How to remove Gohint.xyz
Gohint.xyz is a malicious website that is known to infect computers and exploit browser notifications. It is categorized as adware or potentially unwanted program (PUP) and is typically spread through deceptive techniques. Users may unknowingly visit the website by clicking on malicious ads, downloading infected software bundles, or visiting compromised websites.
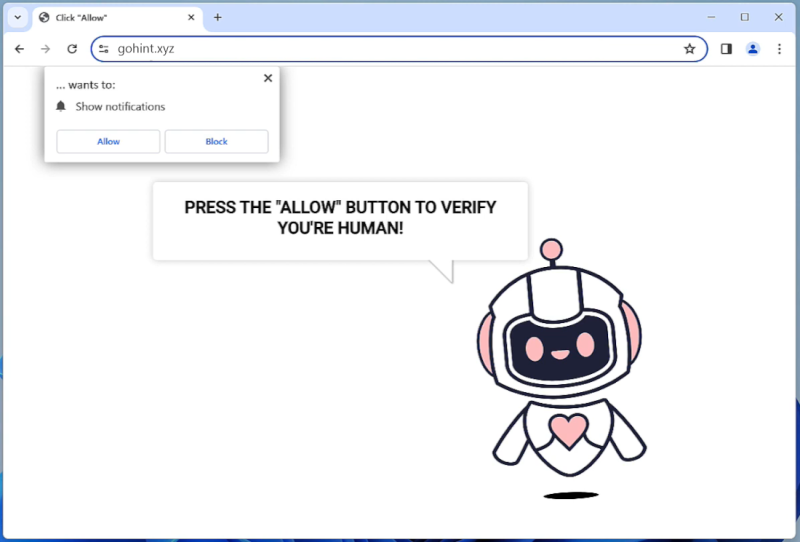
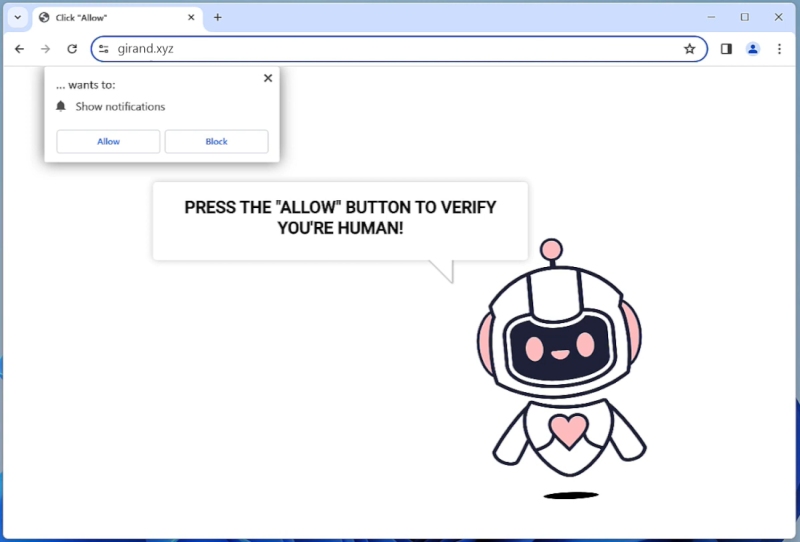
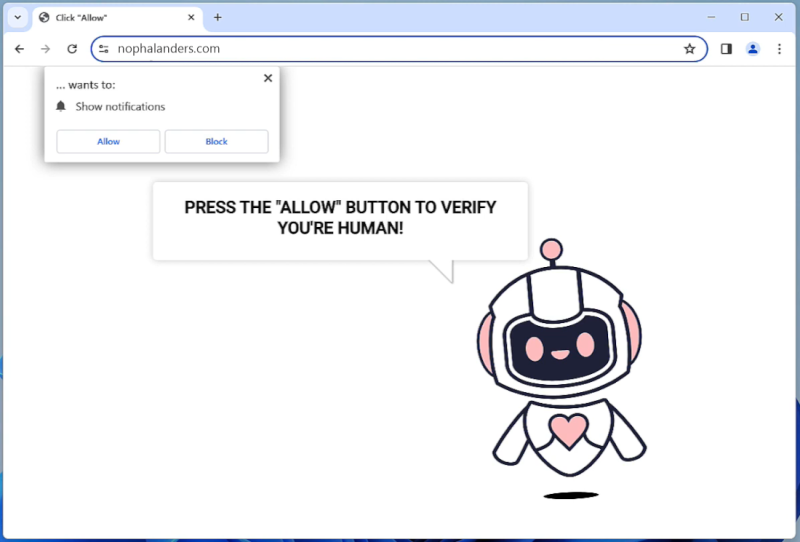
Once a user lands on Gohint.xyz, the website attempts to trick them into subscribing to its push notifications. It employs various social engineering tactics, such as disguising the notification prompt as a necessary step to access content or claiming that it is required to verify that the user is not a robot. If the user falls for the trick and accepts the notifications, Gohint.xyz gains the ability to display intrusive and unwanted advertisements directly on the user’s desktop, even when the browser is closed.
Gohint.xyz can target various web browsers, including popular ones like Google Chrome, Mozilla Firefox, and Microsoft Edge. It can infect both Windows and Mac devices, making it a threat to a wide range of users. To protect against such infections, it is crucial to exercise caution while browsing the internet, avoid clicking on suspicious ads or downloading software from untrusted sources, and regularly update antivirus software to detect and remove potential threats.