How to remove Yourshields24.club
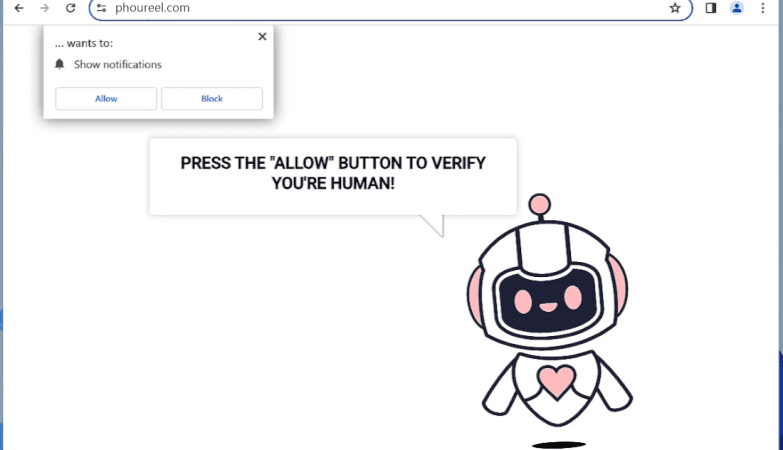
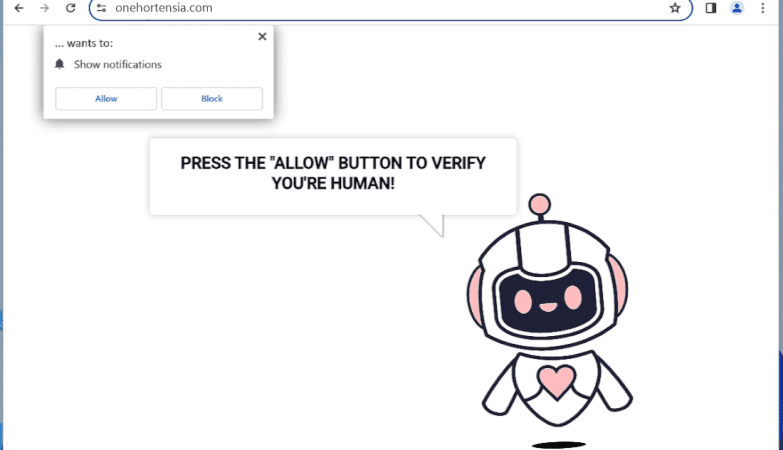
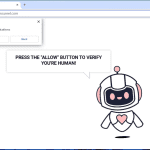
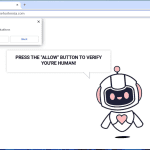
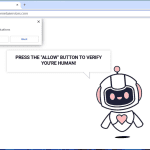
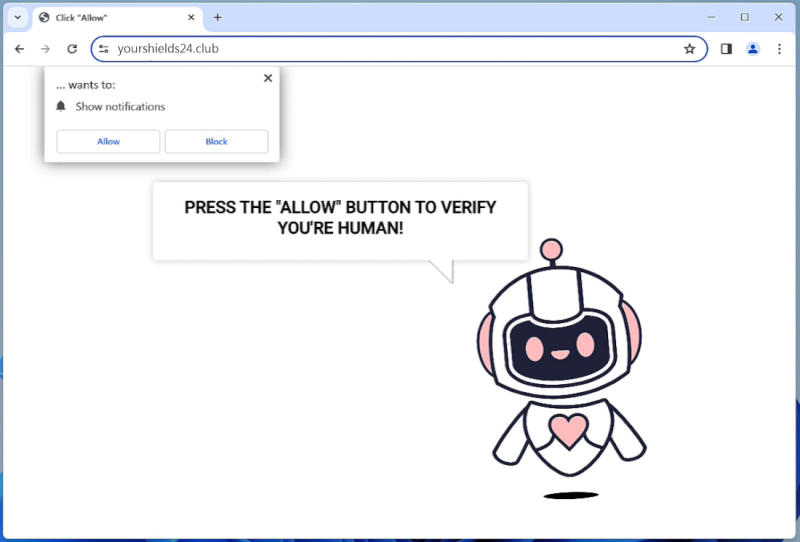
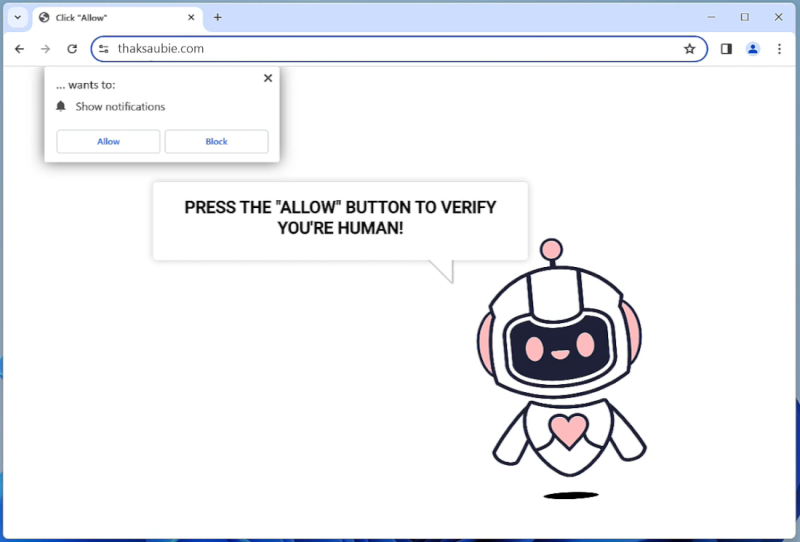
Yourshields24.club is a malicious website that infects computers by tricking users into allowing browser notifications. Once a user visits the website, they are prompted with a message that claims they need to click “Allow” to access a certain page or download content. By clicking “Allow,” the user unknowingly gives permission for Yourshields24.club to send them malicious notifications.
Once the notifications are enabled, Yourshields24.club can exploit them to display unwanted advertisements, pop-ups, and other harmful content on the user’s browser. This can lead to a poor browsing experience, as well as potential security risks such as malware infections. Yourshields24.club is known to target a wide range of browsers, including Google Chrome, Mozilla Firefox, and Safari, as well as various devices such as laptops, desktops, and mobile phones. Users should be cautious when encountering suspicious websites like Yourshields24.club and avoid clicking on any prompts or allowing notifications without verifying the legitimacy of the site.