How to remove Predator The Cipher and decrypt .predator files
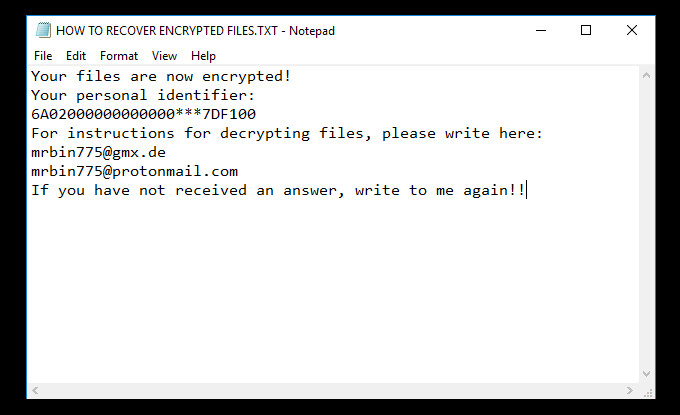
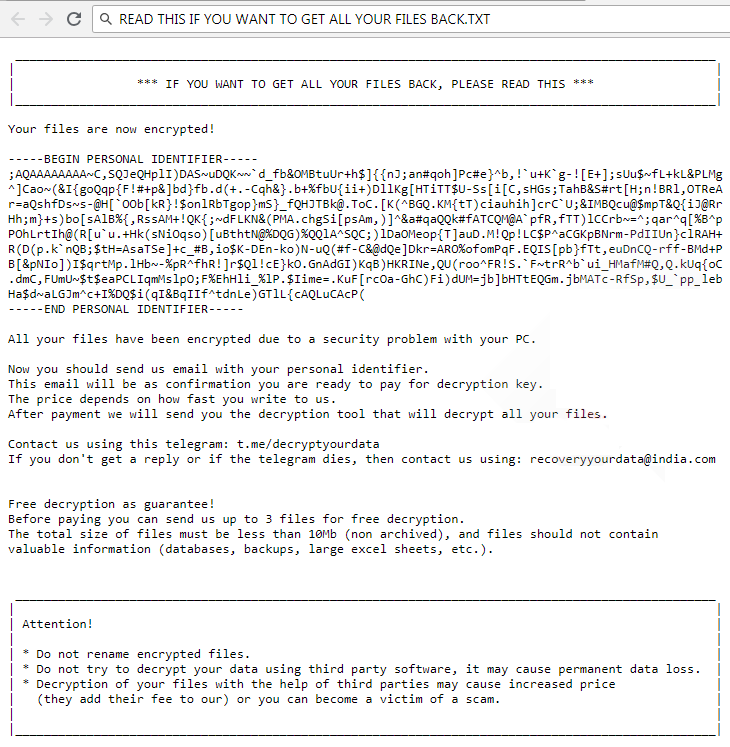
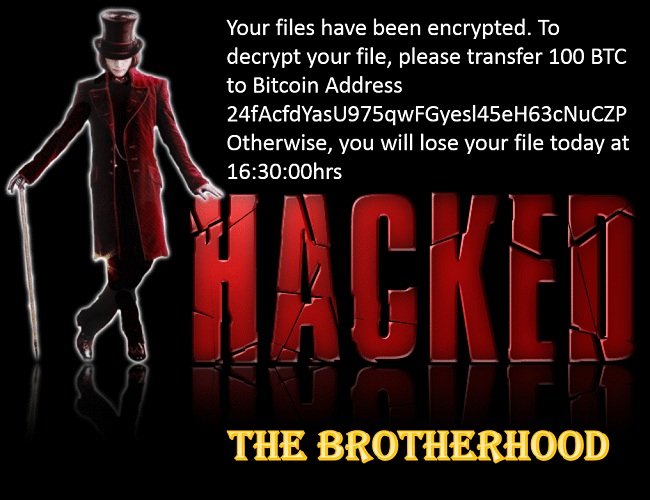
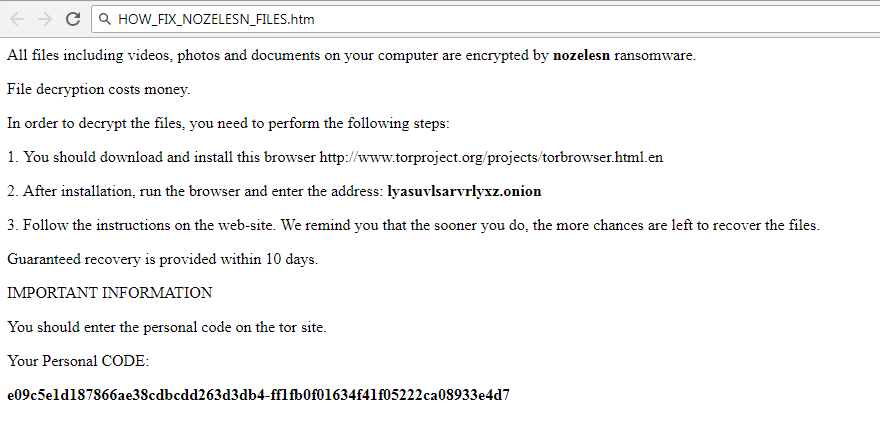
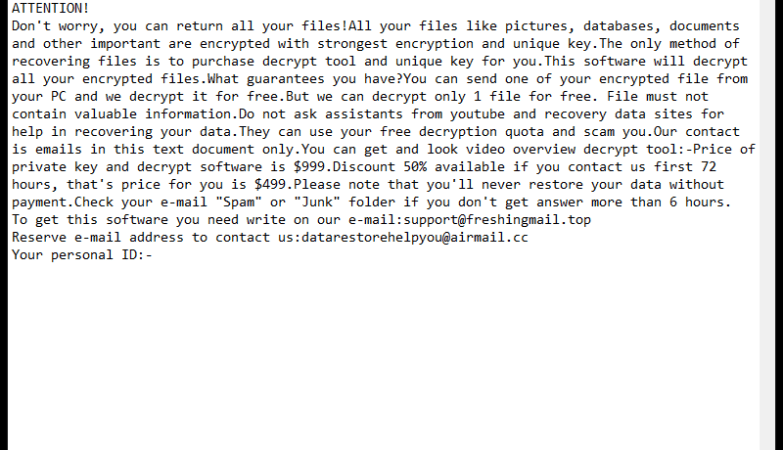
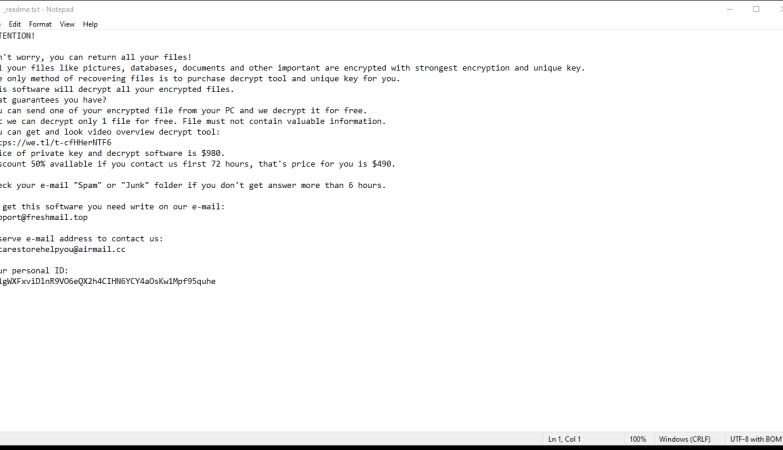
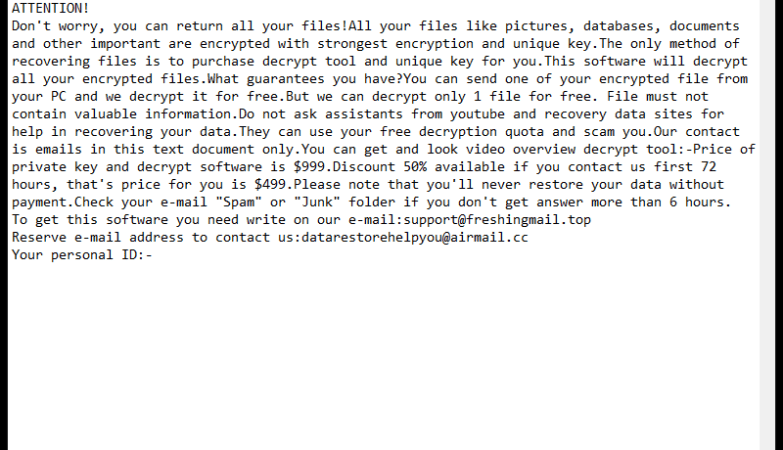
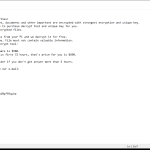
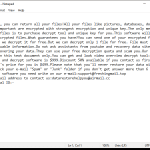
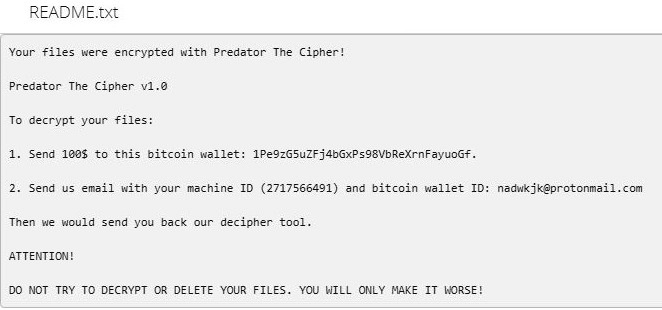
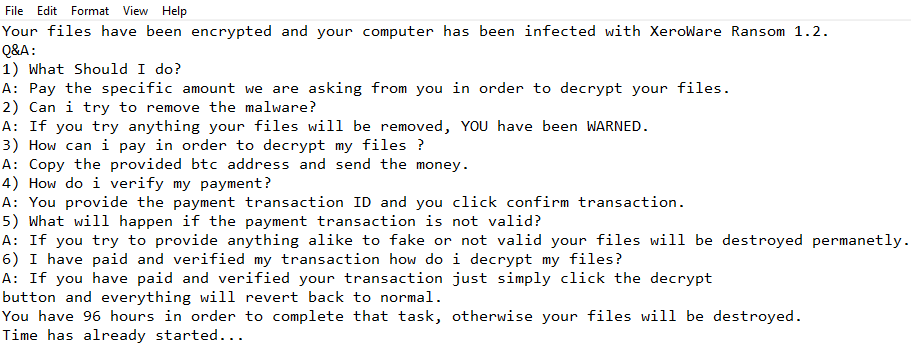
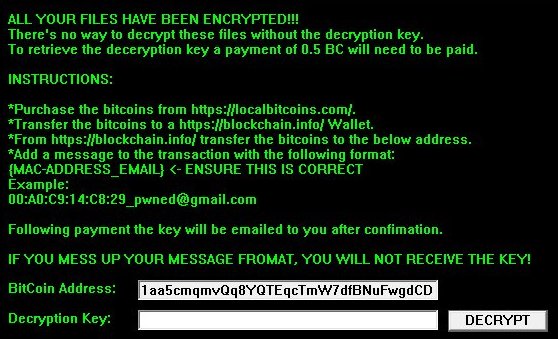
Predator The Cipher – is an encoder, that has been discovered in the beginning of July, 2018. The workflow of this crypto-virus is quite similar to other ransomware threats. First of all, it will try to find the way to sneak into a victim’s PC, it will use any unprotected connections and vulnerabilities of a system. Then, if it gets onto victim’s computer, it will immediately take control and start malicious processes, one of them is encryption procedure. Encrypting of infected files would not take much time. When the files are encoded they would not be accessible in any possible way. So, in order to be able to use infected files again, a victim need to pay money ransom, in this particular case it is 100$. We recommend you not to pay anything, as there are no guarantees of getting your files back. If you have this crypto-virus on your computer, use this guide to remove Predator The Cipher ransomware and restore .predator files without paying anything.






![How to remove Meduza ransomware and decrypt .[btc2018@tutanota.de].meduza files](https://malwarewarrior.com/wp-content/uploads/2018/07/MW-Meduza-ransomware.png)
![How to remove Everbe ransomware and decrypt .[eV3rbe@rape.lol].eV3rbe files](https://malwarewarrior.com/wp-content/uploads/2018/07/MW-Everbe-ransomware.png)