How to remove Osloader.Exe Trojan
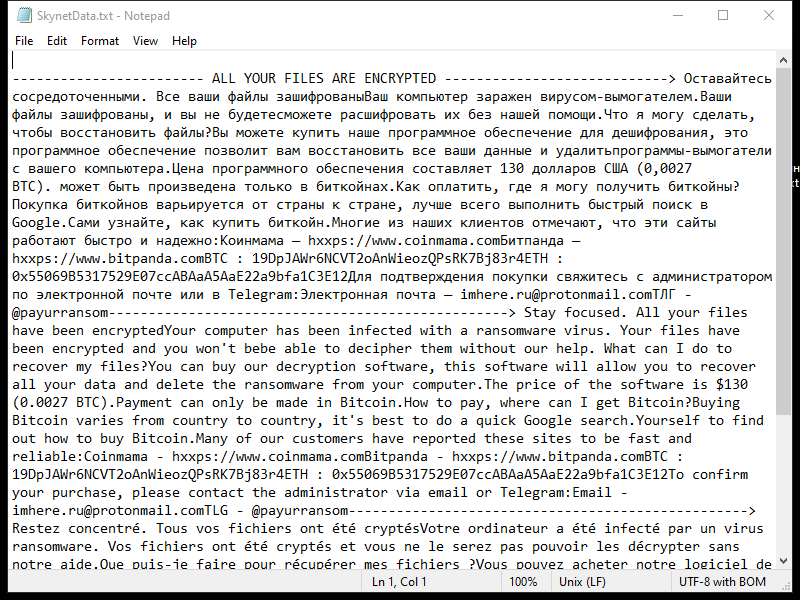
Osloader.Exe Trojan is a type of malicious software that disguises itself as a legitimate system file to infect computers. Once installed, the Trojan can perform various harmful activities, such as stealing sensitive information, corrupting files, and giving remote access to cybercriminals.
Osloader.Exe Trojan can infect computers through various means, including email attachments, malicious websites, software downloads, and removable storage devices. It can also spread through network vulnerabilities and exploit outdated software or operating systems.
To protect your computer from Osloader.Exe Trojan and other malware, it is important to use reliable antivirus software, keep your operating system and software up to date, avoid clicking on suspicious links or downloading unknown files, and practice safe browsing habits.




![How to remove Win32:Acecrypter-D [Cryp]](https://malwarewarrior.com/wp-content/uploads/2024/03/win32-acecrypter-d-cryp--1170x669.png)