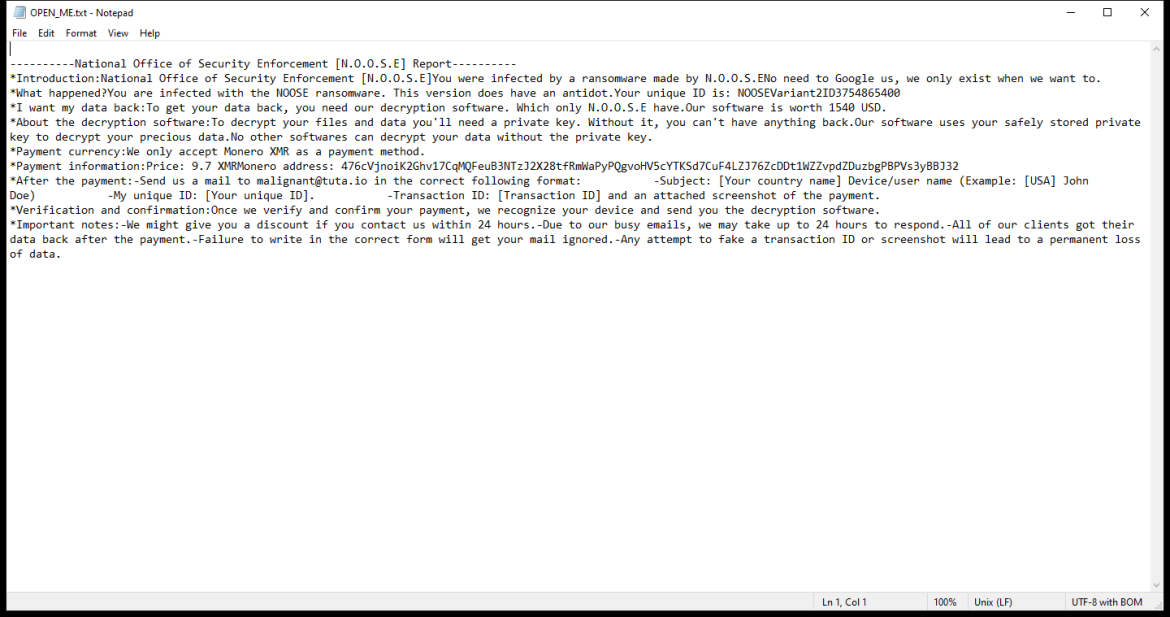
NOOSE Ransomware is a type of malicious software that encrypts files on a victim’s computer and demands a ransom for their release. Here is some information about it:
1. Infection: NOOSE Ransomware typically infects computers through methods like phishing emails, malicious downloads, exploit kits, or by exploiting software vulnerabilities.
2. File Extensions: NOOSE Ransomware appends the extension “.noose” to encrypted files. For example, a file originally named “document.docx” would become “document.docx.noose” after encryption.
3. Encryption: NOOSE Ransomware uses a strong encryption algorithm (usually AES or RSA) to lock the victim’s files. This encryption makes the files inaccessible without the decryption key.
4. Ransom Note: After encrypting the files, NOOSE Ransomware creates a ransom note that typically contains instructions on how to pay the ransom. The note may be in the form of a text file, a pop-up window, or a wallpaper change.
5. Decryption Tools: At the time of writing, there are no known decryption tools available for NOOSE Ransomware. It’s always recommended to avoid paying the ransom, as there’s no guarantee the attackers will provide the decryption key or fully restore the files even if the payment is made.
6. Decryption of .noose Files: Without a decryption tool, decrypting .noose files is extremely difficult, if not impossible. The best course of action is to restore the files from a backup if one exists. Additionally, you can seek assistance from a professional cybersecurity firm or law enforcement agencies who may be able to provide guidance or solutions.
Please note that the information provided is based on general knowledge about ransomware in the public domain, and specific details about NOOSE Ransomware may vary. It’s always important to stay vigilant, keep backups of your important files, and employ robust cybersecurity measures to prevent ransomware infections.