How to remove Moresearchhh.com
Moresearchhh.com is a type of adware that is designed to generate revenue for its developers through the display of unwanted advertisements on infected computers. Once installed, Moresearchhh.com will inject unwanted ads, pop-ups, and sponsored links into the user’s web browser, making it difficult to browse the internet without being bombarded with advertisements. This not only disrupts the user’s browsing experience but can also slow down the performance of the computer.
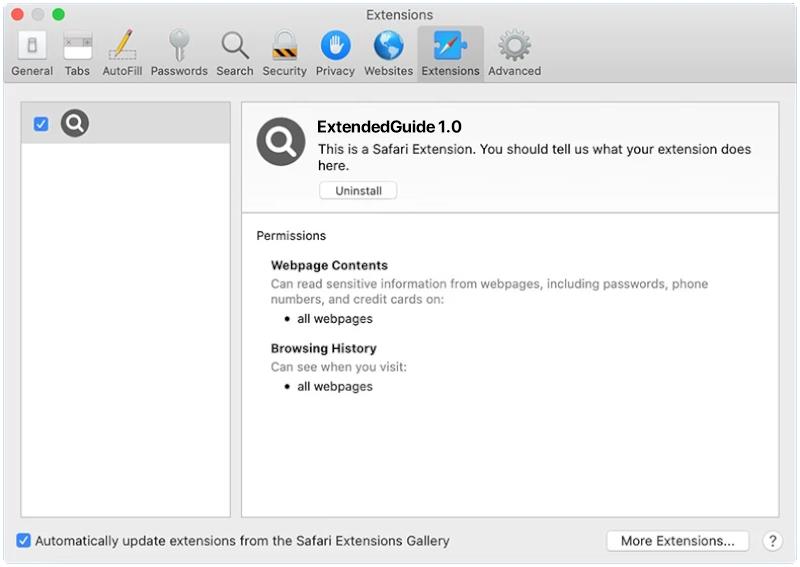
Moresearchhh.com typically infects computers and browsers through deceptive tactics such as bundling with freeware or shareware programs, fake software updates, or malicious websites. Users may unknowingly install Moresearchhh.com adware when downloading and installing free software from unreliable sources, or when clicking on malicious ads or links. Once installed, Moresearchhh.com will modify browser settings and track the user’s online activities in order to display targeted ads and generate revenue for its developers.