How to remove Myholobods.com
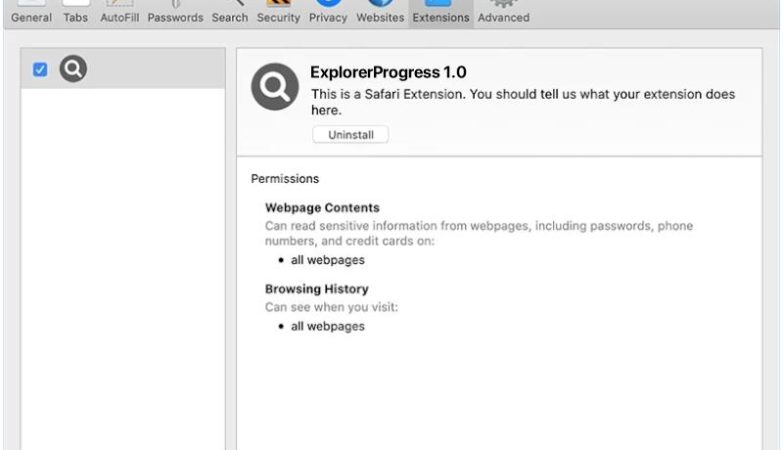
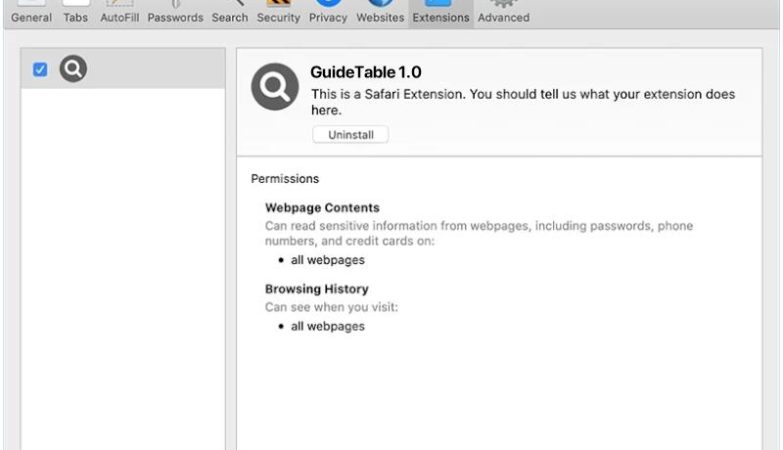
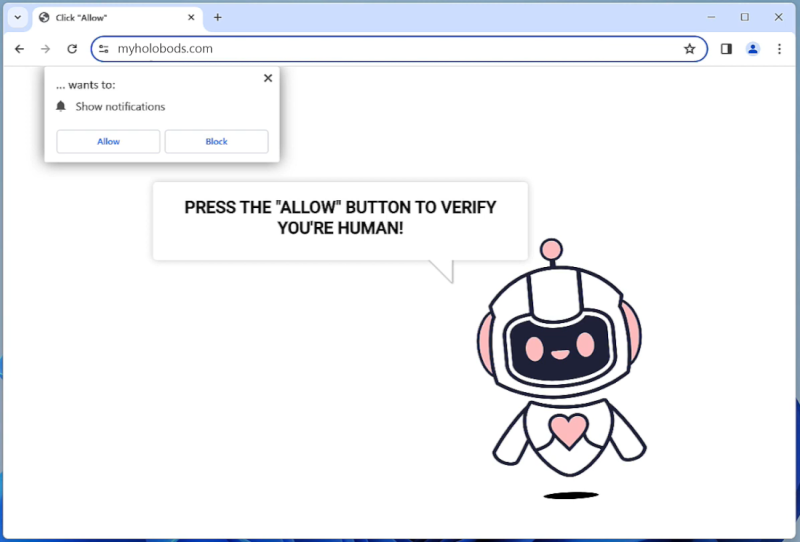
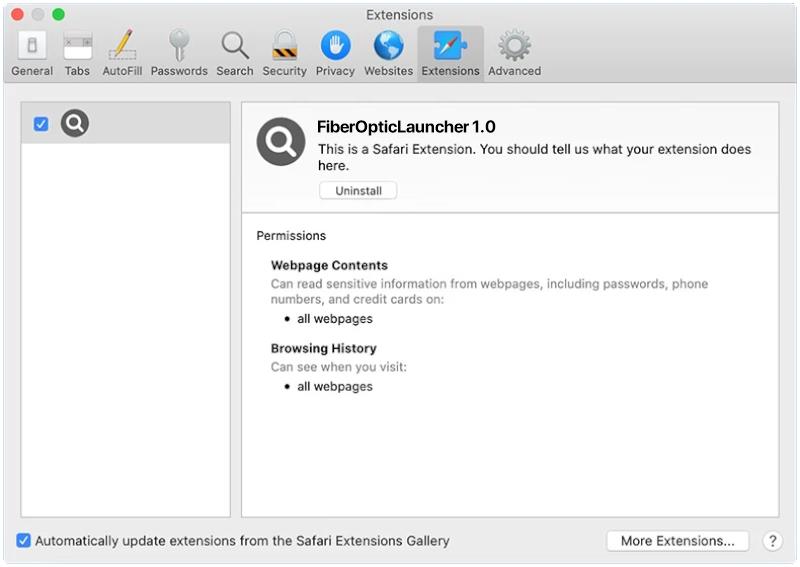
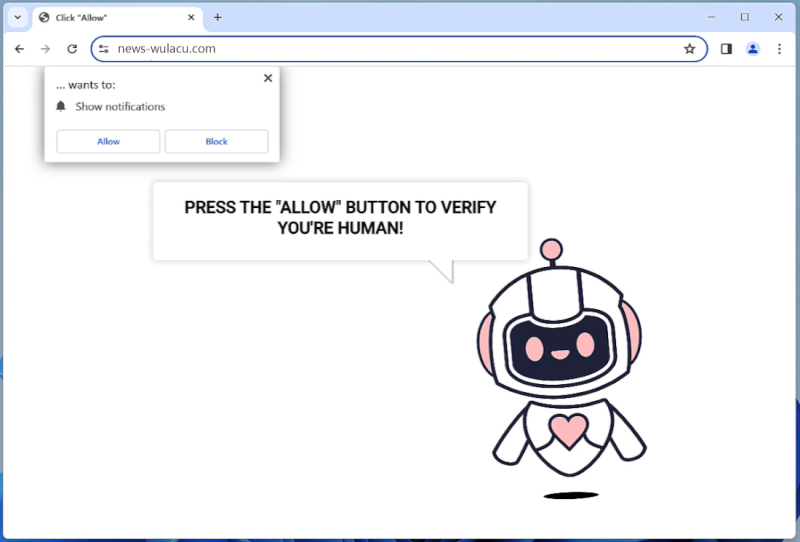
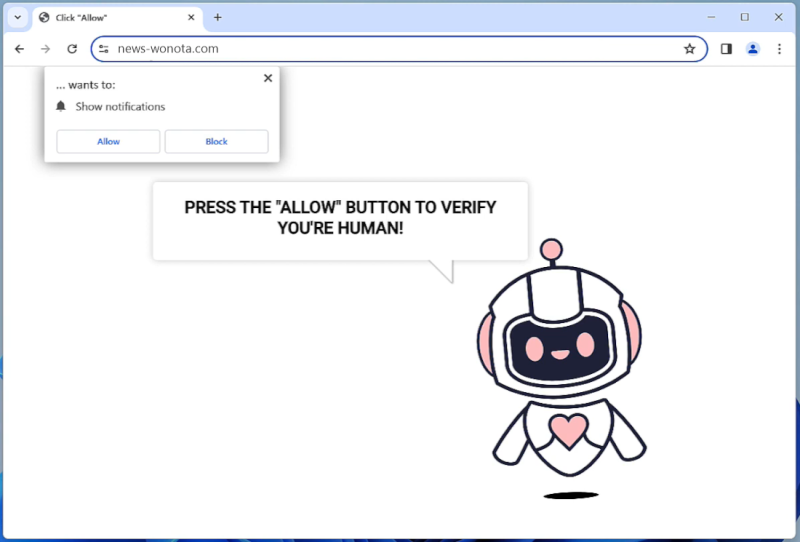
Myholobods.com is a malicious website that infects computers by tricking users into allowing browser notifications. Once a user visits the site, they may be prompted with a pop-up message asking to enable notifications in order to access content or continue browsing. If the user agrees, Myholobods.com will start sending unwanted and potentially harmful notifications to the user’s desktop or mobile device.
By exploiting browser notifications, Myholobods.com can bombard users with advertisements, fake alerts, and malicious links. These notifications can be difficult to remove and may lead to further malware infections or privacy breaches. Myholobods.com is known to target a wide range of browsers, including Google Chrome, Mozilla Firefox, and Safari, as well as various devices such as desktop computers, laptops, and smartphones. Users should be cautious when encountering pop-ups or notifications from unfamiliar websites and avoid enabling notifications from sites like Myholobods.com to protect their devices from potential harm.