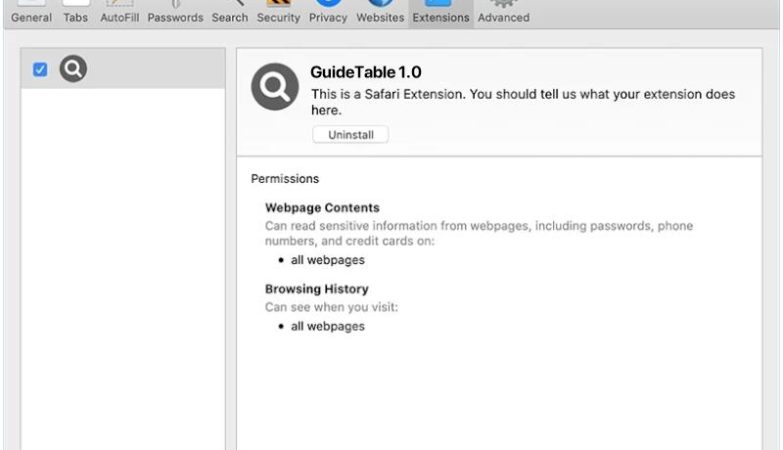
These spam campaigns can infect computers in a variety of ways, including through malicious attachments or links in the email that, when clicked, download malware onto the recipient’s device. This malware can then steal sensitive information, such as login credentials or financial data, and potentially cause other harm to the infected computer.
Interacting with Sigrid Trust Rim Foundation email scams can pose significant risks, including identity theft, financial loss, and damage to your computer or network. It is important to be cautious when receiving unsolicited emails claiming to be from a charitable organization or foundation, and to verify the legitimacy of any requests for personal information or payment before responding. Be sure to report any suspicious emails to your email provider and avoid clicking on any links or attachments in the email.