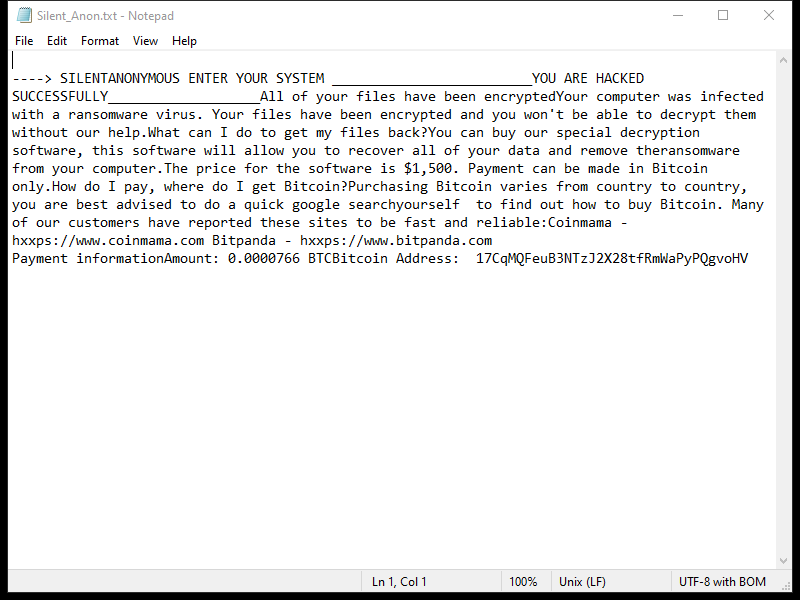
SilentAnonymous Ransomware, also known as SilentAttack, is a type of malicious software that infects computers and encrypts files, rendering them inaccessible to the user. Here is some information about the ransomware:
1. Infection: SilentAnonymous Ransomware typically spreads through various methods such as malicious email attachments, software vulnerabilities, fake software updates, or through compromised websites.
2. File Extensions: When the ransomware infects a computer, it adds the “.silentattack” extension to the encrypted files. For example, a file named “example.jpg” would become “example.jpg.silentattack”.
3. Encryption: SilentAnonymous Ransomware employs strong encryption algorithms like AES or RSA to encrypt the victim’s files. These encryption algorithms ensure that the files cannot be easily decrypted without the private encryption key.
4. Ransom Note: After encrypting the files, the ransomware creates a ransom note that usually contains instructions on how to pay the ransom and obtain the decryption key. The note can be found in various locations such as desktop, folders with encrypted files, or in text files scattered across the system.
5. Decryption Tools: As of now, there are no known decryption tools available to decrypt SilentAnonymous Ransomware-encrypted files. It is important to note that paying the ransom does not guarantee the recovery of your files, and it may encourage further criminal activities.
6. Decryption of .silentattack Files: Since there are no decryption tools available, the primary methods to potentially recover your files are restoring from a backup (if available) or seeking professional help from cybersecurity experts who may have advanced techniques to recover encrypted data.
It is crucial to maintain regular backups of important files, keep your operating system and software up to date, and exercise caution while opening email attachments or downloading files from untrusted sources to protect your system from ransomware attacks.