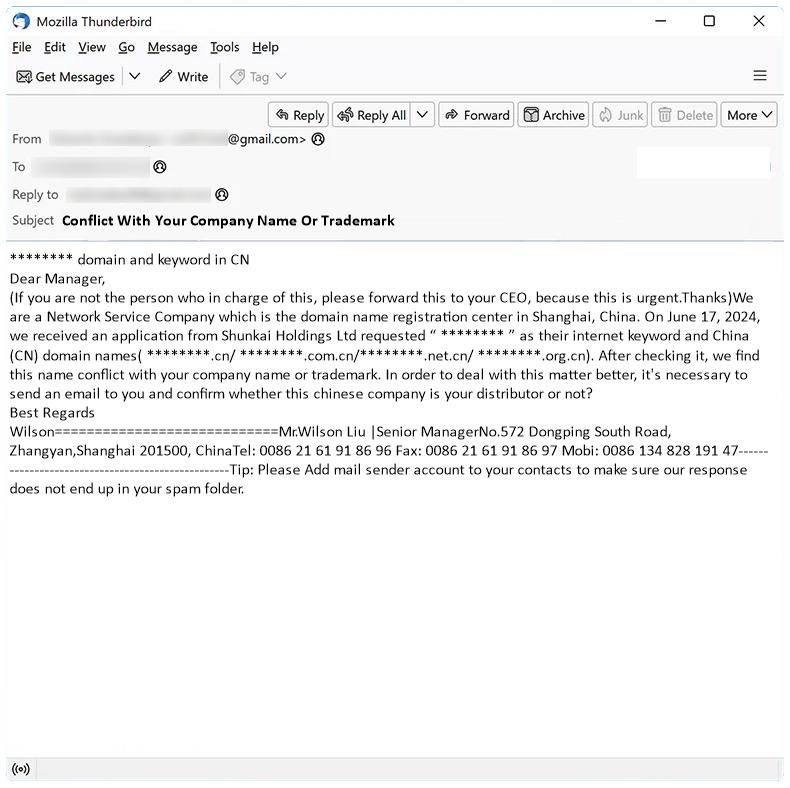
How to stop Conflict With Your Company Name Or Trademark email scam
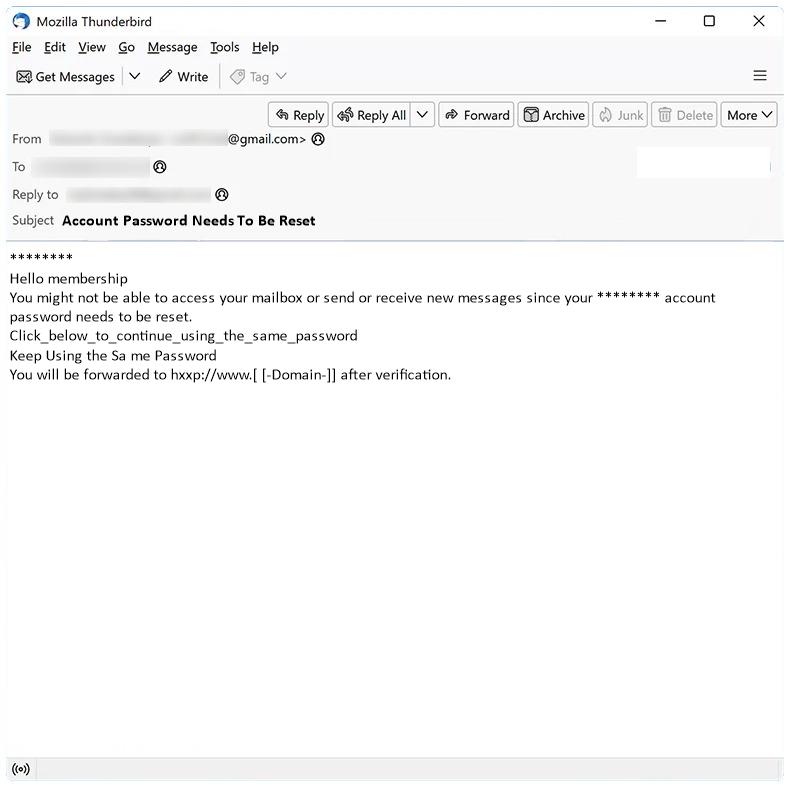
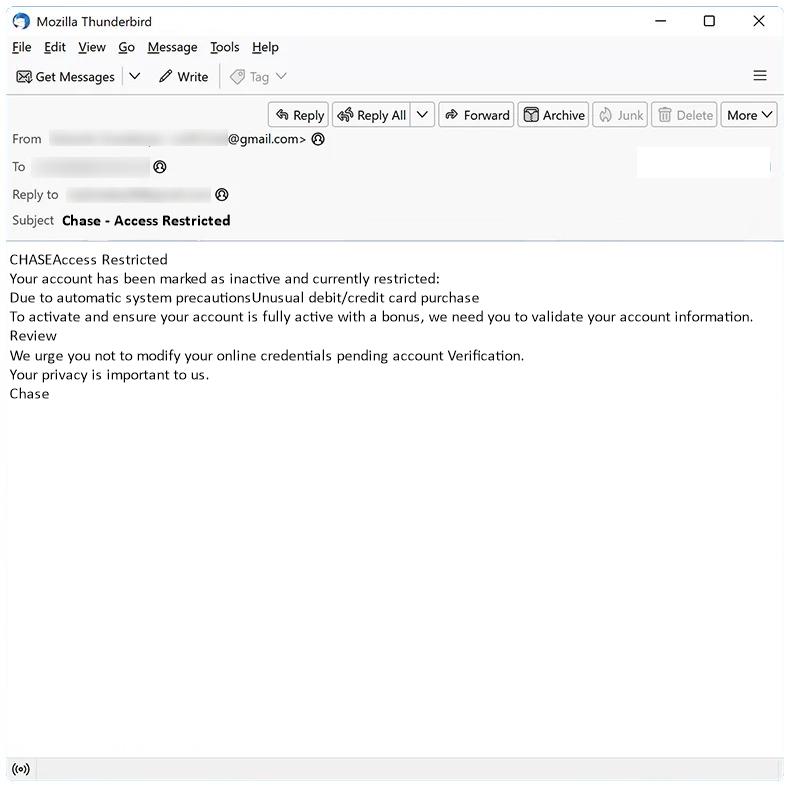
Conflict With Your Company Name Or Trademark email spam is a type of scam where cybercriminals send emails claiming that your company name or trademark is in conflict with another entity, and that legal action may be taken if not resolved. These emails often contain threats and demands for payment to avoid legal consequences.
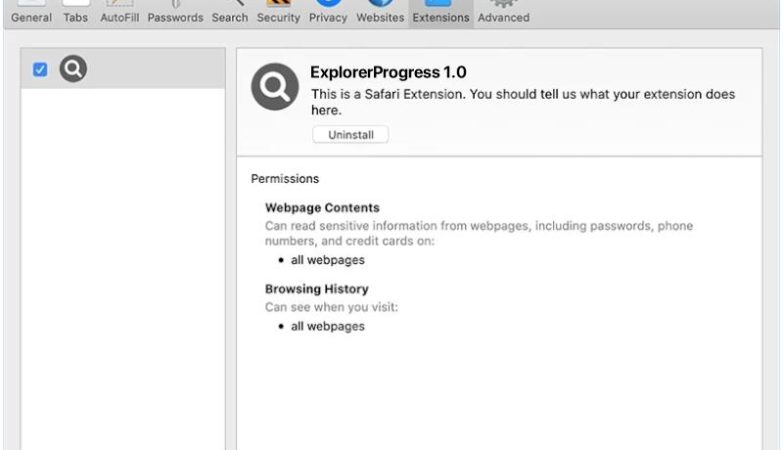
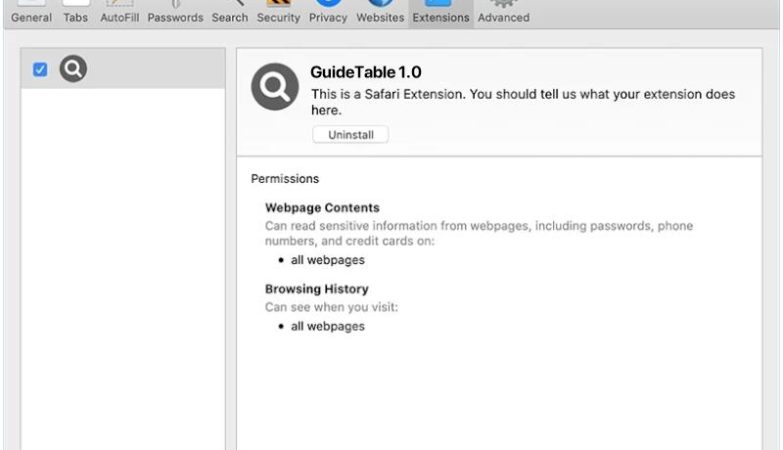
These spam campaigns can infect computers by tricking users into clicking on malicious links or attachments in the email, leading to malware installation or phishing attacks. Interacting with Conflict With Your Company Name Or Trademark email scams can pose several risks, including financial loss from fraudulent payments, compromise of sensitive information, and damage to your company’s reputation.
It is important to be cautious when receiving such emails and to verify the legitimacy of the claims before taking any action. It is recommended to report any suspicious emails to your IT department or cybersecurity provider for further investigation.