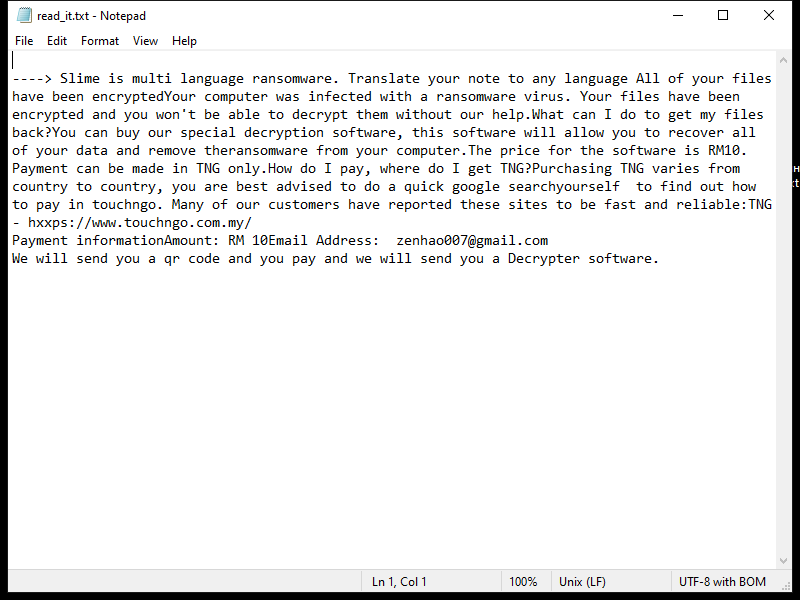
Slime Ransomware is a type of malicious software that encrypts files on a victim’s computer, rendering them inaccessible until a ransom is paid to the attackers. Here are the details you requested without any links or references:
1. Infection Method: Slime Ransomware typically spreads through malicious email attachments, fake software updates, infected downloads, or by exploiting vulnerabilities in outdated software.
2. File Extensions: Slime Ransomware adds the “.slime” extension to the encrypted files. For example, a file named “document.docx” would become “document.docx.slime” after encryption.
3. File Encryption: Slime Ransomware uses a strong encryption algorithm to lock files, making them impossible to open without the decryption key held by the attackers. The specific encryption method used by Slime Ransomware may vary across different versions or variants.
4. Ransom Note: After encrypting the files, Slime Ransomware creates a ransom note that typically contains instructions on how to pay the ransom and regain access to the encrypted data. The ransom note is often placed on the desktop or in various folders within the compromised system.
5. Decryption Tools: At the time of writing, there are no known decryption tools that can decrypt files encrypted by Slime Ransomware without paying the ransom. It is not recommended to contact or pay the attackers as it encourages further criminal activities.
6. Decrypting .slime Files: Since there are no decryption tools available, the best course of action is to restore the affected files from a backup if you have one. Regularly backing up important files is crucial to mitigate the impact of ransomware attacks. If you don’t have a backup, it might not be possible to decrypt the files without the decryption key held by the attackers.
It is important to note that dealing with ransomware should be done with caution, and seeking professional help from cybersecurity experts or law enforcement agencies is advisable.