2700 Ransomware is a type of malware that is part of the Stop/Djvu ransomware family. It’s named after the “.2700” extension it adds to the end of infected files. Once it infects a computer, it encrypts files making them inaccessible to the users and demands a ransom to get them decrypted.
Infection Method:
The most common ways that 2700 Ransomware infects computers are through phishing emails, malicious downloads, or by exploiting vulnerabilities in a computer’s operating system or software.
File Extension:
2700 Ransomware adds the “.2700” extension to all encrypted files. For example, a file originally named “example.jpg” would be renamed to “example.jpg.2700” after encryption.
Encryption:
The 2700 Ransomware typically uses a combination of AES and RSA encryption algorithms to lock the files. This makes the files inaccessible without the unique decryption key.
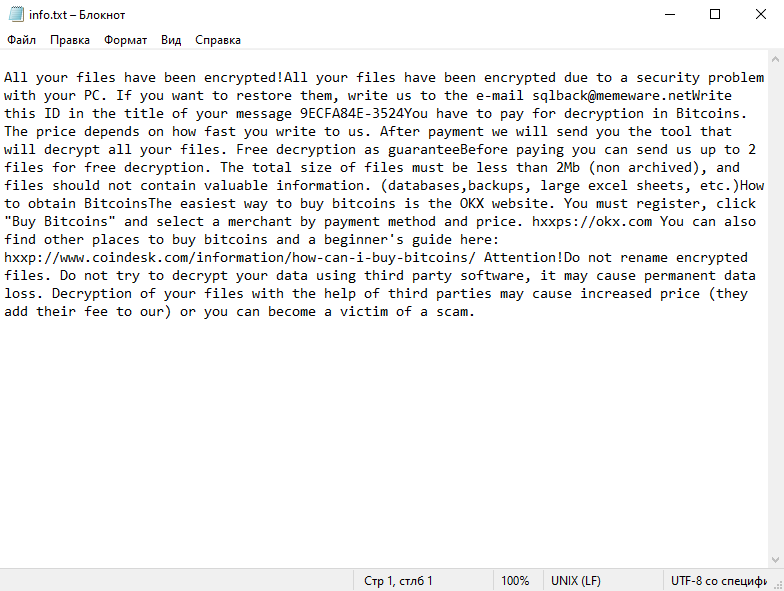
Ransom Note:
The ransom note is usually created in a text file named “_readme.txt” and is typically located in every folder that contains encrypted files. The note informs the victim about the encryption and demands a ransom, usually in Bitcoin, for the decryption key.
Decryption Tools:
Unfortunately, as of now, there is no known free decryption tool specifically for the 2700 Ransomware. Researchers are continuously working on developing decryption tools for various ransomware strains, but these tools often take time.
How to Decrypt .2700 Files:
If you’ve been infected with 2700 Ransomware, you should first remove the malware from your system using a reliable anti-malware program to prevent further file encryption. After that, if you have a recent backup of your files, you can restore them. If you don’t have a backup, you may have to wait until a free decryption tool becomes available. In some cases, you might be able to recover some files using data recovery software, but this method is not always successful and can sometimes lead to loss of data. You should never pay the ransom as this does not guarantee that your files will be decrypted and it only encourages the cybercriminals.